Category: Vulnerability Analysis
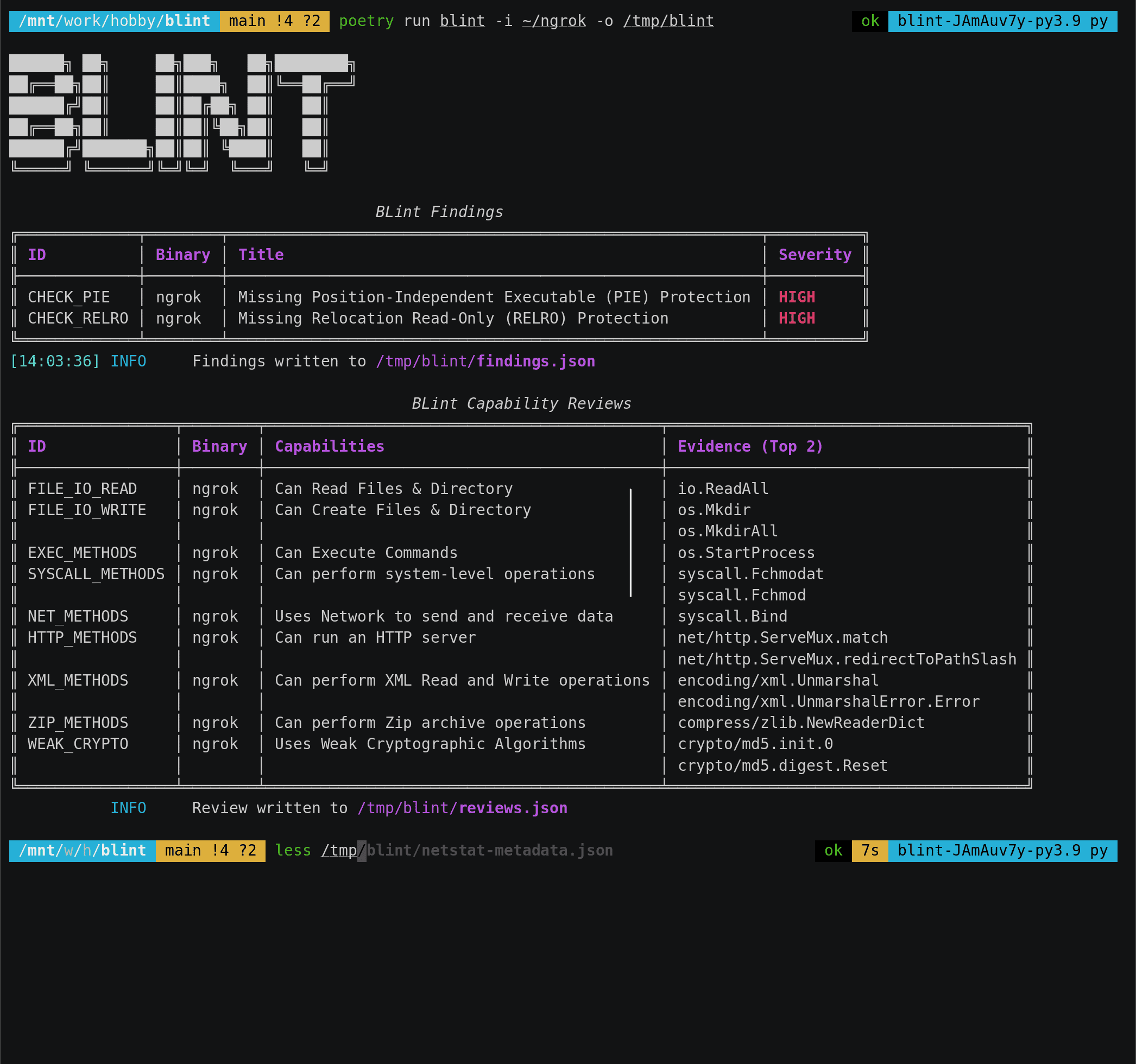
BLint BLint is a Binary Linter to check the security properties and capabilities in your executables. It is powered by lief Supported binary formats: ELF (GNU, musl) PE (exe, dll)...
