Category: Social Engineering
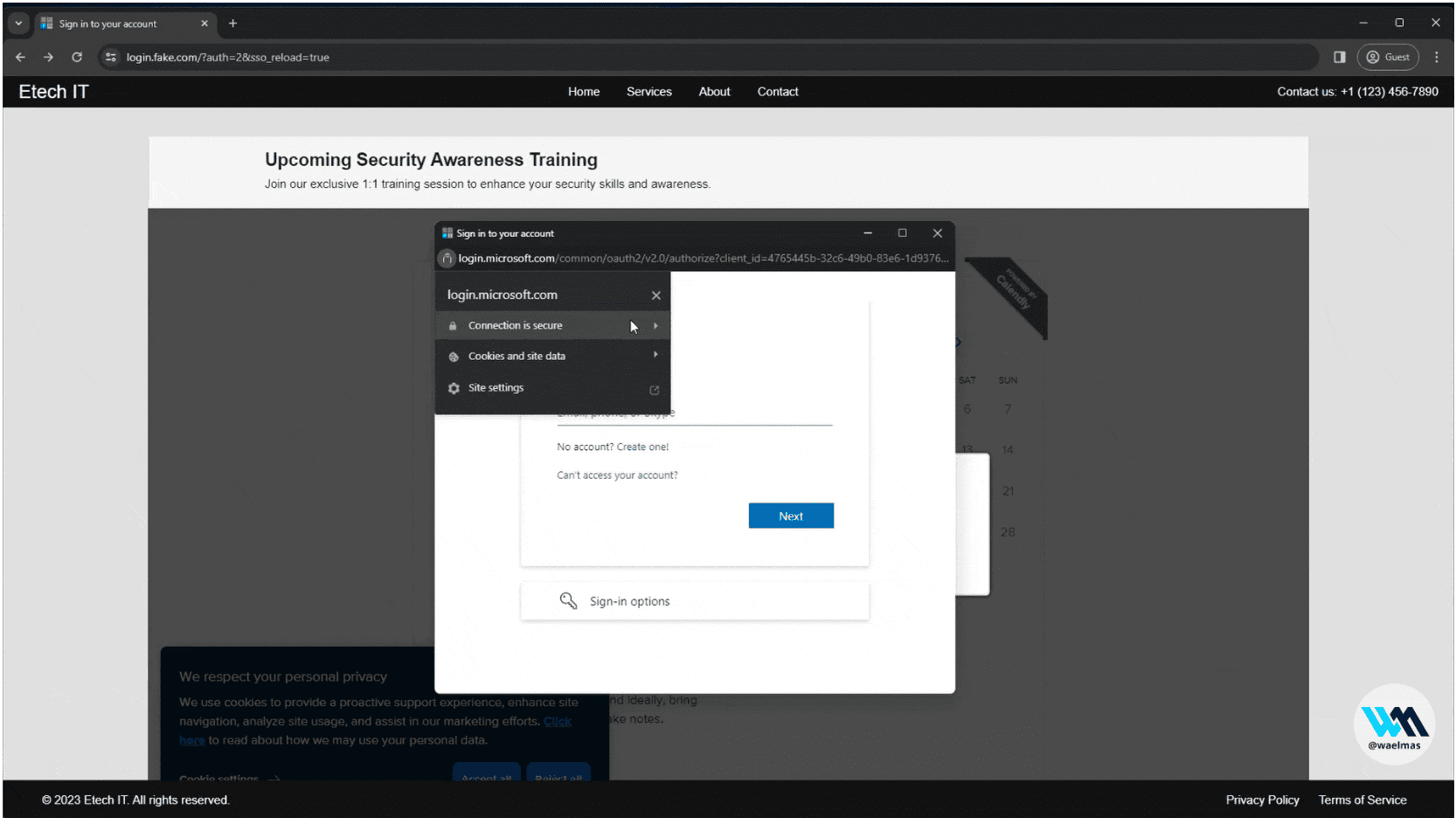
Frameless BITB A new approach to Browser In The Browser (BITB) without the use of iframes, allows the bypass of traditional framebusters implemented by login pages like Microsoft. This POC...
r4ven The tool hosts a fake website that uses an iframe to display a legit website and, if the target allows it, it will fetch the Gps location (latitude and...
EvilSlackbot A Slack Attack Framework for conducting Red Team and phishing exercises within Slack workspaces. Background Thousands of organizations utilize Slack to help their employees communicate, collaborate, and interact. Many...
