Windows Oracle Database Attack Tool (wodat)
Simple port of the popular Oracle Database Attack Tool (ODAT) to C# .Net Framework.
- Perform password-based attacks e.g. username as password, username list against given password, password list against given username, username:pass combolist.
- Test if a credential/connection string is working against the target
- Brute force attacks to discover valid SID/ServiceNames
- Perform discovery of valid TNS listeners against provided target file or CIDR range
- More to come, I hope!
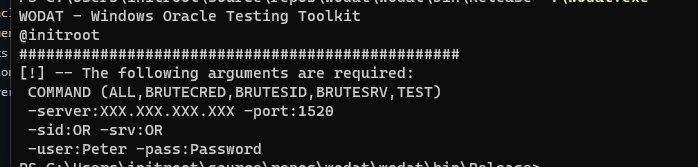
Modules
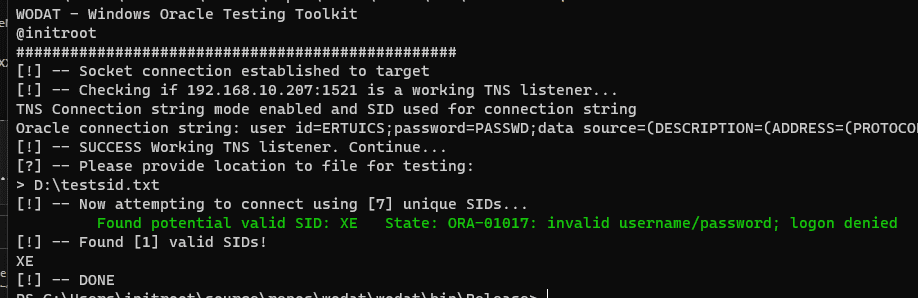
BRUTESID
The module performs wordlist SID guessing attack if not successful will ask for brute force attack.
wodat.exe BRUTESID -server:XXX.XXX.XXX.XXX -port:1521
BRUTESRV
The module performs a wordlist ServiceName guessing attack if not successful will ask for a brute force attack.
wodat.exe BRUTESRV -server:XXX.XXX.XXX.XXX -port:1521
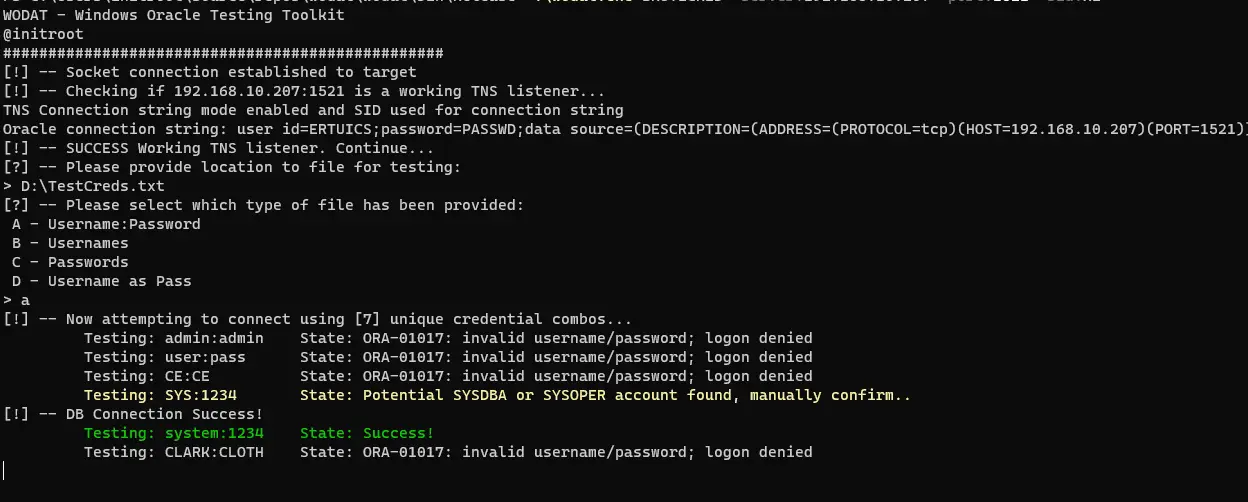
BRUTECRED
The module performs wordlist password-based attack. The following options exist:
A – username:password combolist with no credentials given during arguments
B – username list with password given in arguments
C – password list with username given in arguments
D – username as password with username list provided
To perform a basic attack with a given file that has username:password combos.
wodat.exe BRUTECRED -server:XXX.XXX.XXX.XXX -port:1521 -sid:XE

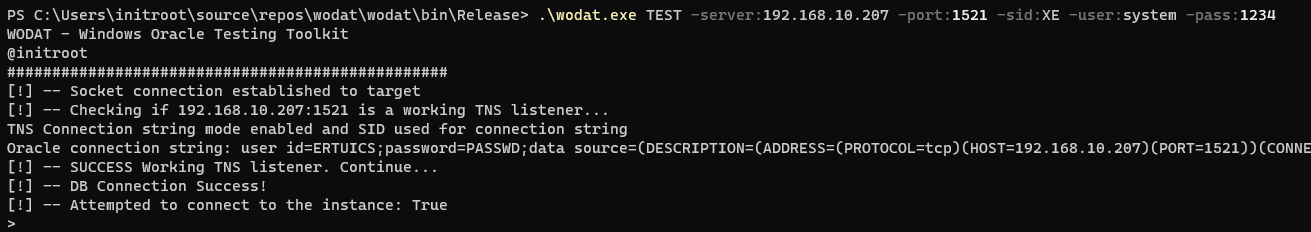
TEST
Module tests if the given connection string can connect successfully.
wodat.exe TEST -server:XXX.XXX.XXX.XXX -port:1521 -sid:XE -user:peter -pass:pan
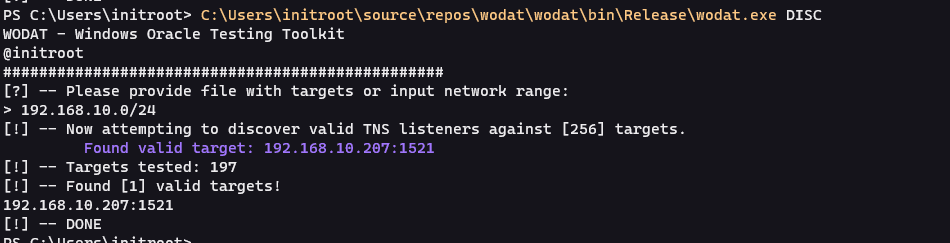
DISC
The module will perform discovery against provided CIDR range or file with instances. Note, that only instances with valid TNS listeners will be returned. Testing a network range will be much faster as it’s processed in parallel.
wodat.exe DISC
Instances to test must be formatted as per the below example targets.txt:
192.168.10.1
192.168.10.5,1521