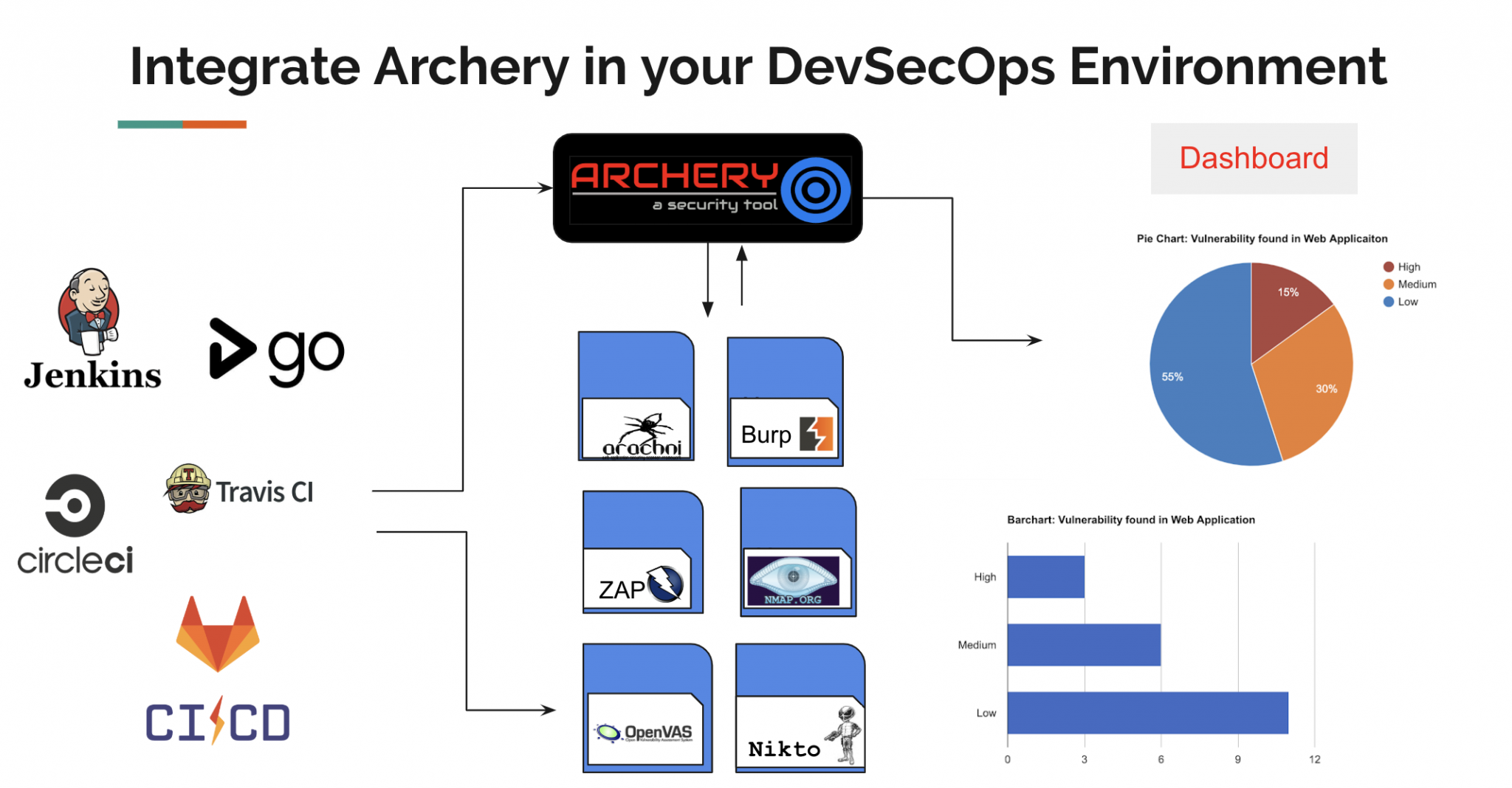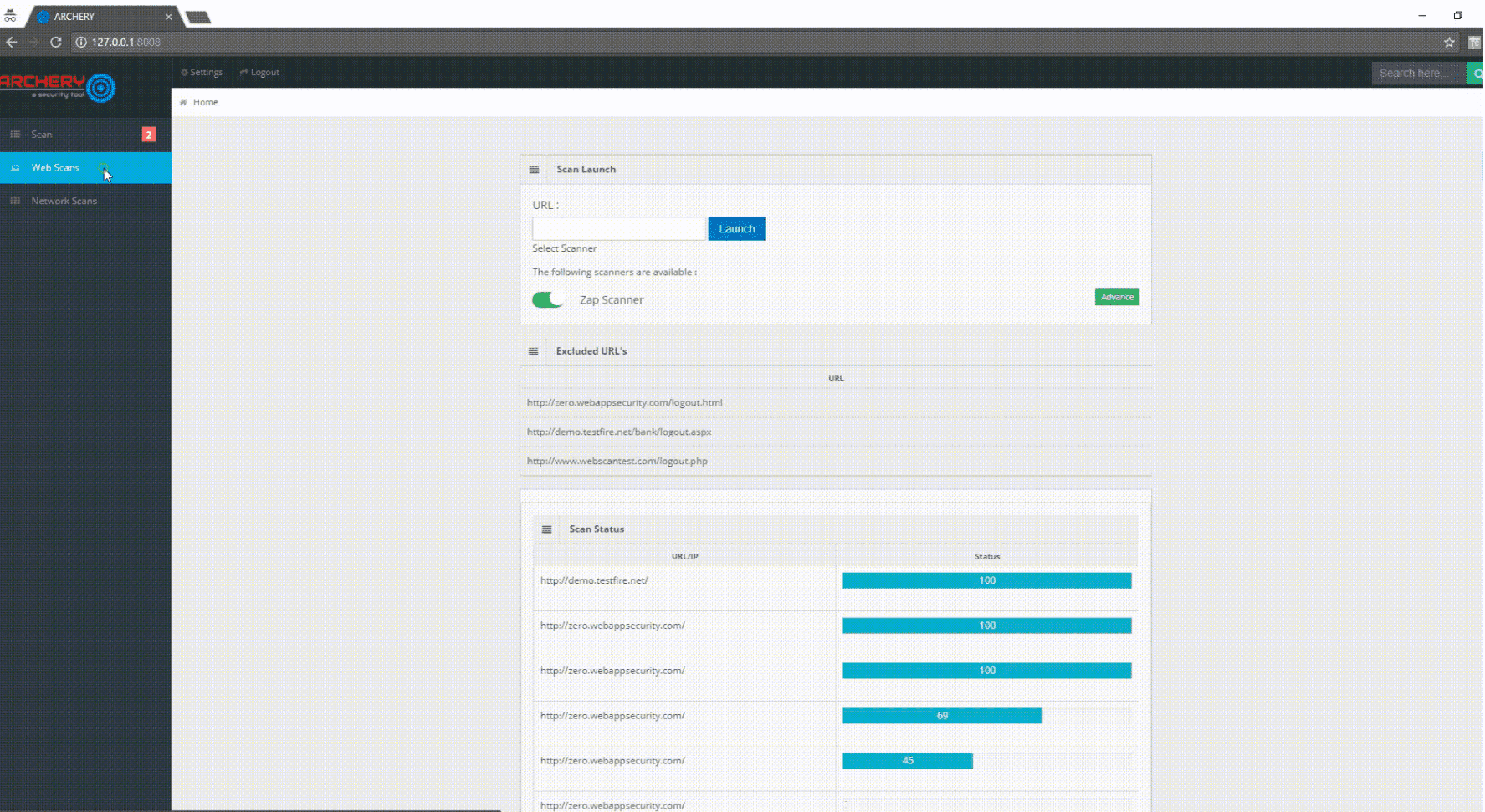
Archery is an opensource vulnerability assessment and management tool which helps developers and pentesters to perform scans and manage vulnerabilities. Archery uses popular opensource tools to perform comprehensive scanning for web applications and networks. It also performs web application dynamic authenticated scanning and covers the whole applications by using selenium. The developers can also utilize the tool for the implementation of their DevOps CI/CD environment.
Overview of the tool:
- Perform Web and Network Vulnerability Scanning using opensource tools.
- Correlates and Collaborate all raw scans data, shows them in a consolidated manner.
- Perform authenticated web scanning.
- Perform web application scanning using selenium.
- Vulnerability Management.
- Enable REST API’s for developers to perform scanning and Vulnerability Management.
- JIRA Ticketing System.
- Subdomain discovery and scanning.
- Periodic scans.
- Concurrent scans.
- Useful for DevOps teams for Vulnerability Management.
Changelog v2.0.5
🚀 New scanners
🚀 Features and enhancements
- Adding Search builder to all DataTables (#603)
- Enhanced Jira integration (#601)