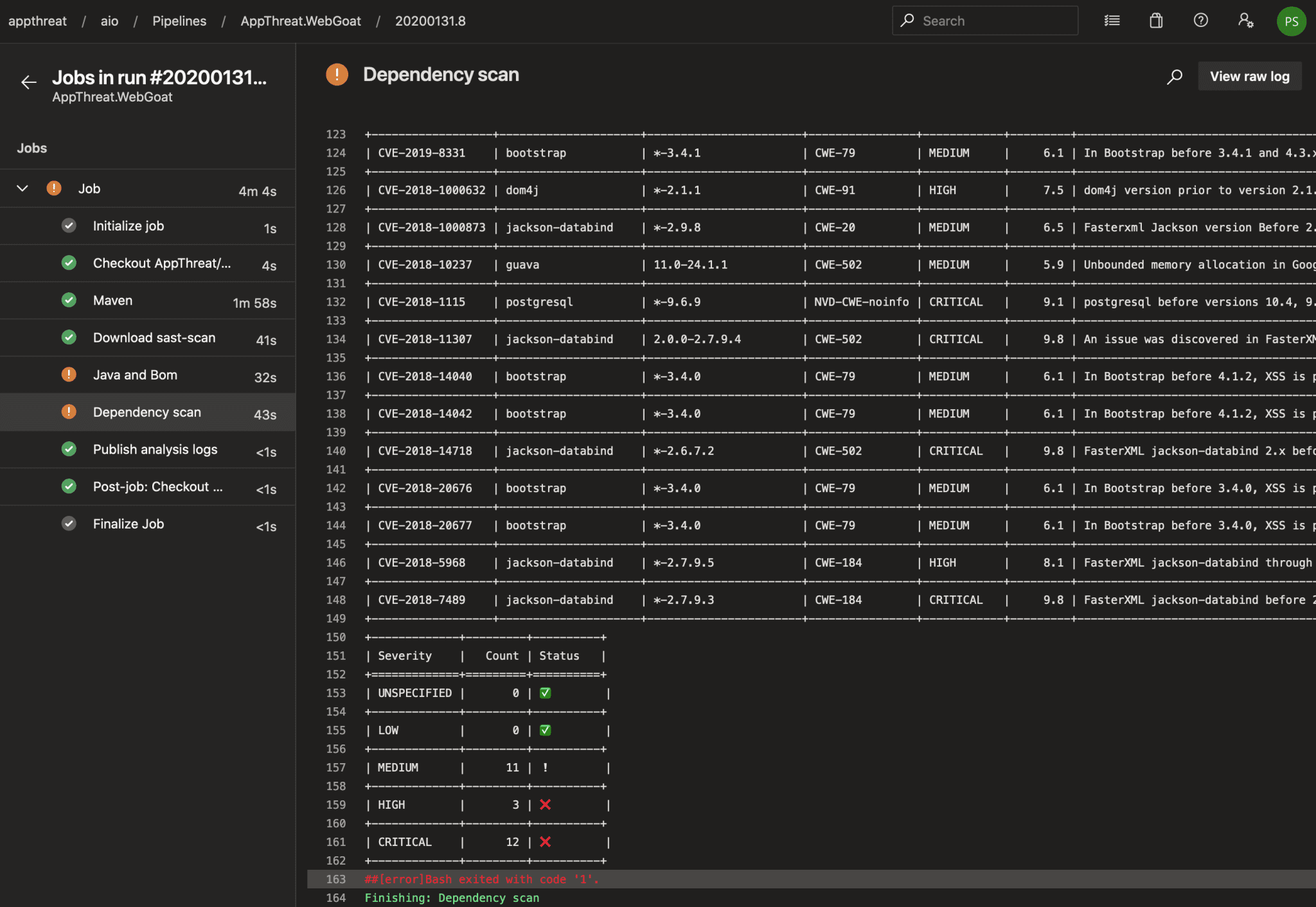
dep-scan dep-scan is a fully open-source security audit tool for project dependencies based on known vulnerabilities, advisories, and licenses limitations. Both local repositories and container images are supported as input....
Microsoft has invested a lot of money in security research. Of course, there is also a detailed bug bounty program to delimit the maximum bounty limit for researchers submitting vulnerabilities....
