Image: Cisco Talos
A recent report from Cisco Talos has exposed a new threat actor named DragonRank, a Chinese-speaking group specializing in SEO manipulation and cyberattacks. This group operates by exploiting vulnerable web application services to compromise websites, specifically targeting Windows Internet Information Services (IIS) servers. DragonRank’s methods include deploying malware such as PlugX and BadIIS, tools that have previously been linked to other Chinese cybercriminal groups.
What makes DragonRank stand out is its primary focus on search engine optimization (SEO) fraud. By compromising IIS servers, the group can manipulate search engine rankings to boost the visibility of fraudulent websites. This manipulation harms legitimate businesses by associating their websites with deceptive content, which can damage reputations and lead to financial loss.
The compromised servers are used to host scam websites that target users with content related to illicit topics. These malicious websites are optimized for search engines like Google, Yahoo, and Bing, making it easy for unsuspecting users to stumble upon them. DragonRank is not limited to a single geographic region; they have been observed attacking servers in countries across Asia and Europe, including Thailand, India, Korea, Belgium, and China.
Cisco Talos’ investigation also uncovered that DragonRank operates a commercial website offering both white hat and black hat SEO services. This business model allows DragonRank to advertise its unethical SEO manipulation tactics openly, including cross-site ranking, parasite ranking, and search result dominance. Their services are available in both Chinese and English, and they have been found advertising these services across various legitimate websites.
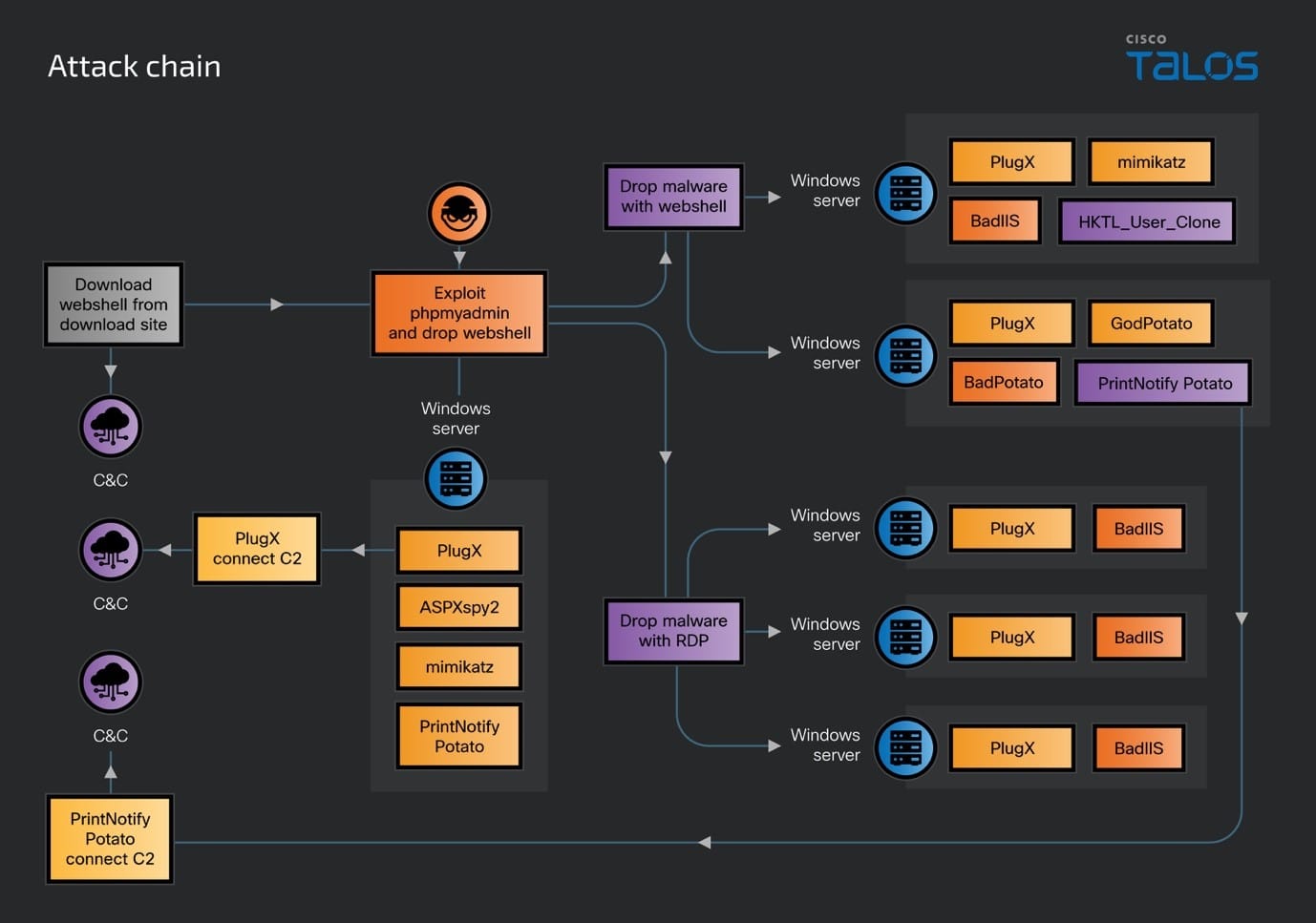
DragonRank’s attack chain begins with exploiting vulnerabilities in popular web applications like phpMyAdmin and WordPress, allowing them to deploy a web shell on compromised servers. Once inside, the group uses malware like PlugX and BadIIS to maintain persistence, escalate privileges, and move laterally across the network. They use tools like Mimikatz, GodPotato, and PrintNotifyPotato to harvest credentials, furthering their control over the infected systems.
One of the most alarming aspects of DragonRank’s operations is its ability to maintain a low profile. The group frequently uses techniques like DLL sideloading and exception handling to evade detection by security tools. For example, the PlugX malware employed by DragonRank uses the Windows Structured Exception Handling (SEH) mechanism to load malicious code without raising suspicion.
DragonRank has also deployed BadIIS, a malware designed to manipulate HTTP responses from compromised IIS servers. This tactic allows the group to interfere with how search engine crawlers view the infected sites, boosting the search engine rankings of malicious websites. BadIIS operates as a proxy between the server and the Command and Control (C2) infrastructure, helping DragonRank manipulate SEO algorithms to their advantage.
DragonRank’s rapid expansion across different regions and industries signals a significant evolution in the use of SEO manipulation as a cybercrime tactic. Their attacks have targeted a broad range of sectors, from healthcare and manufacturing to media and IT services. This non-targeted approach suggests that DragonRank is casting a wide net, seeking opportunities wherever vulnerabilities exist.
While DragonRank’s origins point to a Simplified Chinese-speaking group, their reach extends far beyond China. The group’s online presence includes Telegram and QQ accounts, where they openly communicate with clients and provide customized SEO services. This business-like approach to cybercrime is becoming increasingly common among hacking groups, allowing them to profit not just from direct attacks but also from selling their services to other criminals.