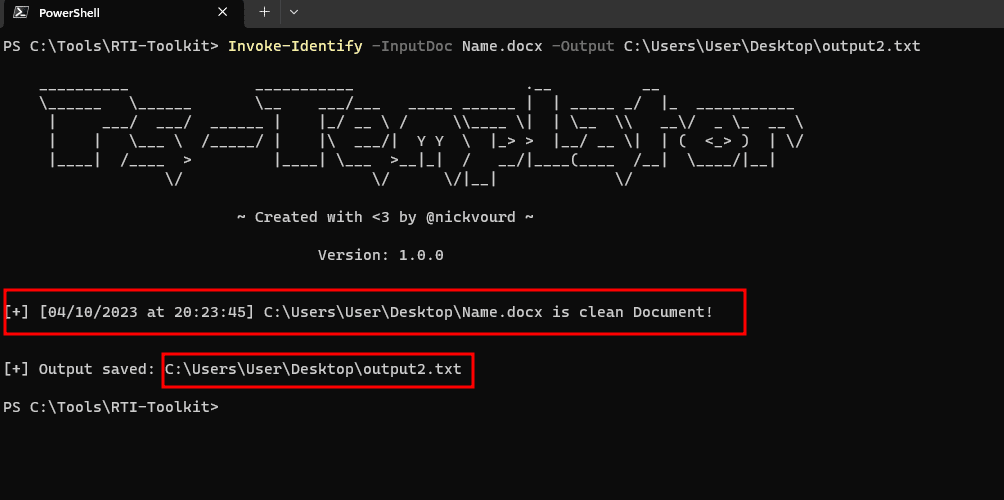
RTI-Toolkit RTI-Toolkit is an open-source PowerShell toolkit for Remote Template Injection attacks. This toolkit includes a PowerShell script named PS-Templator.ps1 which can be used from both an attacking and defensive perspective....
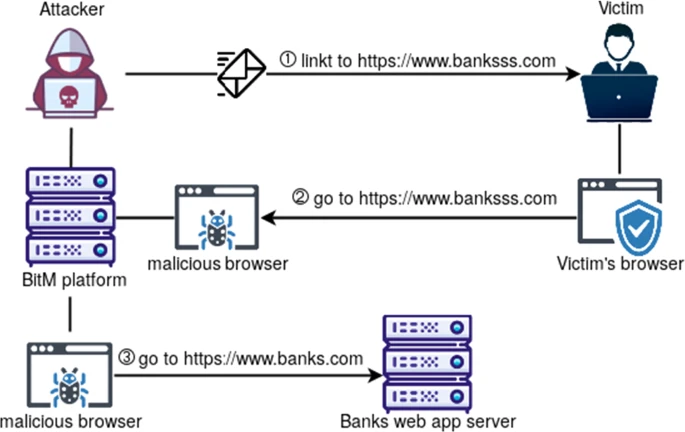
CuddlePhish Weaponized multi-user browser-in-the-middle (BitM) for penetration testers. This attack can be used to bypass multi-factor authentication on many high-value web applications. It even works for applications that do not...