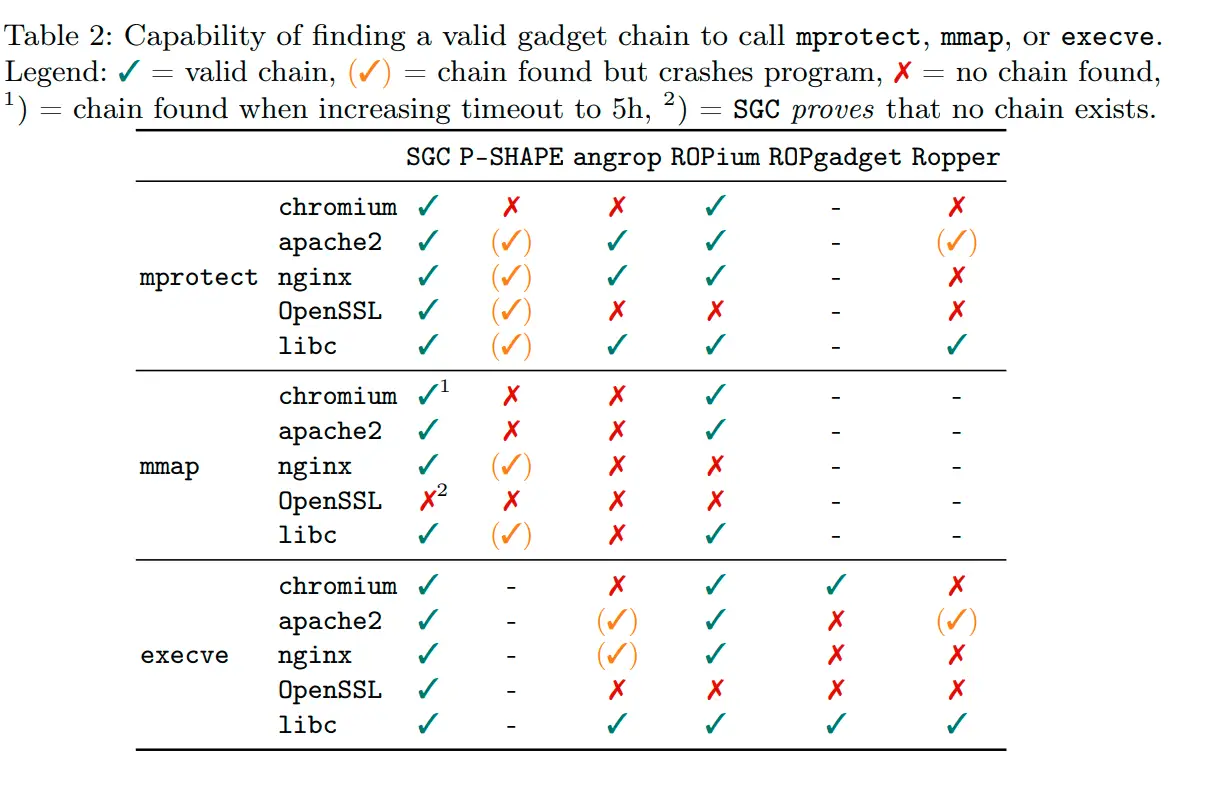
SGC: Towards Automating Code-Reuse Attacks Using Synthesized Gadget Chains SGC is a tool to automatically synthesize gadget chains. It builds a logical formula to encode the execution state at the...
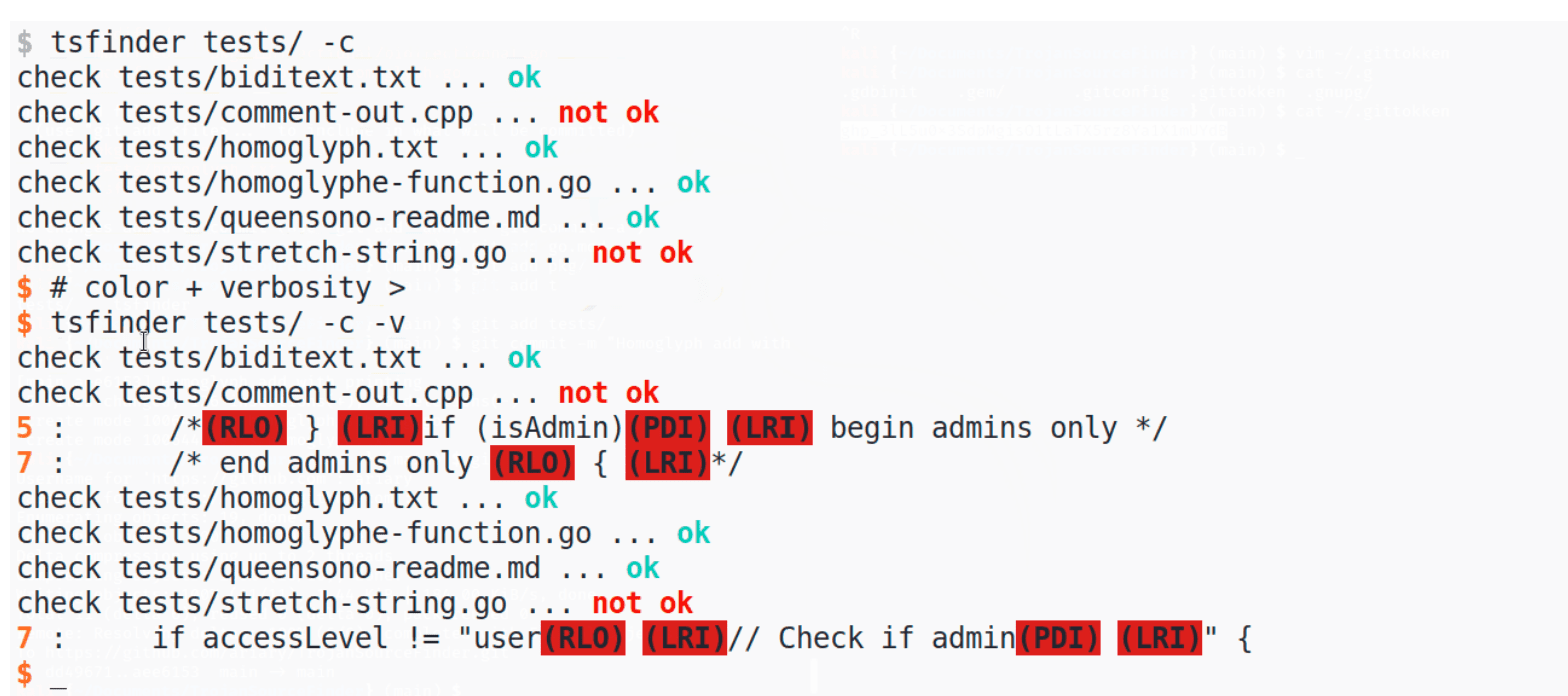
TrojanSourceFinder TrojanSourceFinder helps developers detect “Trojan Source” vulnerability in source code. Trojan Source vulnerability allows an attacker to make malicious code appear innocent. In general, the attacker tries to lure...
