Windows Feature Hunter (WFH)
Windows Feature Hunter (WFH) is a proof of concept python script that uses Frida, a dynamic instrumentation toolkit, to assist in potentially identifying common “vulnerabilities” or “features” within Windows executables. WFH currently has the capability to automatically identify potential Dynamic Linked Library (DLL) sideloading and Component Object Model (COM) hijacking opportunities at scale.
DLL sideloading utilizes the Windows side-by-side (WinSXS) assembly to load a malicious DLL from the side-by-side (SXS) listing. COM hijacking allows an adversary to insert malicious code that can be executed in place of legitimate software through hijacking the COM references and relationships. WFH will print the potential vulnerabilities and write a CSV file containing the potential vulnerabilities in the target Windows executables.
Install
git clone https://github.com/ConsciousHacker/WFH.git
cd WFH
pip install -r requirements.txt
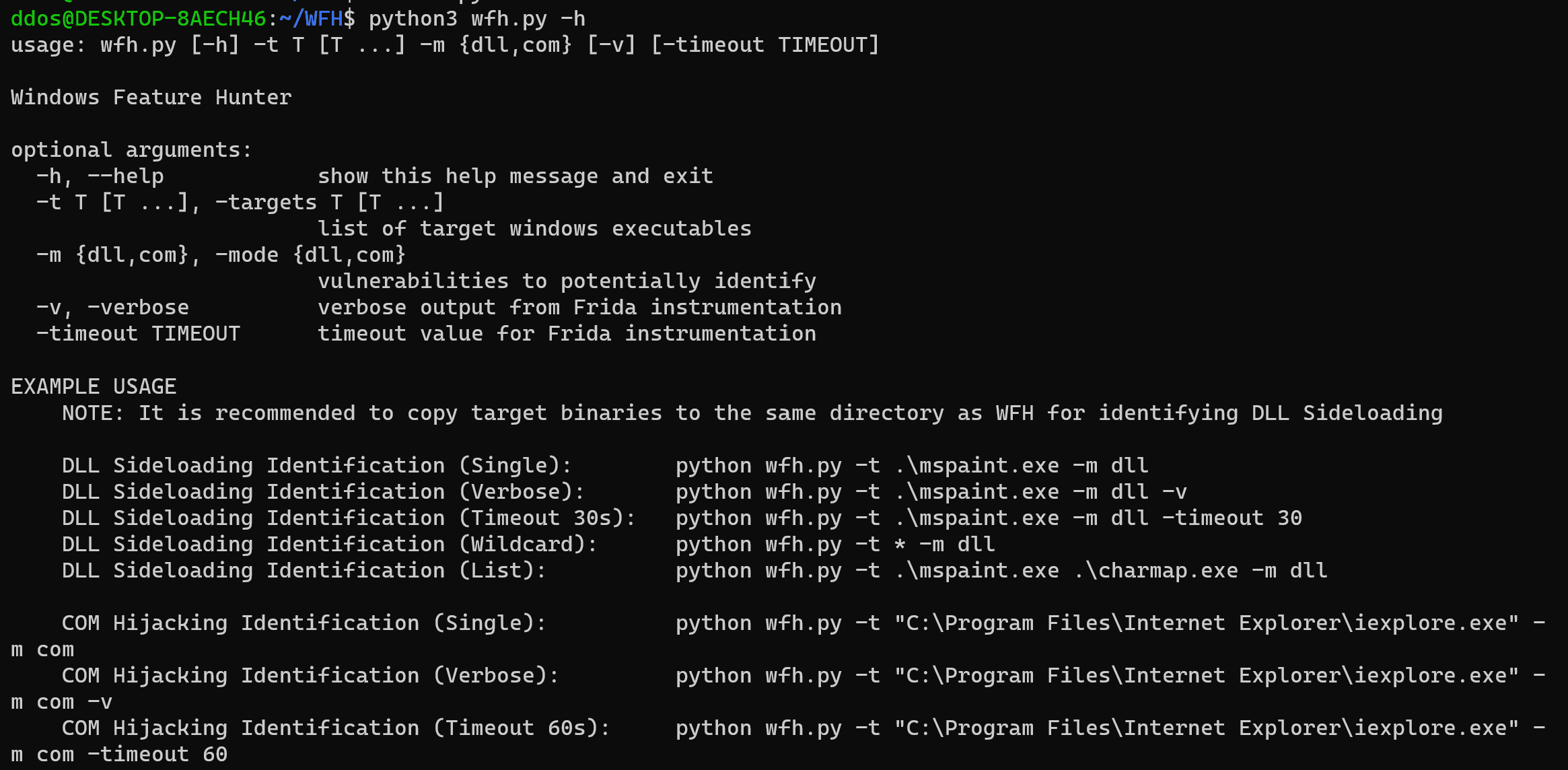
Use
Example
DLL Sideloading Identification
First, you need to copy the binaries you want to analyze to the same directory as wfh
Now you can run wfh against the binaries to identify dll sideloading opportunities
If you prefer more verbose output, you can use “-v” to see every message from Frida instrumenting the Windows API calls. You can also view this output in the raw log file.
COM Hijacking Identification
Use Cases
Native Windows Signed Binaries
Copy all native Windows signed binaries to the wfh directory
Get-ChildItem c:\ -File | ForEach-Object { if($_ -match ‘.+?exe$’) {Get-AuthenticodeSignature $_.fullname} } | where {$_.IsOSBinary} | ForEach-Object {Copy-Item $_.path . }
Hunt for DLL sideloading opportunities
python wfh.py -t * -m dll
Hunt for COM hijacking opportunities
python wfh.py -t * -m com