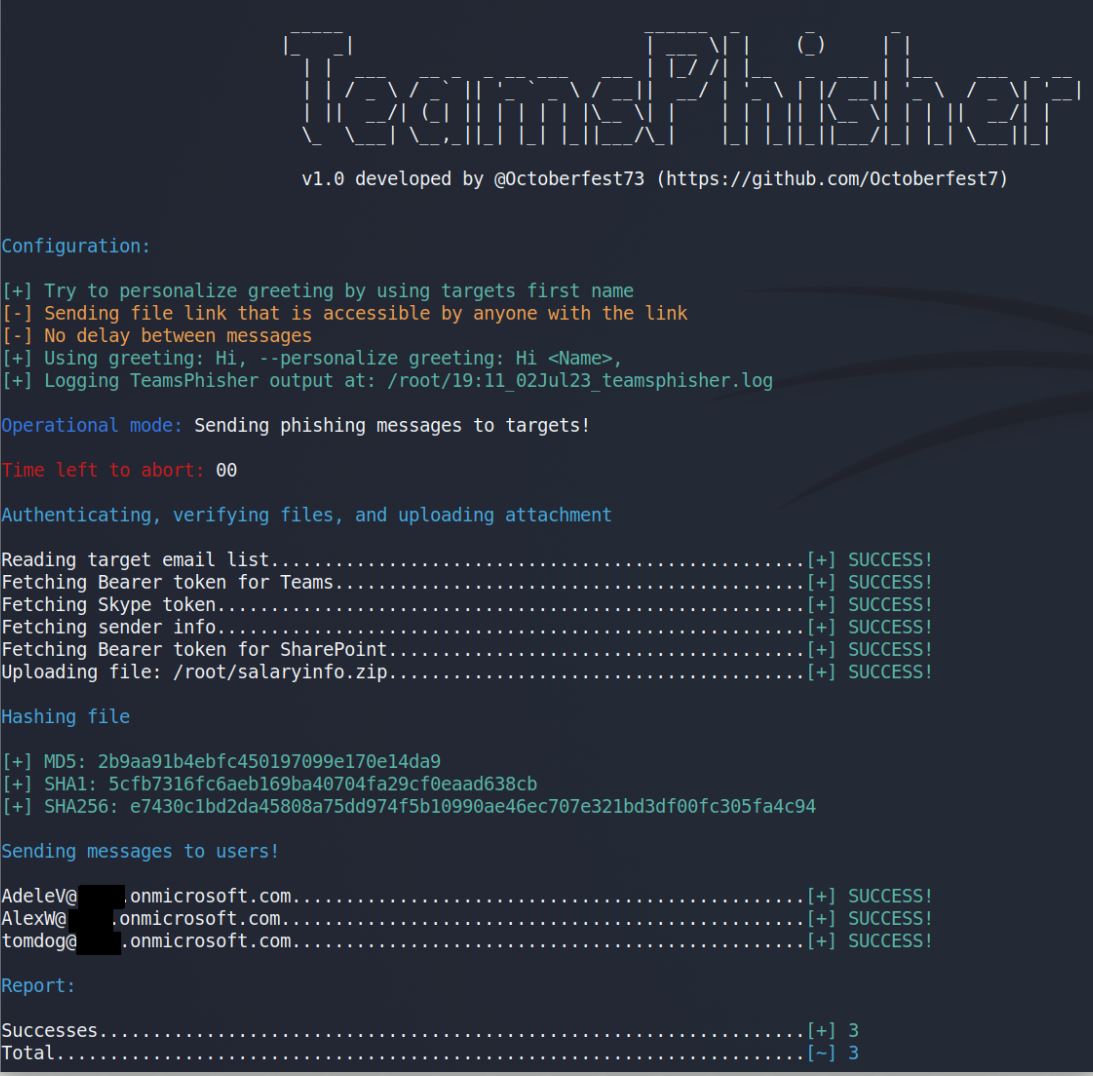
TeamsPhisher TeamsPhisher is a Python3 program that facilitates the delivery of phishing messages and attachments to Microsoft Teams users whose organizations allow external communications. It is not ordinarily possible to...
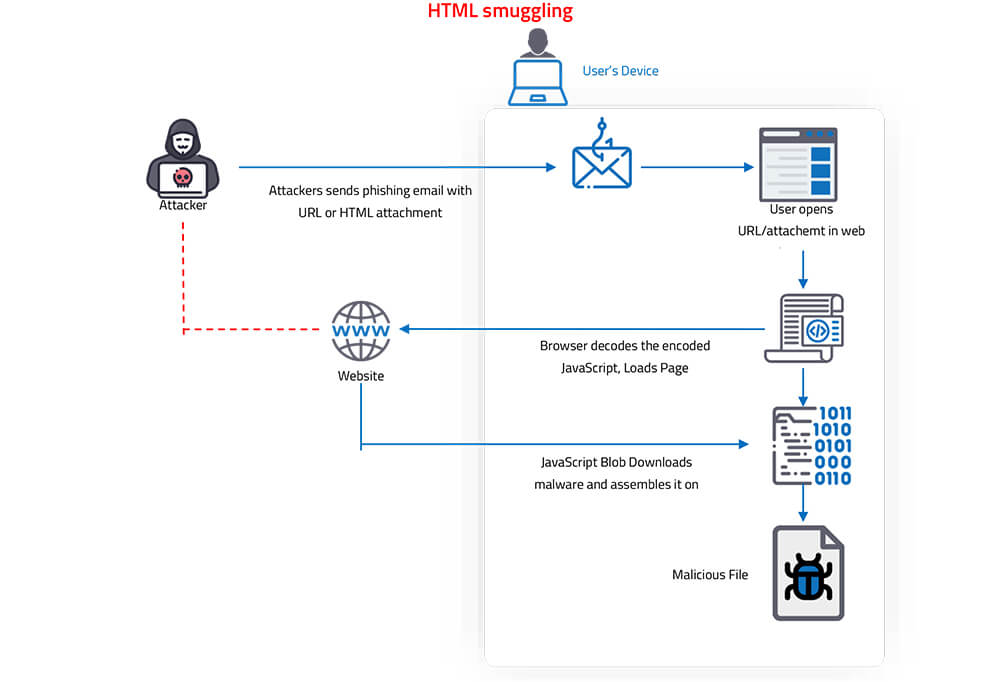
Html Smuggling HTML smuggling is a malicious technique used by hackers to hide malware payloads in an encoded script in a specially crafted HTML attachment or web page. The malicious...