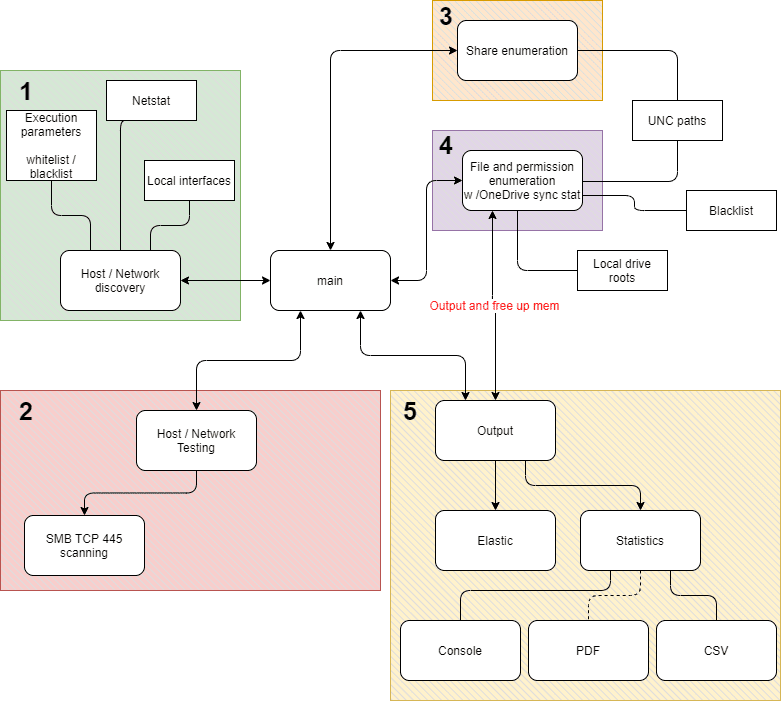
SMBeagle SMBeagle is an (SMB) fileshare auditing tool that hunts out all files it can see in the network and reports if the file can be read and/or written. All...
mesh-kridik Enhance your Kubernetes service mesh security !! mesh-kridik is an open-source security scanner that performs various security checks on a Kubernetes cluster with istio service mesh and outputs a...
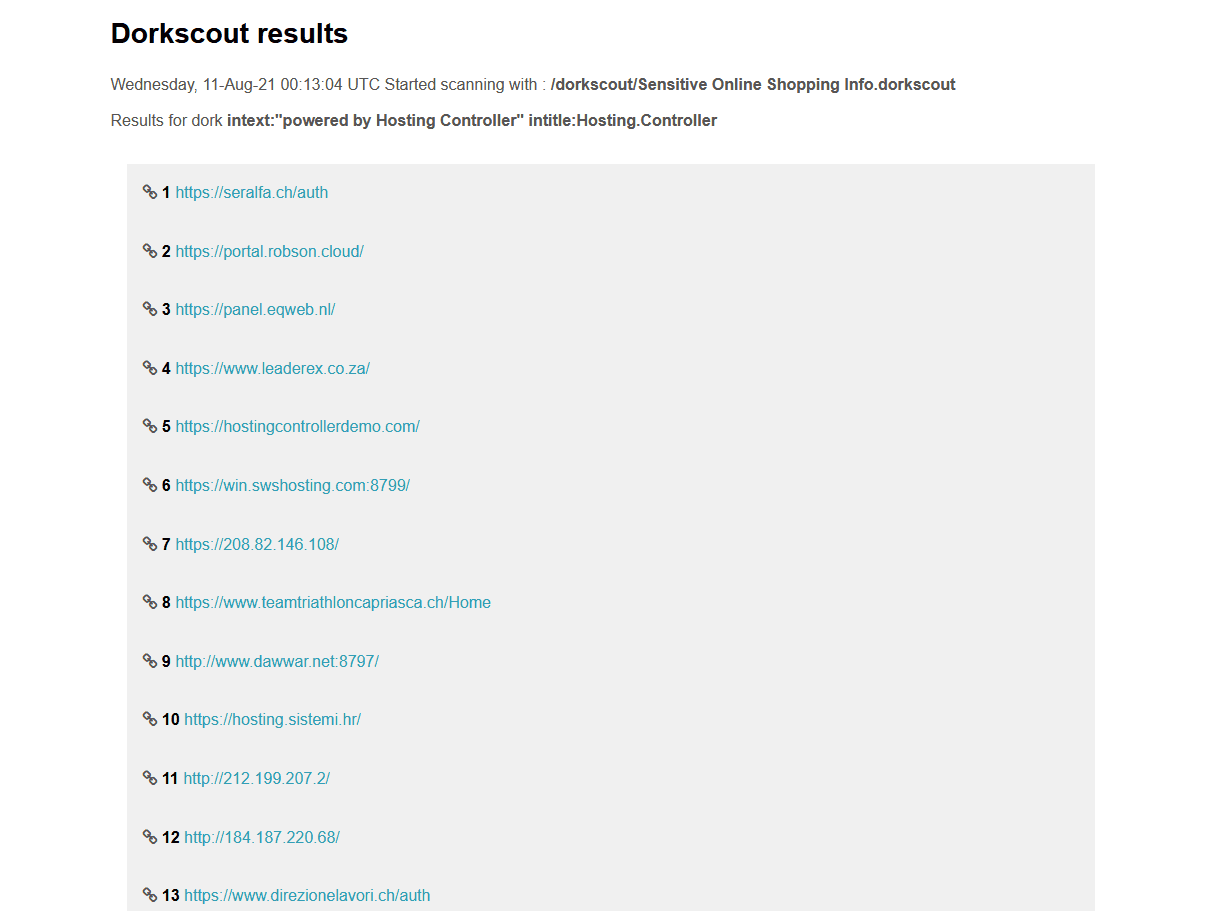
