Category: Post Exploitation
cypherhound A Python3 terminal application that contains 260+ Neo4j cyphers for BloodHound data sets. Why? BloodHound is a staple tool for every red teamer. However, there are some negative side effects based on its design. I will cover...
DragonCastle A PoC that combines AutodialDLL lateral movement technique and SSP to scrape NTLM hashes from the LSASS process. Description Upload a DLL to the target machine. Then it enables the remote registry to...
BloodHound Attack Research Kit BARK stands for BloodHound Attack Research Kit. It is a PowerShell script built to assist the BloodHound Enterprise team with researching and continuously validating abuse primitives. BARK currently focuses on...
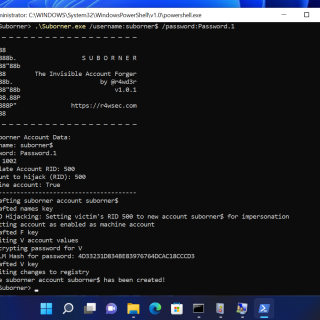
Suborner – A Windows Bribery for Invisible Persistence A simple program to create a Windows account you will only know about 🙂 Create invisible local accounts without net user or Windows OS user management...
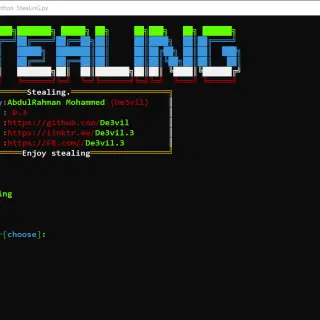
SteaLinG The SteaLinG is an open-source penetration testing framework designed for social engineering. After the hack, you can upload it to the victim’s device and run it. Features module Short description Dump password steal...
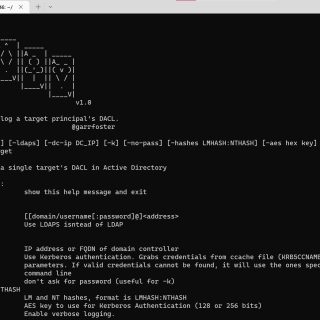
Aced Aced is a tool to parse and resolve a single targeted Active Directory principal’s DACL. Aced will identify interesting inbound access allowed privileges against the targeted account, resolve the SIDS of the inbound...
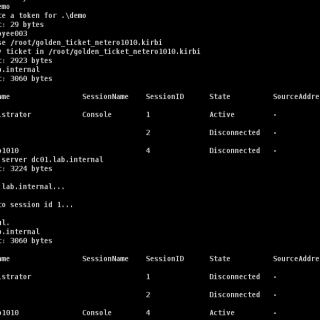
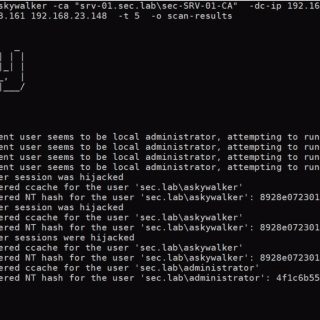
BOF – RDPHijack Cobalt Strike Beacon Object File (BOF) that uses WinStationConnect API to perform local/remote RDP session hijacking. With a valid access token / kerberos ticket (e.g., golden ticket) of the session owner,...
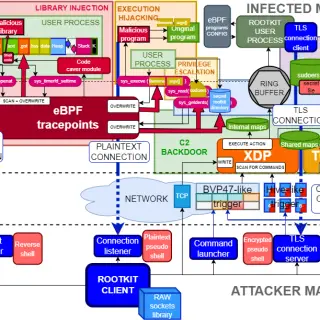
TripleCross TripleCross is a Linux eBPF rootkit that demonstrates the offensive capabilities of the eBPF technology. TripleCross is inspired by previous implant designs in this area, notably the works of Jeff Dileo at DEFCON...
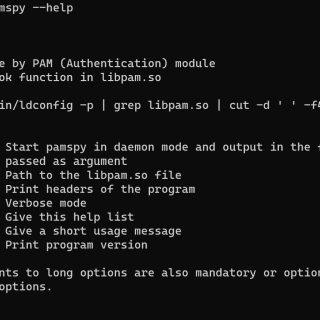
pamspy — Credentials Dumper for Linux pamspy leverages eBPF technologies to achieve an equivalent work of 3snake. It will track a particular userland function inside the PAM (Pluggable Authentication Modules) library, used by many...
Masky Masky is a python library providing an alternative way to remotely dump domain users’ credentials thanks to an ADCS. A command line tool has been built on top of this library in order...
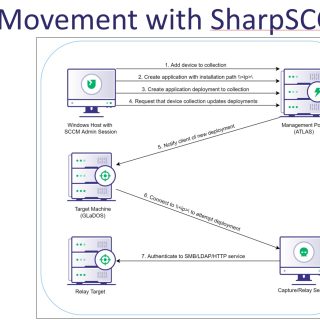
SharpSCCM SharpSCCM is a post-exploitation tool designed to leverage Microsoft Endpoint Configuration Manager (a.k.a. ConfigMgr, formerly SCCM) for lateral movement without requiring access to the SCCM administration console GUI. SharpSCCM was initially created to...
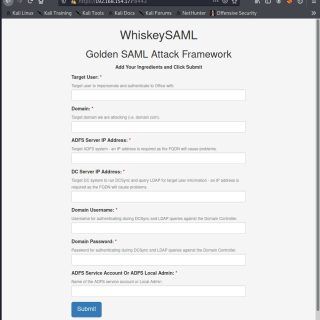
WhiskeySAML and Friends TicketsPlease TicketsPlease: Python library to assist with the generation of Kerberos tickets, remote retrieval of ADFS configuration settings, generation of Golden SAML tokens, and retrieval of Azure Access Tokens. Modules ldap...
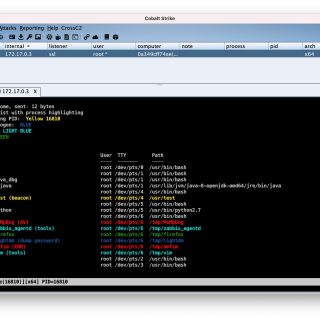
CrossC2 Kit CrossC2Kit is an infiltration expansion around the Unix platform derived from CrossC2. Use Aggressor Script Open Source Script engine. It can be used to create automation to simulate the operation process of the Red...
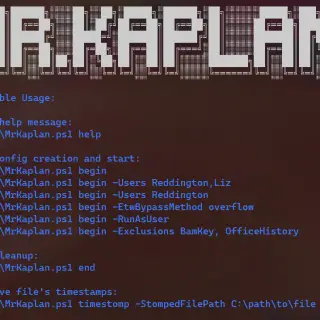
Mr.Kaplan The biggest problem for any attacker is the windows event logger (ETW). Almost every famous blue teams agents (Sysmon, Wazuh, etc.) use it, which means that if you somehow disable this service no...
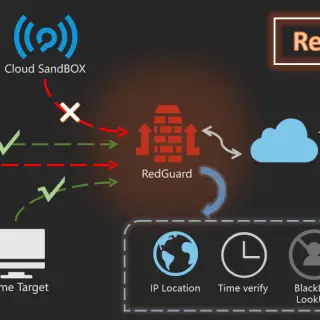
RedGuard – Excellent C2 Front Flow Control tool RedGuard is a derivative work of the C2 facility pre-flow control technology. It has a lighter design, efficient flow interaction, and reliable compatibility with go language...