QRExfiltrate This tool is a command line utility that allows you to convert any binary file into a QRcode GIF. The data can then be reassembled visually allowing the exfiltration...
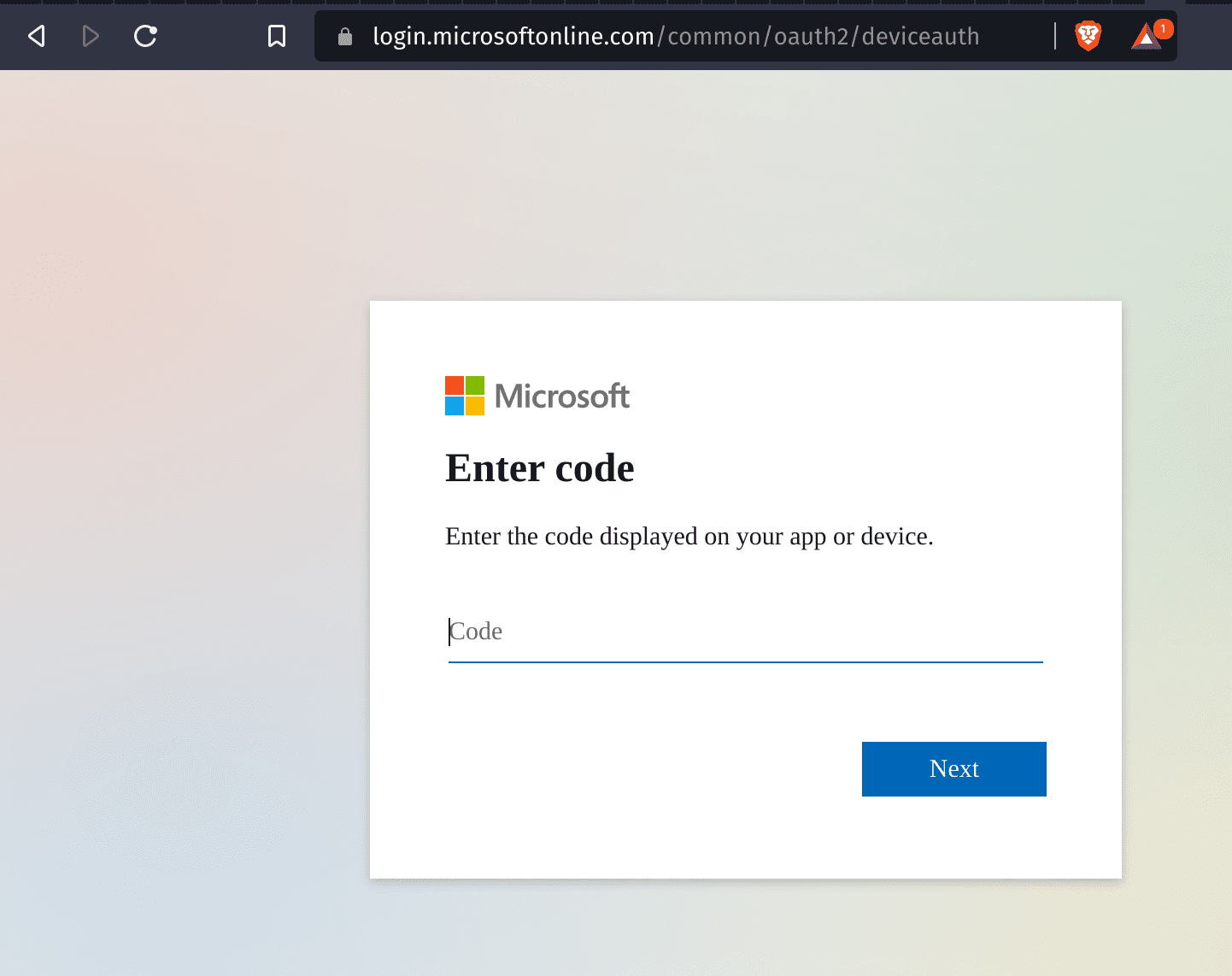
SquarePhish SquarePhish is an advanced phishing tool that uses a technique combining the OAuth Device code authentication flow and QR codes. See PhishInSuits for more details on using OAuth Device Code flow...
