Category: Password Attacks
What is MQTT? MQTT stands for MQ Telemetry Transport. It is a publish/subscribe, extremely simple and lightweight messaging protocol, designed for constrained devices and low-bandwidth, high-latency or unreliable networks. The...
Weapon of Mass Destruction This is a python tool with a collection of IT security software. The software is incapsulated in “modules”. The modules does consist of pure python code...
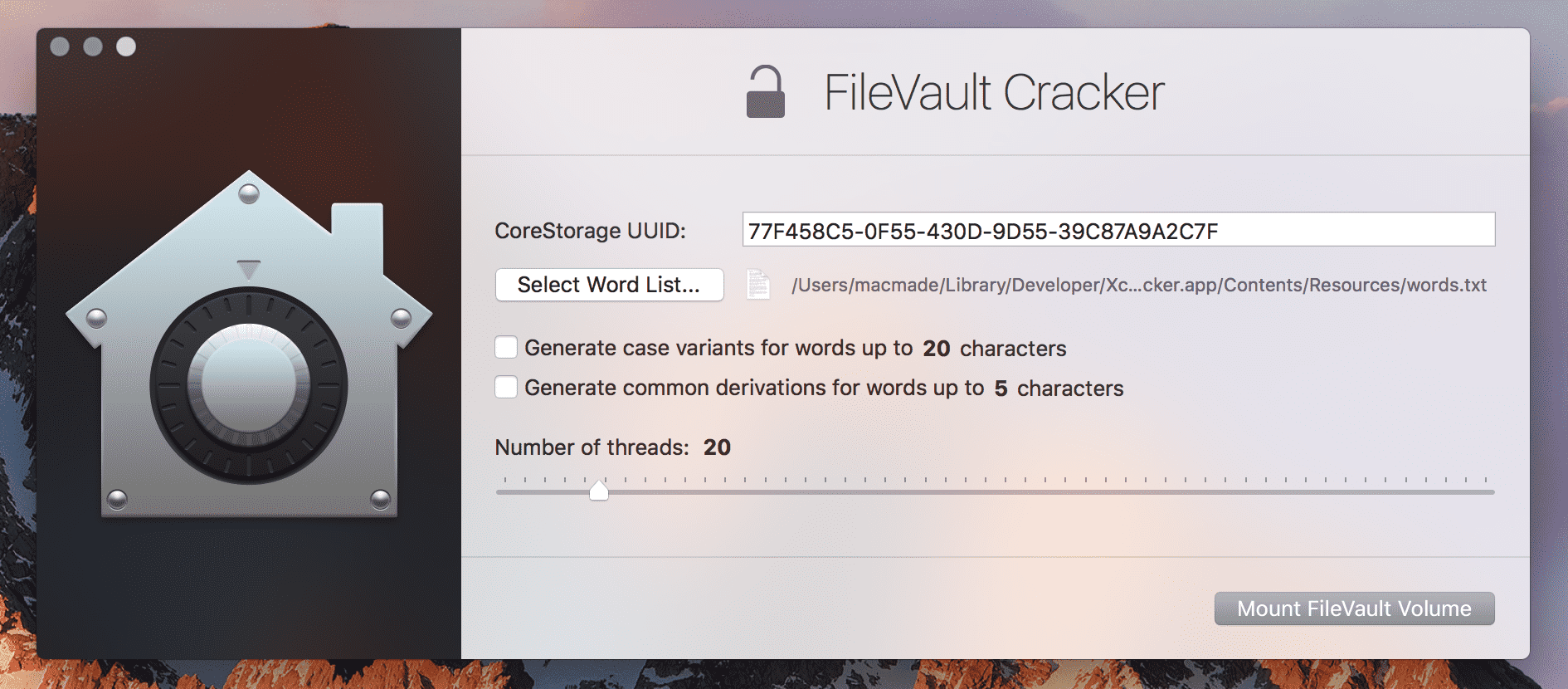
Today, we are introduced for a macOS FileVault disk file protection function of the password crack tool, the tool is easy to use. Introduction to FileVault In fact, FileVault should be...
Cheetah is a dictionary-based brute force password webshell tool, running as fast as a cheetah hunt for prey. Cheetah’s working principle is that it can submit a large number of...
pymultitor Python Multi-Threaded Tor Proxy Did you ever want to be at two different places at the same time? When I asked myself this question, I actually started developing this...
