BOFHound
BOFHound is an offline BloodHound ingestor and LDAP result parser compatible with TrustedSec’s ldapsearch BOF and the Python adaptation, pyldapsearch. BOFHound will parse sets of log files to generate BloodHound compatible JSON files for those times when your team needs more control over the queries being run and the data coming back. With utilities such as the aforementioned ldapsearch BOF, BloodHound data can now be pulled low and slow, potentially avoiding the honeypots and expensive LDAP query thresholds, and ingested in a way that allows offensive professionals to use the many features of BloodHound again.
By parsing log files generated by the aforementioned tools, BOFHound allows operators to utilize BloodHound’s beloved interface while maintaining full control over the LDAP queries being run and the speed at which they are executed. This leaves room for operator discretion to account for potential honeypot accounts, expensive LDAP query thresholds, and other detection mechanisms designed with the traditional, automated BloodHound collectors in mind.
Install
pip3 install bofhound
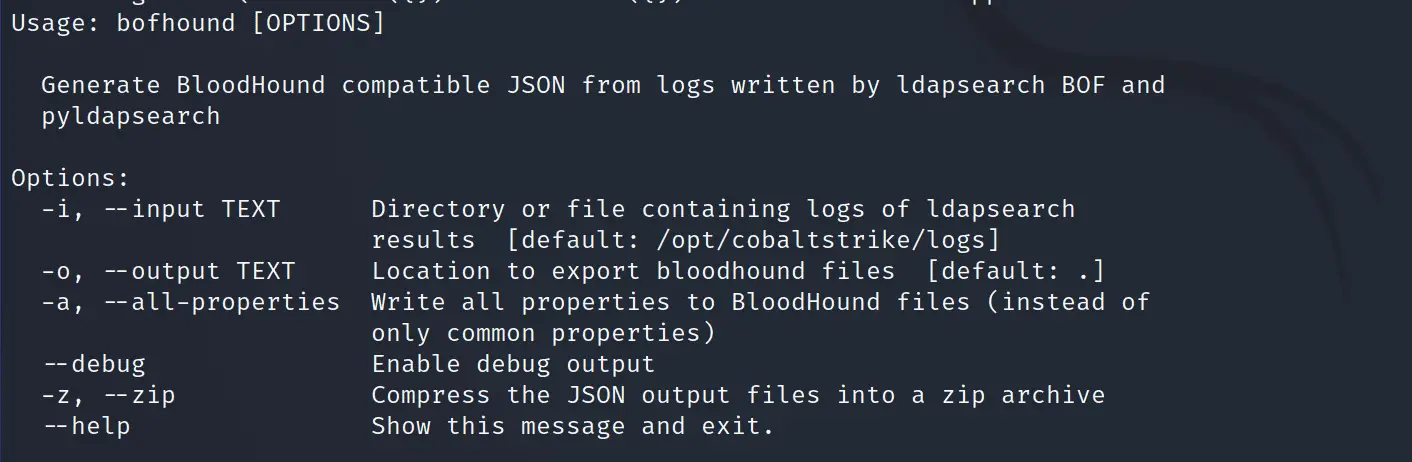
Use

Example Usage
Parse ldapseach BOF results from Cobalt Strike logs (/opt/cobaltstrike/logs by default) to /data/
bofhound -o /data/
Parse pyldapsearch logs and only include common BloodHound properties
bofhound -i ~/.pyldapsearch/logs/ –all-properties
ldapsearch Query Examples
Required Data
The following attributes are required for proper functionality:
samaccounttype
dn
objectsid
Get All the Data (Maybe Run BloodHound Instead?)
ldapsearch (objectclass=*)
Retrieve All Schema Info
ldapsearch (schemaIDGUID=*) name,schemaidguid -1 “” CN=Schema,CN=Configuration,DC=windomain,DC=local
Retrieve Only the ms-Mcs-AdmPwd schemaIDGUID
ldapsearch (name=ms-mcs-admpwd) name,schemaidguid 1 “” CN=Schema,CN=Configuration,DC=windomain,DC=local
Copyright (c) 2022, Fortalice Solutions, LLC.
All rights reserved.
Source: https://github.com/fortalice/