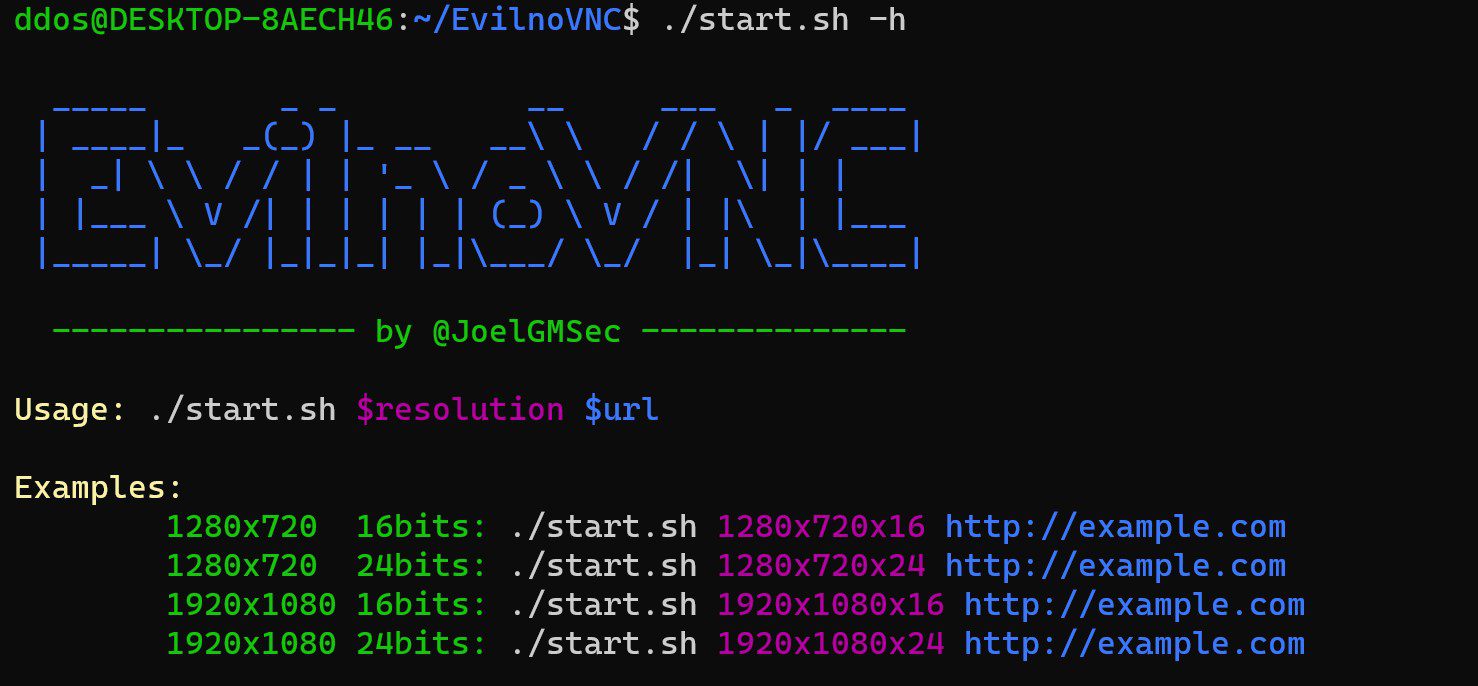
EvilnoVNC EvilnoVNC is a Ready to go Phishing Platform. Unlike other phishing techniques, EvilnoVNC allows 2FA bypassing by using a real browser over a noVNC connection. In addition, this tool allows...
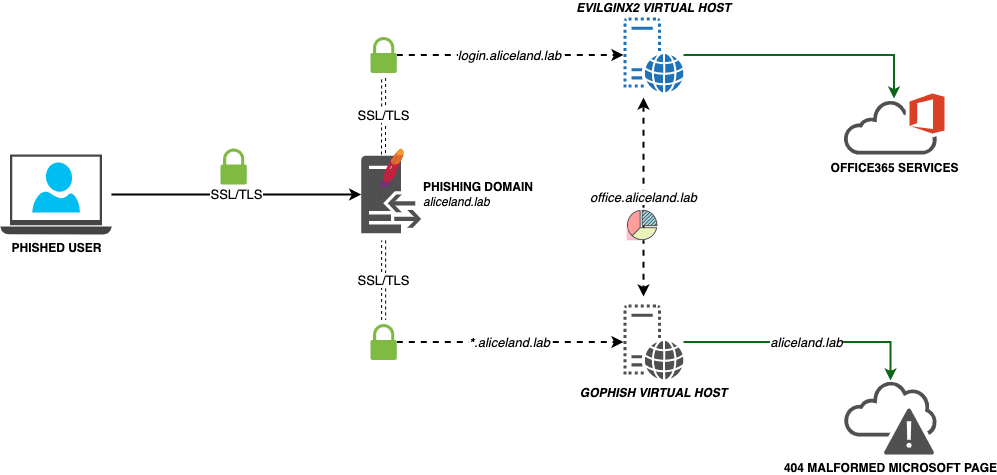
evilgophish Combination of evilginx2 and GoPhish. Why? As a penetration tester or red teamer, you may have heard of evilginx2 as a proxy man-in-the-middle framework capable of bypassing two-factor/multi-factor authentication. This is enticing to...