dorkscout dokrscout is a tool to automate the finding of vulnerable applications or secret files around the internet through google searches, dorkscout first starts by fetching the dorks lists from...
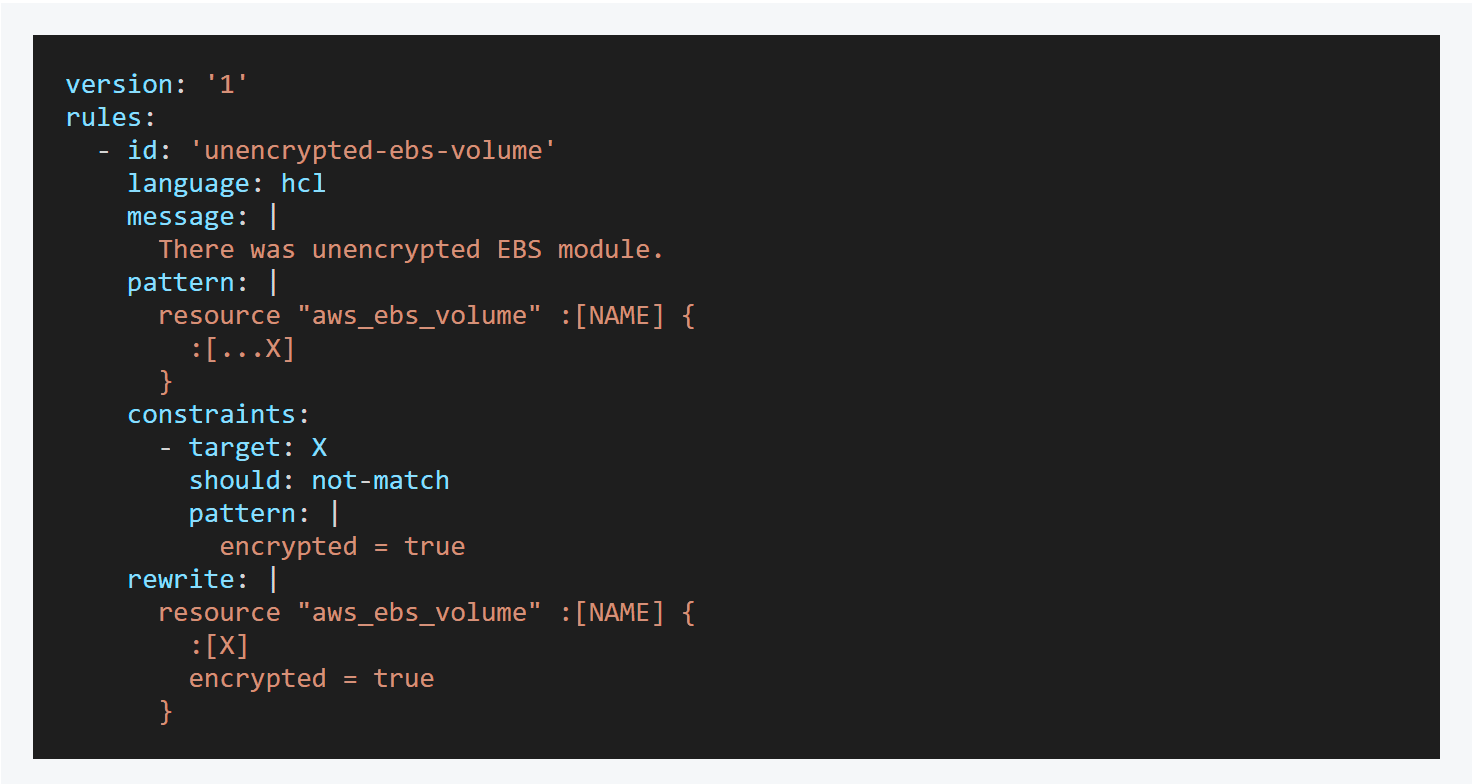
shisho Shisho is a lightweight static code analyzer designed for developers and security teams. The key motivation of Shisho is providing a means of Security-as-Code for Code. It allows us to analyze...