What does BEWGor do? At its core, BEWGor is designed help with ensuring password security. It is a Python script that prompts the user for biographical data about a person...
A facecheck2.0.php script that its function would be to verify accounts on Facebook. I know there is such a script that can be useful for someone or his logic, I...
Sometimes, on your Penetration Testing, a Hash value is encountered, it is possible to identify the possible Hash types based on the different characteristics of each hash value, but this...
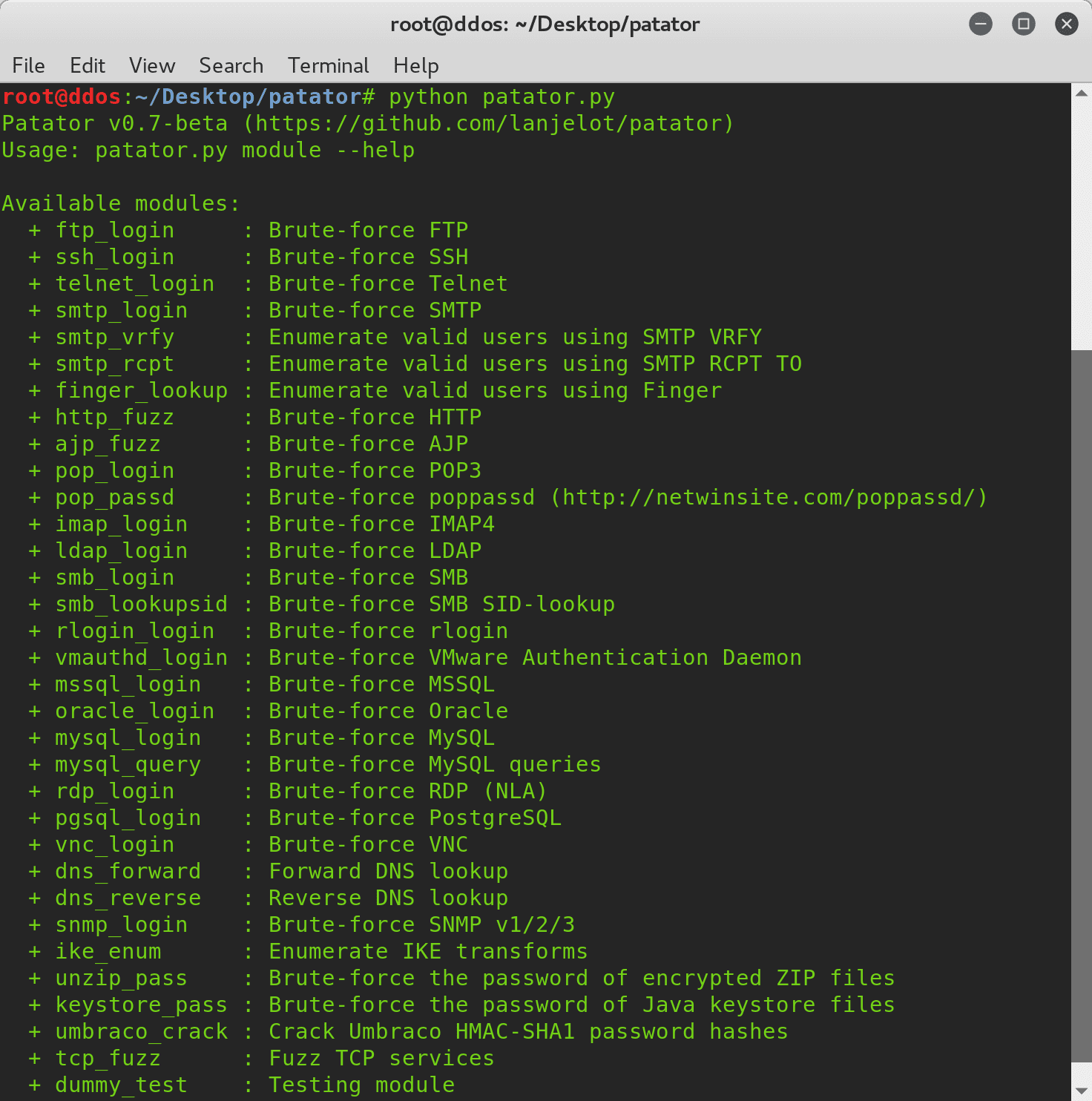
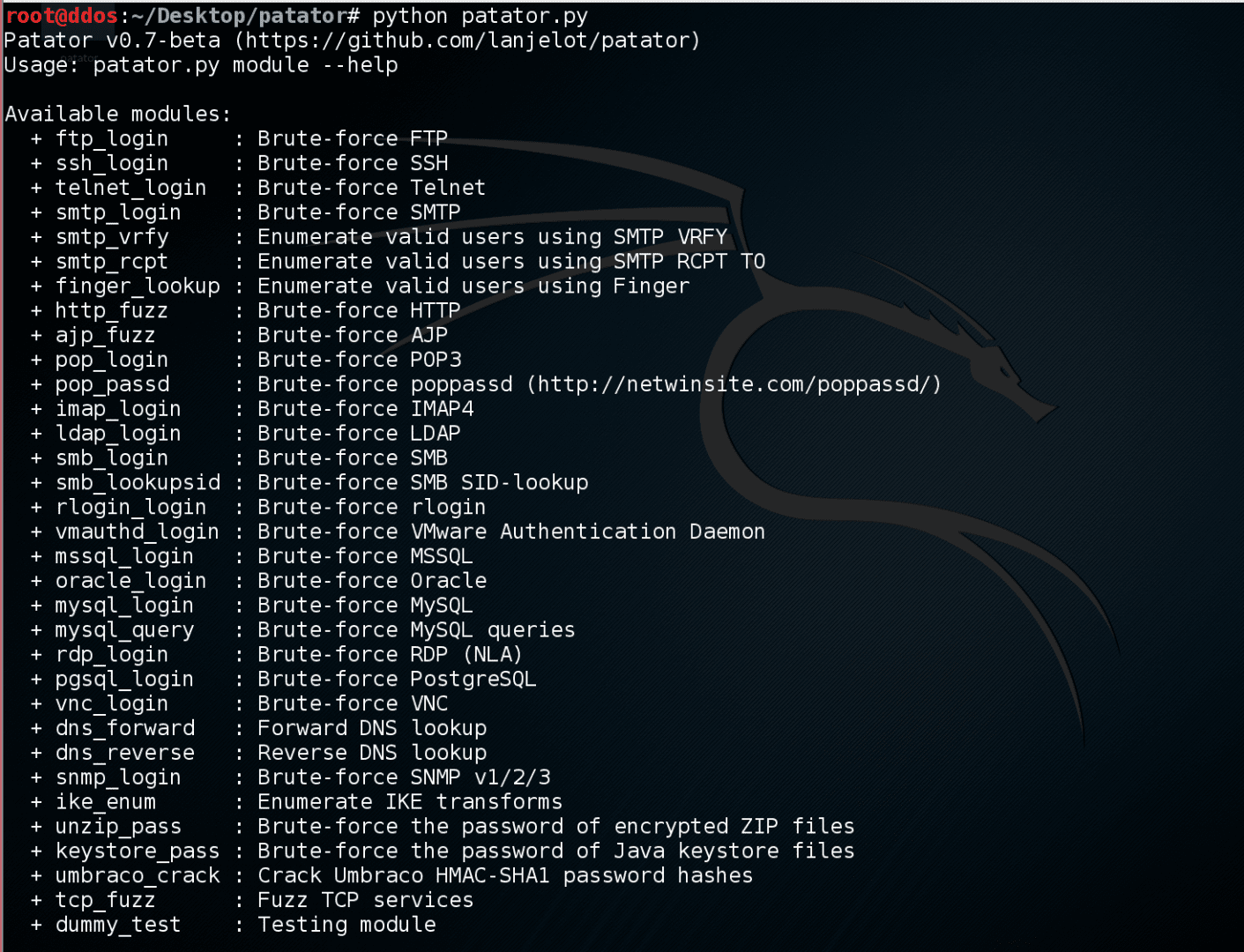
What is patator? It is a universal tool brute force, having on board a decent number of modules and the ability to fairly flexible settings. Patator is, as usual, a python...