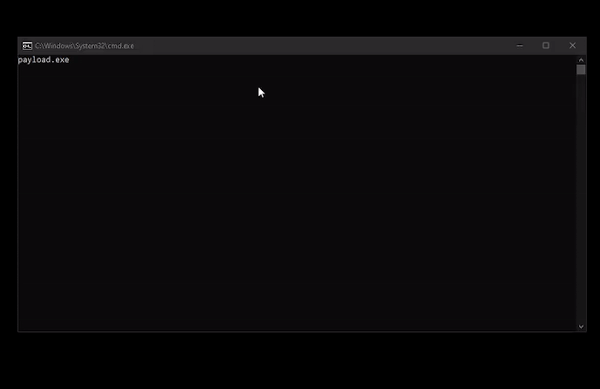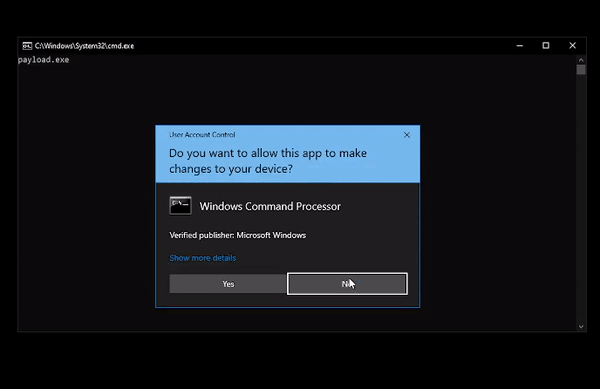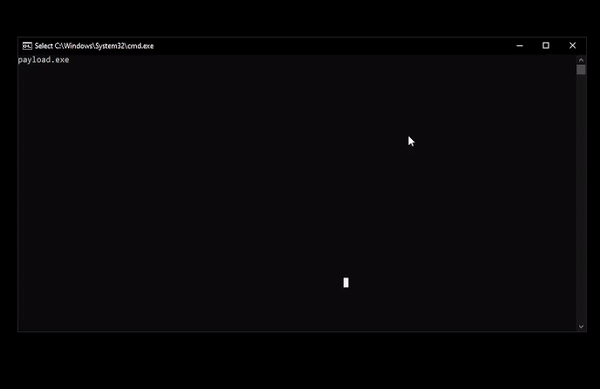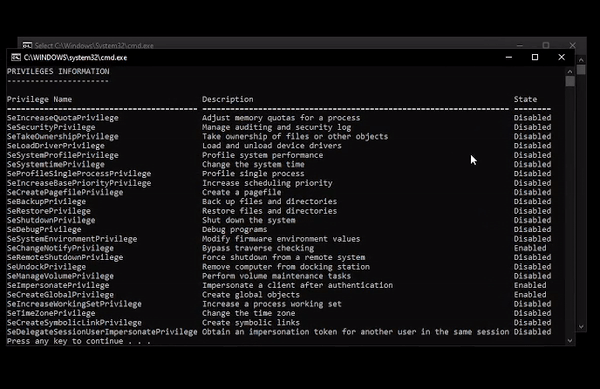
ForceAdmin ForceAdmin is a c# payload builder, creating infinite UAC pop-ups until the user allows the program to be run. The inputted commands are run via powershell calling cmd.exe and...
