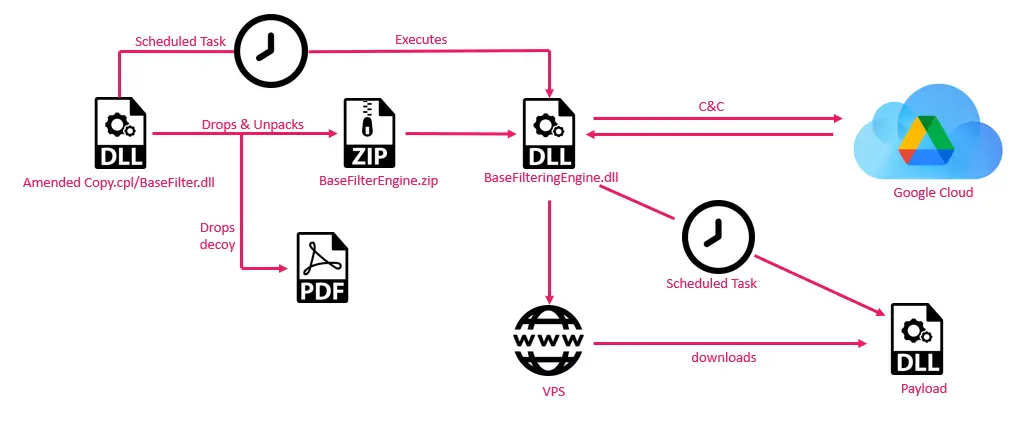
Google Drive-based Campaign Infection Chain | Image: Check Point
In a new report, cybersecurity researchers from Check Point detail the evolution of ElizaRAT, a remote access tool (RAT) used by the notorious APT36, also known as Transparent Tribe. The report highlights how this Pakistan-based threat group has continuously refined its malware and infrastructure to enhance evasion techniques, largely targeting high-profile entities within India.
APT36 has long targeted Indian government organizations, diplomatic personnel, and military facilities. Known for its persistence and adaptability, this group recently upgraded ElizaRAT to bolster its command and control (C2) capabilities and detection evasion. The researchers reveal that ElizaRAT is primarily deployed through phishing campaigns, with malicious links to Google Storage likely sent via spear-phishing emails.
“APT36, also known as Transparent Tribe, is a Pakistan-based threat actor notorious for persistently targeting Indian government organizations, diplomatic personnel, and military facilities,” states Check Point.
The latest variants of ElizaRAT have demonstrated notable advancements, especially with the integration of mainstream cloud platforms like Telegram, Google Drive, and Slack to support C2 operations. These services are widely used, helping the malware blend into regular network traffic to avoid detection. According to the report, “ElizaRAT samples indicate a systematic abuse of cloud-based services, including Telegram, Google Drive, and Slack, to facilitate command and control communications.”
APT36 has also introduced ApoloStealer, a new stealer payload that was first identified in 2024. ApoloStealer shares similarities with previous Transparent Tribe malware and uses the same working directory as the ElizaRAT variant associated with the Slack C2 campaign. This payload targets specific file types and directories on infected systems, storing and exfiltrating data in a meticulous manner to avoid detection.
ApoloStealer underscores APT36’s shift towards more modular malware. It is designed to collect and exfiltrate files with extensions such as .doc, .ppt, .pdf, .jpg, and others from users’ desktop, downloads, and OneDrive directories.
Check Point’s report identifies multiple ElizaRAT campaigns, each with distinct infrastructures and delivery methods:
- Slack Campaign: A variant known as SlackAPI.dll leverages Slack channels for C2 communication, where the malware polls for commands every 60 seconds and transmits stolen data back to the C2 server.
- Google Drive Campaign: This campaign variant utilizes Google Drive for C2 operations, accessing a specific shared folder and executing commands via downloaded payloads. The threat actor carefully disguised filenames like “Threat Alert 1307-JS-9.pdf” to increase the likelihood of successful phishing attacks.
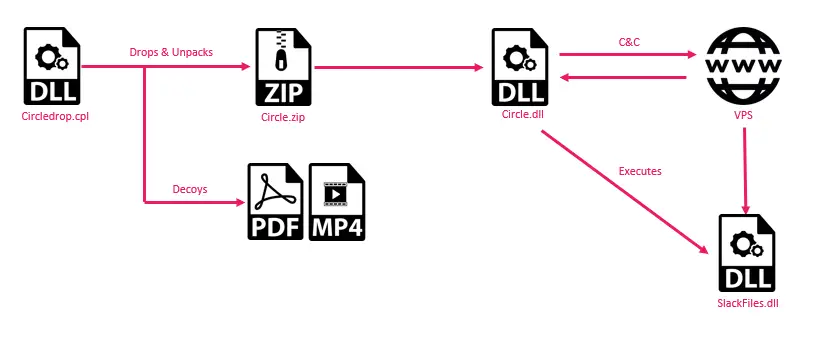
- Circle Campaign: In contrast to the cloud-based variants, the Circle campaign uses a virtual private server (VPS) for C2, suggesting APT36’s willingness to diversify its infrastructure for increased resilience.
As Check Point concludes, “the progression of ElizaRAT reflects APT36’s deliberate efforts to enhance their malware to better evade detection and effectively target Indian entities.” By employing commonly used cloud services as cover, the group leverages familiar platforms to facilitate espionage while minimizing their risk of exposure.
Related Posts:
- Transparent Tribe Targets Indian Government and Defense Sectors with Evolving Cyber Espionage Tactics
- From SideCopy to Transparent Tribe: Pakistan APTs Hit Indian Government With RATs
- Two New Variants of the Spectre Vulnerability were found by Security researchers
- Cybercriminals Mimic Slack in Sophisticated Malvertising Campaign
- TikTok Hit by Zero-Day Attack: High-Profile Accounts Compromised