
The Albabat ransomware group is evolving, signaling a potential expansion of its targets and a streamlined operational approach. Trend Micro’s research has uncovered new versions of the Albabat ransomware, indicating that the group may be broadening its focus from Windows to include Linux and macOS systems. This evolution poses a significant threat to enterprises, as a successful ransomware attack can lead to “reputational damage, operational disruption, and financial losses.”
The threat hunting team at Trend Micro recently encountered versions 2.0.0 and 2.5 of Albabat, which not only target Microsoft Windows but also gather system and hardware information on Linux and macOS. This discovery includes previously undetected variants of the Albabat ransomware.
A notable aspect of these new versions is the group’s utilization of GitHub to streamline their operations. These new versions retrieve their configuration data through the GitHub REST API, employing a “User-Agent” string labeled “Awesome App.” The configuration details provide key information about the ransomware’s behavior and operational parameters.
The configuration reveals that this version of Albabat ignores specific folders, such as “Searches, AppData, $RECYCLE.BIN,” and others. It also targets a range of file extensions for encryption and skips certain files. Additionally, the ransomware is designed to terminate specific processes.
The configuration details also provide insights into where the ransomware stores collected data from the victim’s machine, connecting to a PostgreSQL database. This collected information is valuable to the attackers for making ransom demands, monitoring infections, and potentially selling victims’ data.
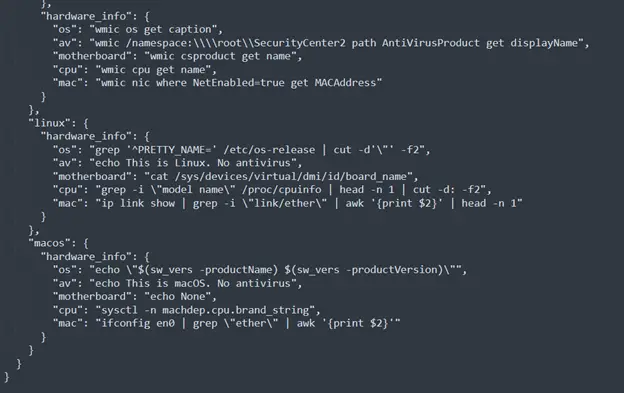
Furthermore, the configuration includes commands for Linux and macOS, indicating that binaries have been developed to target these platforms.
The GitHub repository used to store and deliver configuration files is billdev.github.io. Although the repository used by the ransomware is currently private, it remains accessible through an authentication token. The account associated with this activity is registered under the name “Bill Borguiann,” which is likely a pseudonym.
The commit history reveals ongoing active development, with the user primarily modifying the configuration code. A folder named 2.5.x within the private repository suggests a newer version of the ransomware is in development. This directory contains a config.json file for version 2.5 of the ransomware, which includes newly added cryptocurrency wallets.
To defend against ransomware threats like Albabat, organizations should prioritize proactive cybersecurity measures. This includes:
- Regular backups: Maintain up-to-date, secure backups of all critical data and regularly test restoration processes.
- Network segmentation: Implement network segmentation to limit the spread of ransomware.
- Patch and update systems: Regularly update and patch software and operating systems to close vulnerabilities.
- User training and awareness: Conduct regular training sessions for employees to recognize phishing attempts and suspicious links.