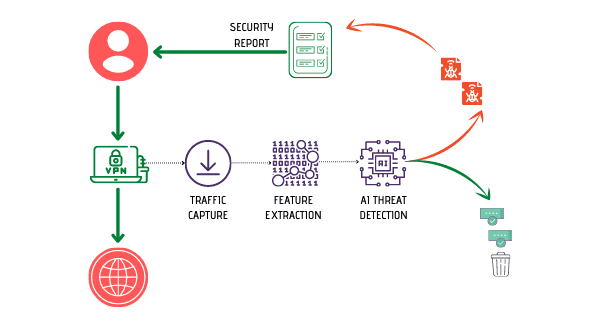
Civilsphere AI VPN The goal of this project is to better protect the privacy of civil society by researching and developing a locally and easy-to-implement VPN that checks the traffic...
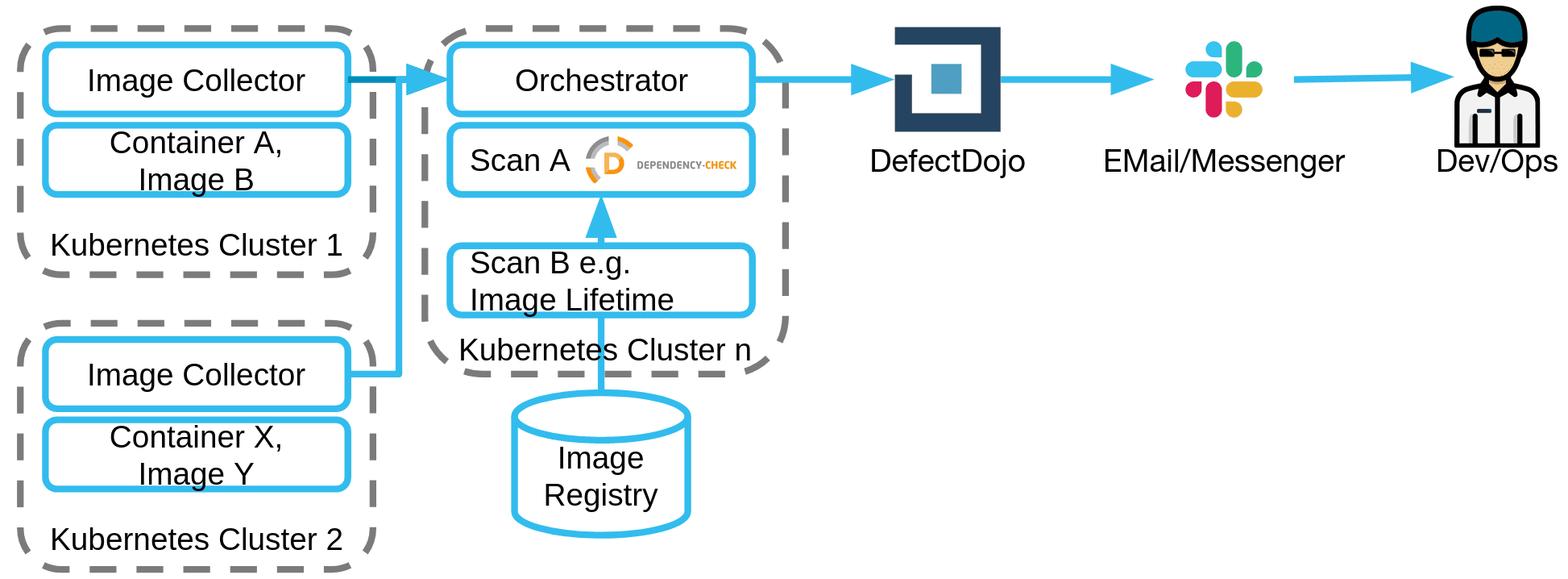
Cluster Scanner The Cluster Scanner detects images in a Kubernetes cluster and provides fast feedback based on various security tests. It is recommended to run the Cluster Scanner in production...
adalanche – Active Directory ACL Visualizer and Explorer Active Directory security is notoriously difficult. Small organizations generally have no idea what they’re doing, and way too many people are just...