- Vuls & Nmap Vulners parsers, few fixes (#600)
- Enhanced & modular parsers (#595)
🐛 Bug Fixes
Requirement
- Python 3.6+ – Python 3.6 Download
- OpenVAS 8, 9
- OWASP ZAP 2.7.0
- Selenium Python Firefox Web driver
- SSLScan
- Nikto
- NMAP Vulners
OpenVAS
You can follow the instructions to install OpenVAS from Hacker Target
Note that, at this time, Archery generates a TCP connection towards the OpenVAS Manager (not the GSA): therefore, you need to update your OpenVAS Manager configuration to bind this port. Its default port (9390/tcp), but you can update this in your settings.
OWASP Zap
Also known as Zaproxy. Simply download and install the matching package for your distro from the official Github Page.
Systemd service file is available in the project.
Burp Scanner
Follow the instruction in order to enable Burp REST API. You can manage and trigger scans using Archery once REST API enabled.
Systemd service file is available in the project.
SSLScan
Simply install SSLScan from your package manager.
Nikto
Simply install Nikto from your package manager.
NMAP Vulners
Simply get the NSE file to the proper directory:
Installation
Documentation
Demo

Copyright (c) 2017, ArcherySec Maintainers, All rights reserved.
Source: https://github.com/anandtiwarics/