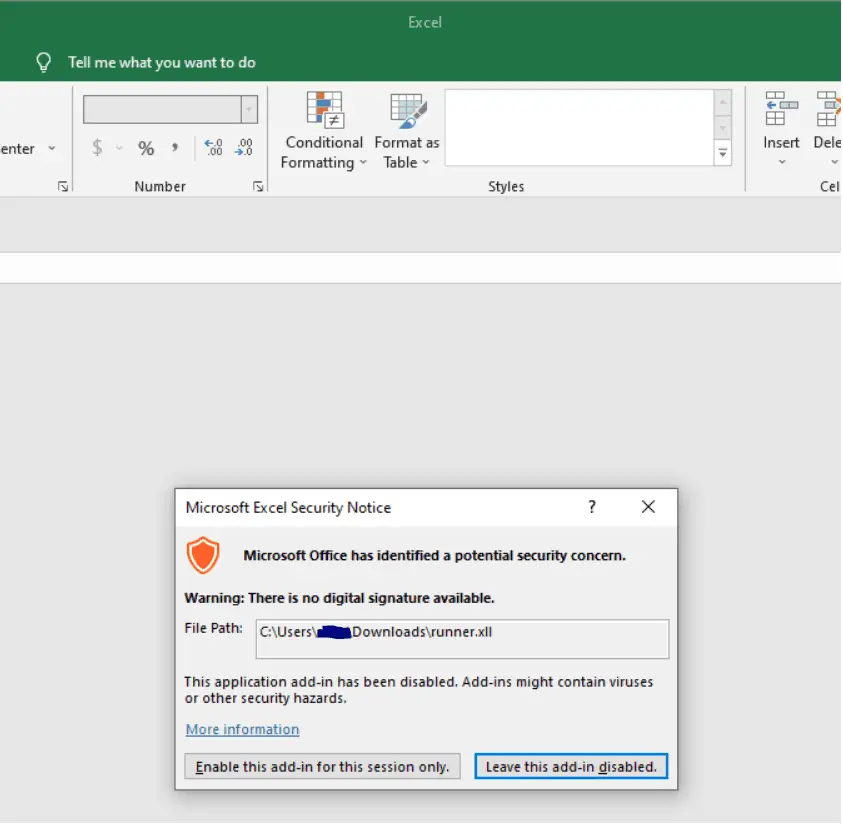
XLL_Phishing Introduction With Microsoft’s recent announcement regarding the blocking of macros in documents originating from the internet (email AND web download), attackers have begun aggressively exploring other options to achieve user-driven...
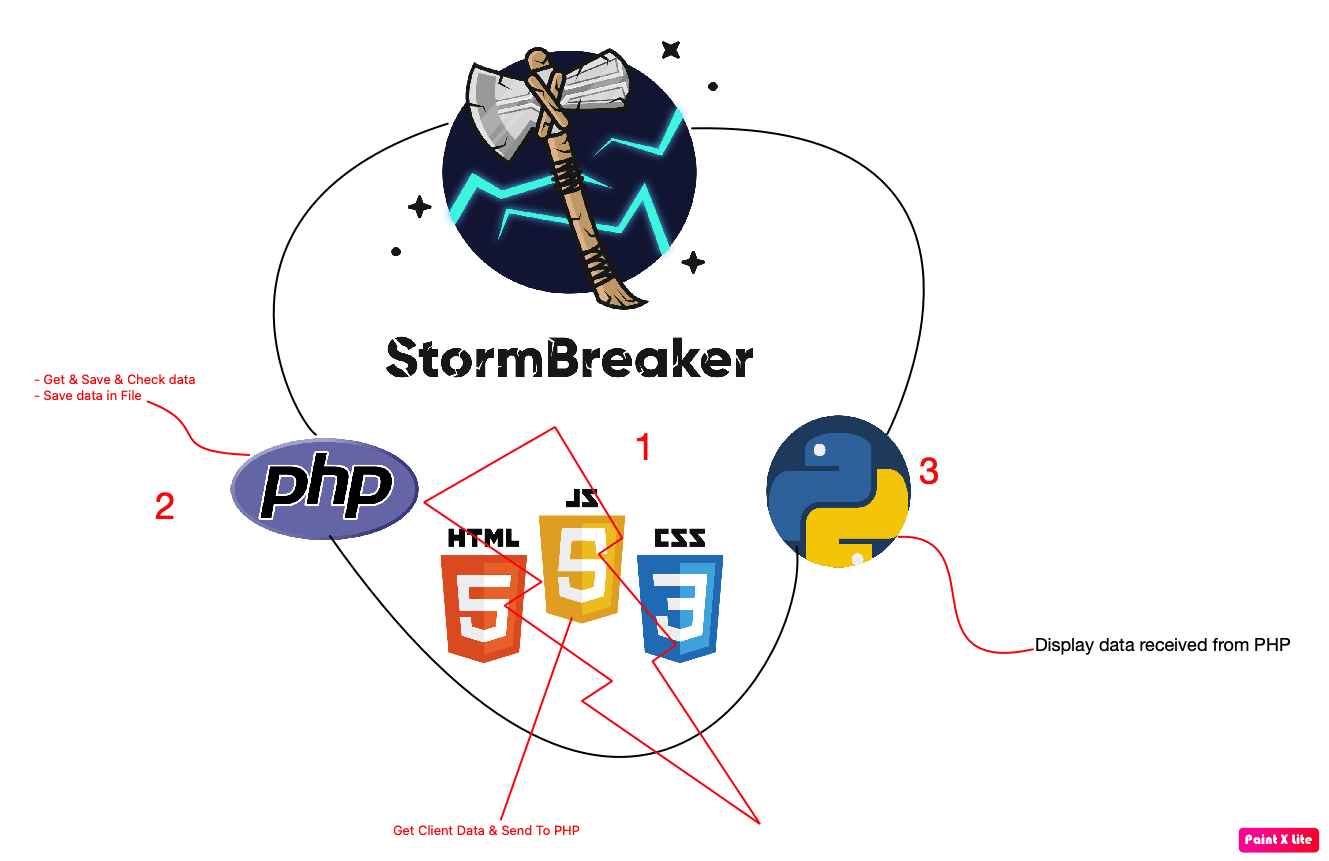
Storm-Breaker Social engineering tool [Access Webcam & Microphone & Location Finder] With Python Features: Get Device Information Without Any Permissions Access Location [SMARTPHONES] Access Webcam Access Microphone Update Log: Second(latest)...