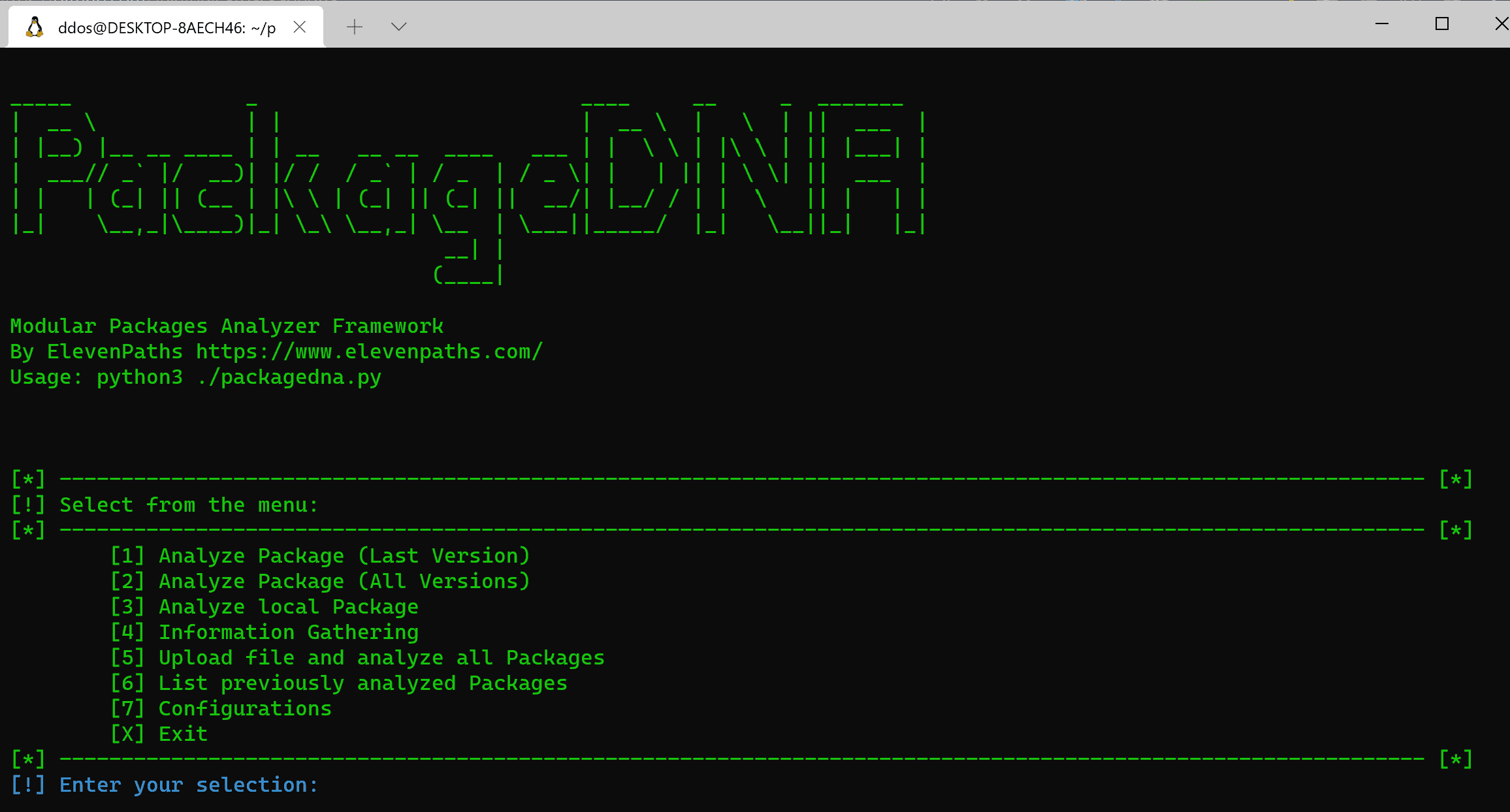
PackageDNA This tool gives developers, researchers, and companies the ability to analyze software packages of different programming languages that are being or will be used in their codes, providing information...
