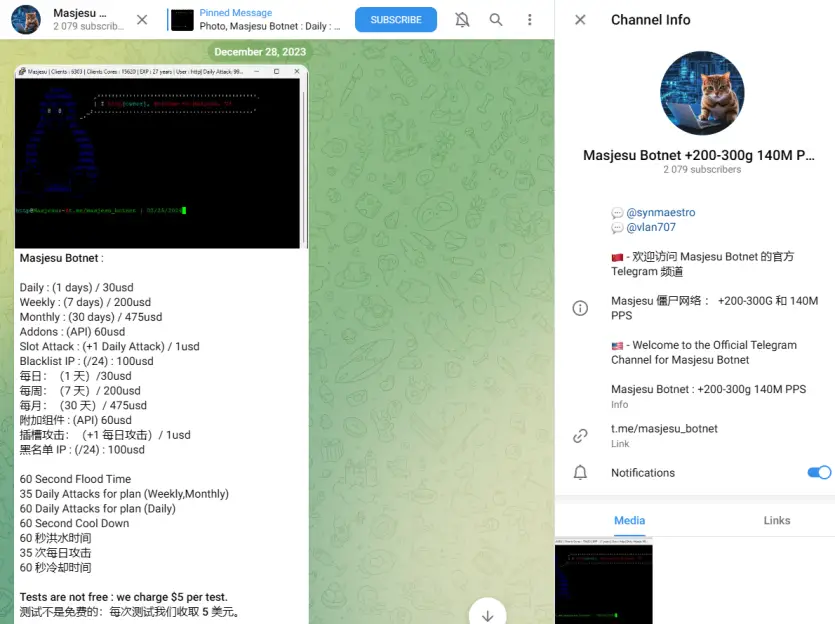
Masjesu’s Telegram Channel | Image: NSFOCUS
NSFOCUS has identified a resurgence of the XorBot botnet, a potent threat to Internet of Things (IoT) devices worldwide. First observed in late 2023, XorBot has evolved significantly, introducing advanced anti-detection mechanisms and a wider arsenal of exploits. The latest iteration, version 1.04, presents new challenges for cybersecurity defenders.
Since its debut, XorBot has shown a consistent ability to adapt and evade detection. “XorBot has become an undeniable security threat in the field of the Internet of Things (IoT),” NSFOCUS reports, with attackers targeting devices such as Intelbras cameras and routers from TP-Link and D-Link. The botnet now supports up to 12 exploit methods and has grown to control a substantial number of devices.
XorBot primarily propagates by exploiting vulnerabilities in IoT devices. Its latest version incorporates advanced techniques targeting vulnerabilities:
| Vulnerability | Target Devices |
| UPnP SOAP TelnetD Command Execution | D-Link devices |
| Netgear cgi-bin Command Injection | Netgear R7000/R6400 devices |
| CCTV/DVR Remote Code Execution | CCTVs, DVRs from over 70 vendors |
| HNAP SoapAction-Header Command Execution | D-Link devices |
| JAWS Webserver unauthenticated shell command execution | MVPower DVRs, among others |
| Netgear setup.cgi unauthenticated RCE | DGN1000 Netgear routers |
| Vacron NVR RCE | Vacron NVR devices |
| Eir WAN Side Remote Command Injection | Eir D1000 routers |
| CVE-2014-8361 | Different devices using the Realtek SDK with the miniigd daemon |
| CVE-2017-17215 | Huawei HG532 |
| GPON Exploit | GPON |
| CVE-2023-1389 | TP-Link |
After gaining access, the Trojan deposits itself in the /tmp directory of compromised devices, ensuring it remains concealed and resistant to external tampering.
The XorBot Trojan has undergone several iterations, with significant enhancements in each version. According to NSFOCUS:
- Early versions included five DDoS attack modes, while the latest version supports over ten, including UDP, TCP_SYN, and HTTP floods.
- The Trojan employs multi-round XOR encryption, similar to the Mirai botnet, and disguises itself as a legitimate system file (
ld-unix.so.2) to achieve persistence.
The botnet also monopolizes resources on infected devices, setting the /tmp directory to read-only, preventing other malware from compromising the same system.
XorBot operators have shifted their focus to profitability, openly advertising distributed denial-of-service (DDoS) attacks as a service under the alias “Masjesu Botnet.” Telegram has become a central platform for recruiting customers and promoting services, which NSFOCUS warns “lays a solid foundation for the subsequent expansion and development of the botnet.”
The botnet employs cutting-edge evasion strategies, including:
- Anti-Tracking Design: XorBot uses passive online methods, establishing connections with control servers without sending identifiable traffic. It waits for server instructions before responding with randomized data, complicating detection.
- Code Obfuscation: Redundant code and signature obfuscation make static analysis challenging.
- Communication Stealth: Unique communication interaction logic reduces the botnet’s visibility at the network level
XorBot’s rapid evolution and adoption of advanced techniques highlight the growing sophistication of IoT-targeted threats. As NSFOCUS emphasizes, “the controllers of the botnet are continuously increasing their investment in anti-detection and anti-tracking technologies,” making defense efforts more complex.
Related Posts:
- New APT Group ‘Actor240524’ Targets Azerbaijan and Israel with Advanced Tactics
- Redis Servers Exploited to Deploy Metasploit Meterpreter Backdoor
- North Korean Cyberattacks Persist: Developers Targeted via npm
- Netgear Patches Multiple Vulnerabilities in CAX30, XR1000, and R7000 Routers