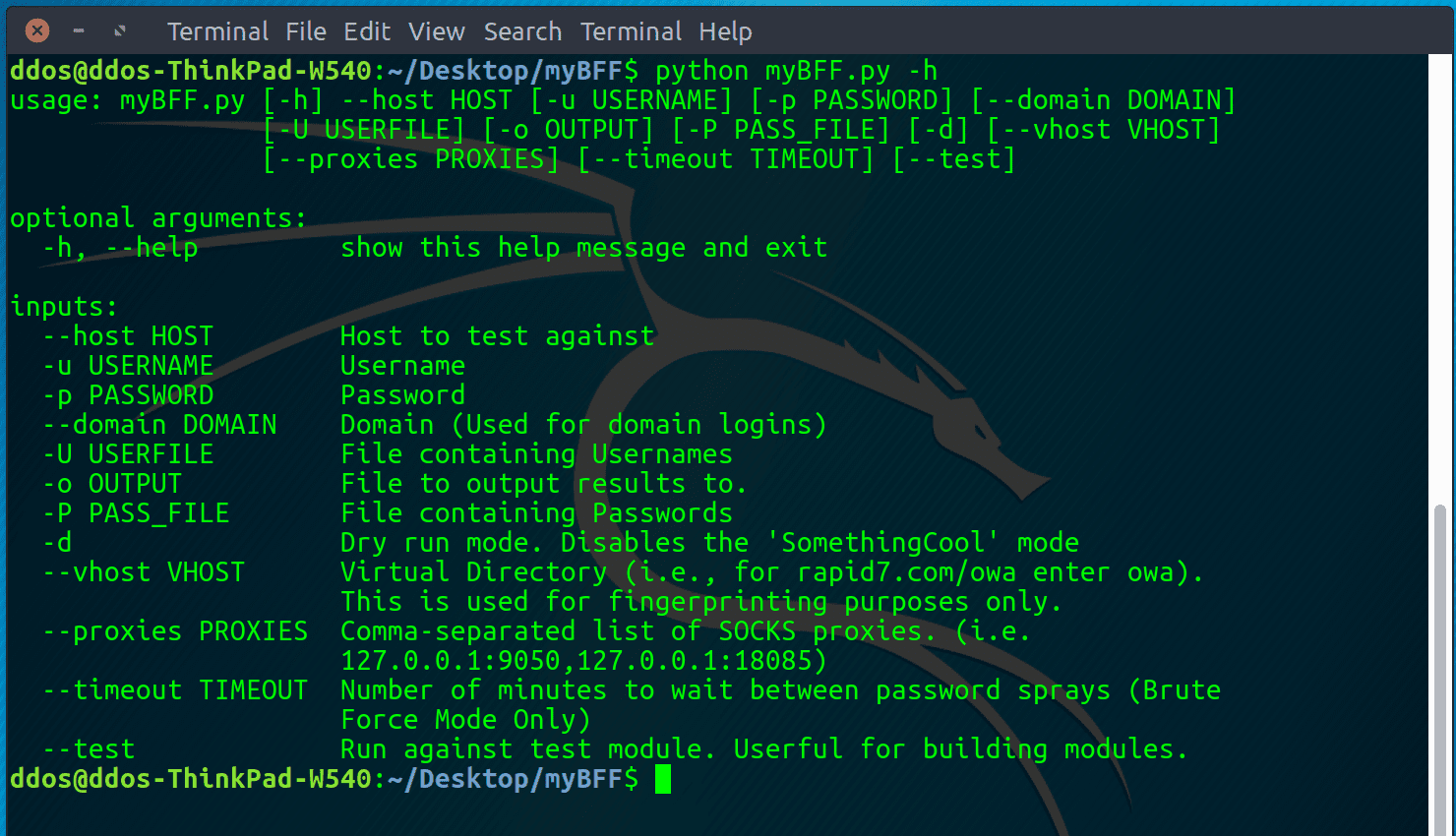
myBFF is a web application brute force framework. Point the framework at a file containing usernames, a host, and give it a password. The framework will determine what type of...
Some time ago came md5online search engine mass, free and online hashes where you can find up to 25,000 hashes in a batch. Automatically detects the hash you are looking for...
A password and cryptography attack that does not attempt to decrypt any information, but continue to try a list of different passwords, words, or letters. For example, a simple brute-force...
DESCRIPTION Sentry detects and prevents bruteforce attacks against sshd using minimal system resources. SAFE To prevent inadvertant lockouts, Sentry auto-whitelists IPs that have connected more than 3 times and succeeded...
Burp suite has always been used to burst a variety of forms used to submit the login authentication, today i am going guide you how to use Use the Burp...
WordList 15 GB: CrackStation.Password.Cracking.Dictionary CrackStation’s 15GB 1.5 billion entry password cracking dictionary. The wordlist is being sold by CrackStation using a “pay what you want” model. If you find this dictionary...