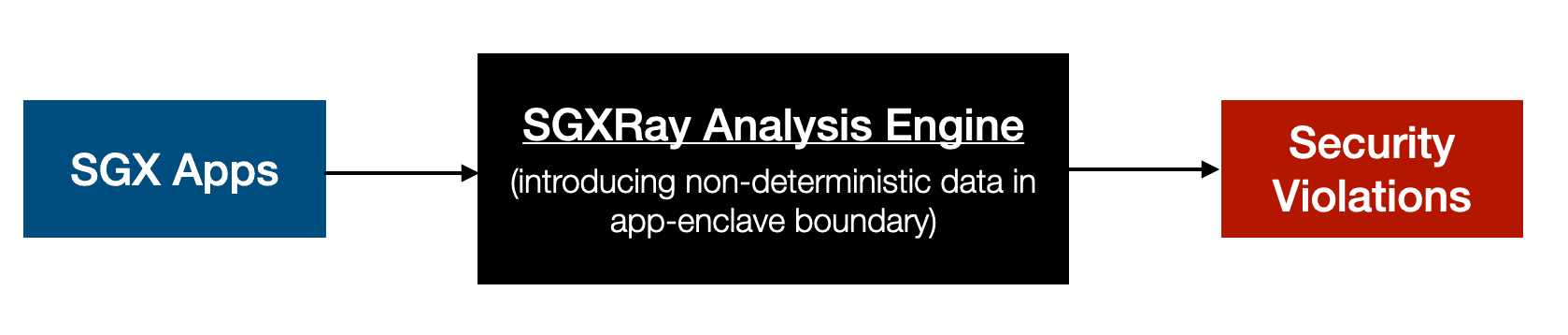
SGXRay: Automating Vulnerability Detection for SGX Apps Intel SGX protects isolated application logic and sensitive data inside an enclave with hardware-based memory encryption. To use such hardware-based security mechanism requires...
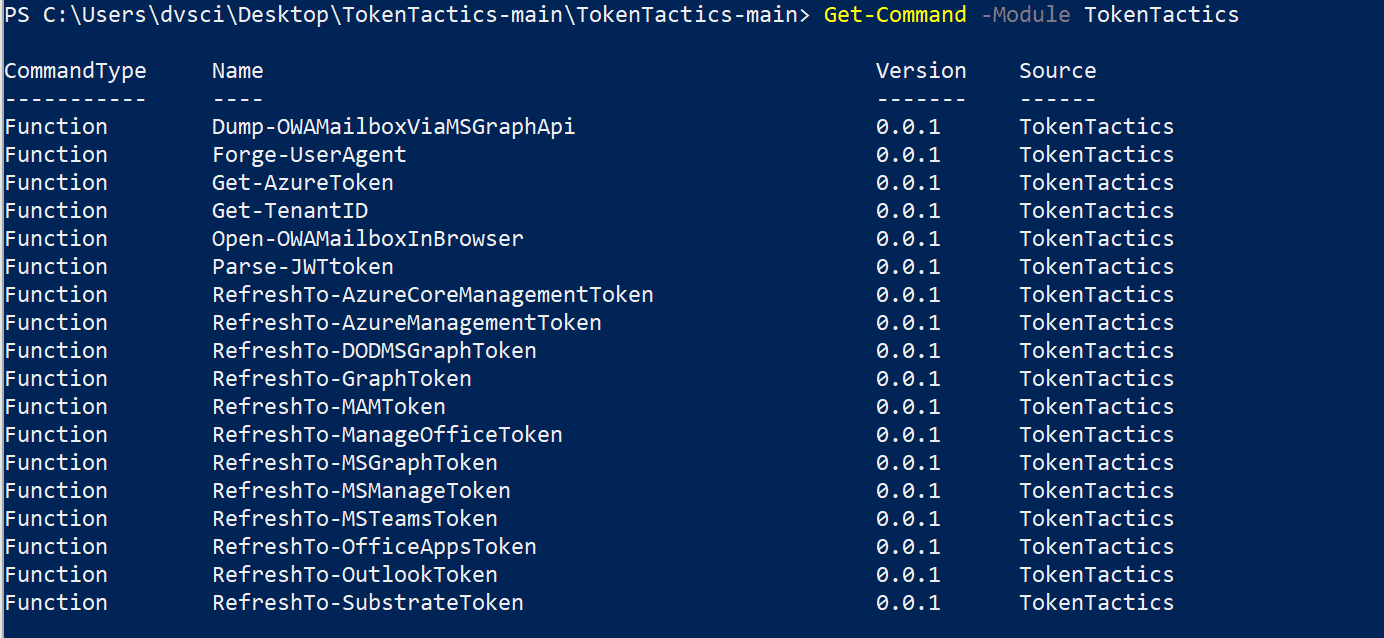
TokenTactics Azure JSON Web Token (“JWT”)Token Manipulation Toolset Azure JWT’s allow you to authenticate to certain endpoints as the user who signed in with the device code. Even if they...