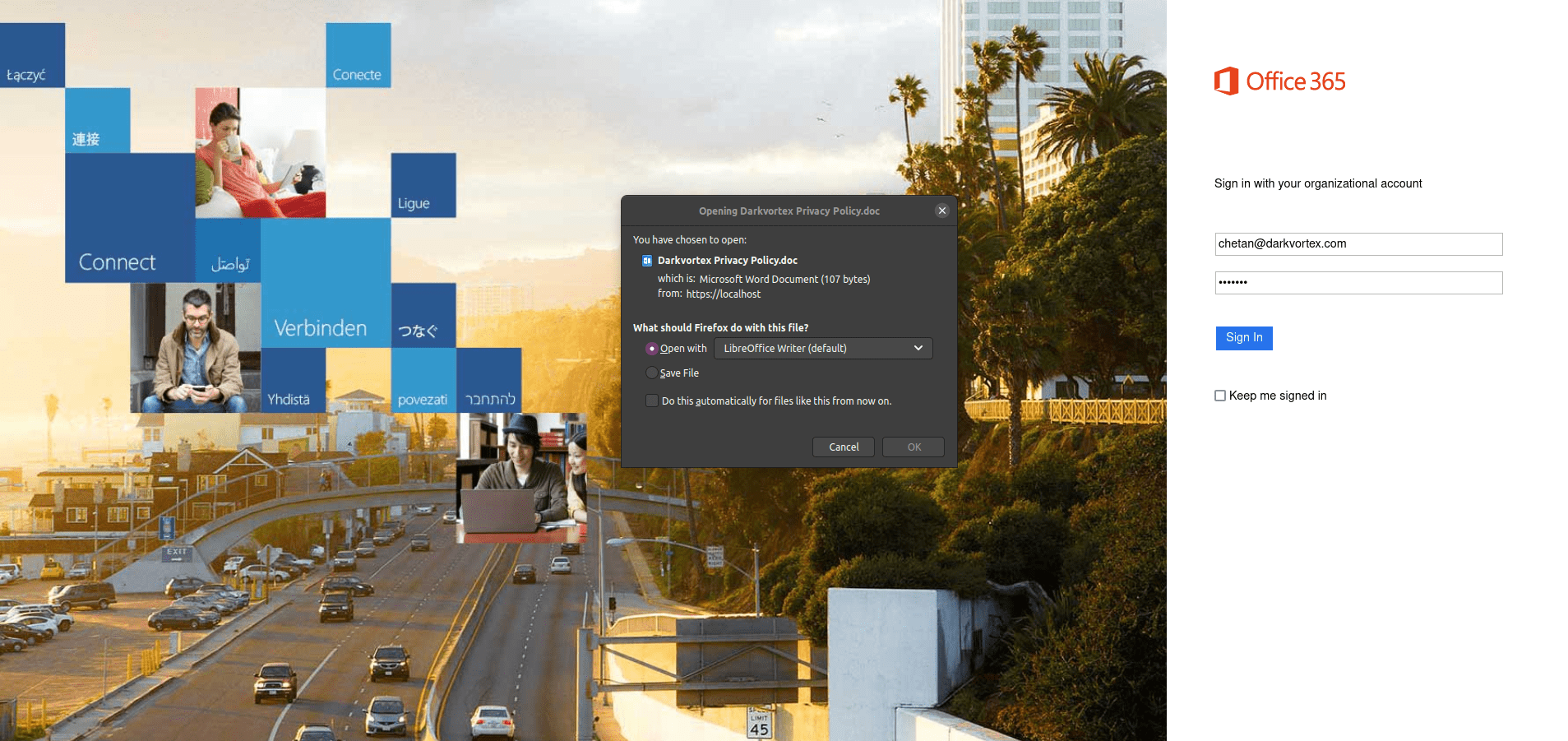
O365-Doppelganger O365-Doppelganger is NOT a replacement for hardcore phishing activities. There are several other tools which perform OAuth and OTA capture which is not the aim of O365-Doppelganger. O365-Doppelganger is...