Sandbox Scryer: open source tool for producing threat hunting and intelligence data
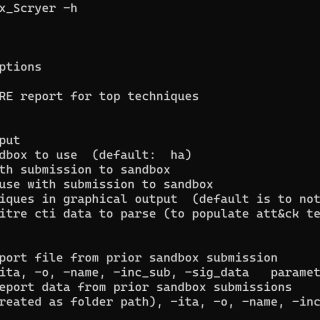
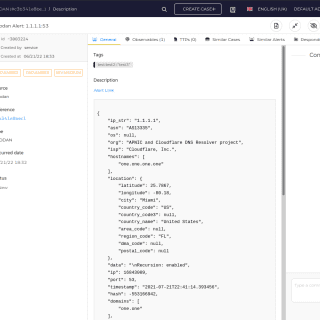
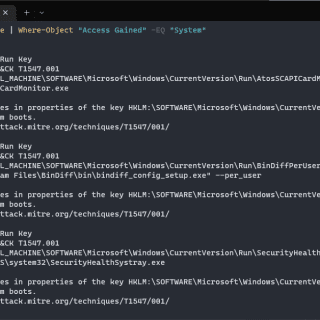
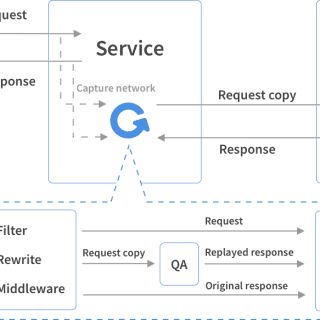
Sandbox Scryer The Sandbox Scryer is an open-source tool for producing threat hunting and intelligence data from public sandbox detonation output. The tool leverages the MITRE ATT&CK Framework to organize and prioritize findings, assisting...