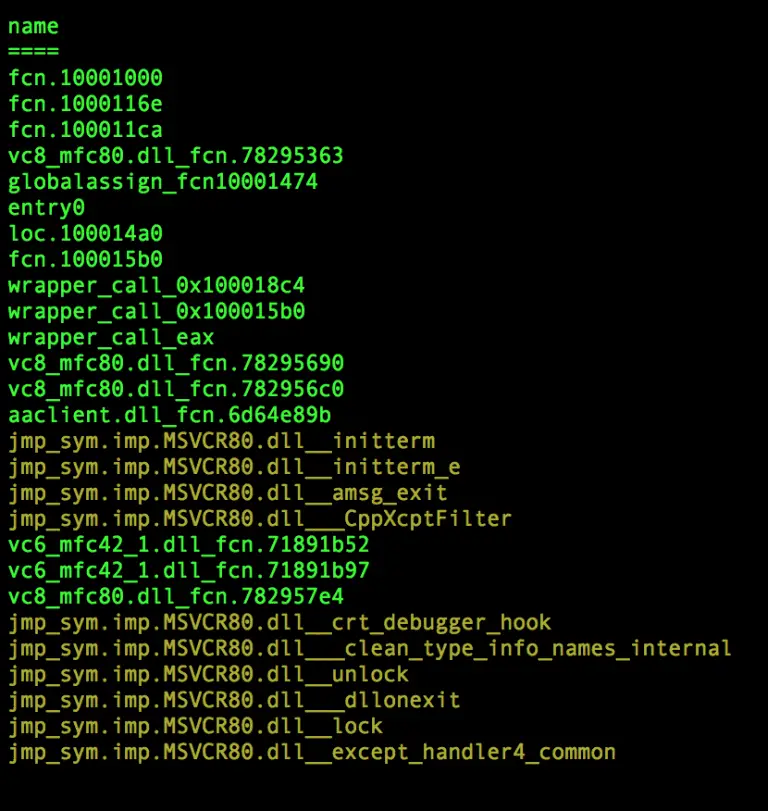
r2kit Overview r2kit is a set of scripts to help with a workflow for malware code analysis...
Reverse Engineering
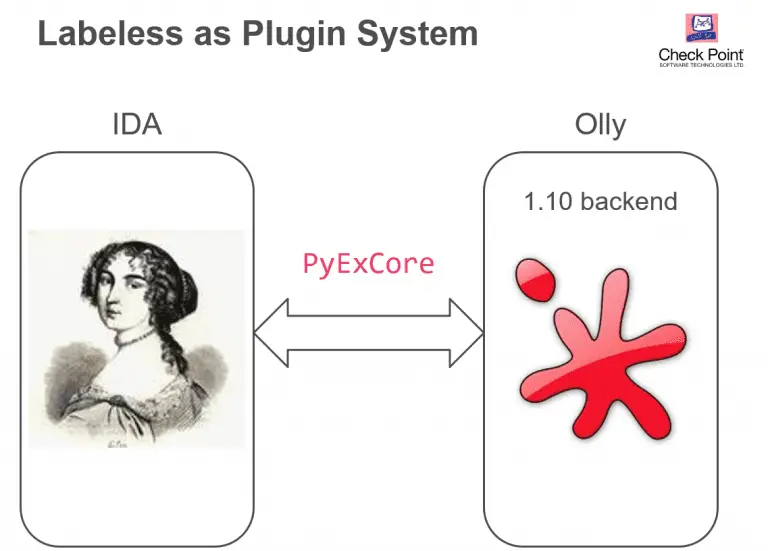
labeless Labeless is a plugin system for dynamic, seamless and real-time synchronization between IDA Database and debugs backend....
exploit_me Very vulnerable ARM/ARM64 application (CTF style exploitation tutorial for ARM/ARM64, but portable to other platforms). Why:...
Shed is an application that allows inspecting the .NET runtime of a program in order to extract useful...
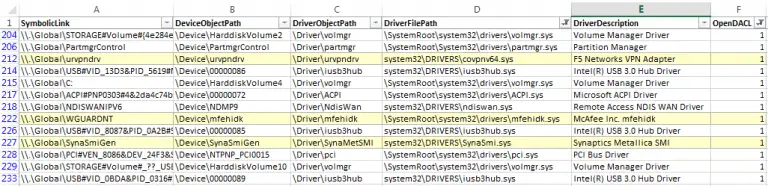
DIRT: Driver Initial Reconnaissance Tool get an initial assessment of drivers installed on a Windows system (e.g....
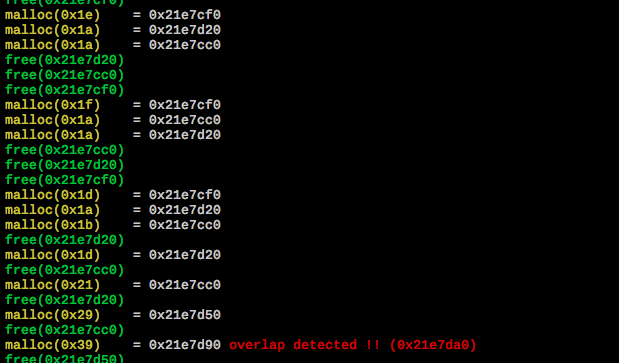
beebug beebug is a tool that can be used to verify if a program crash could be exploitable....
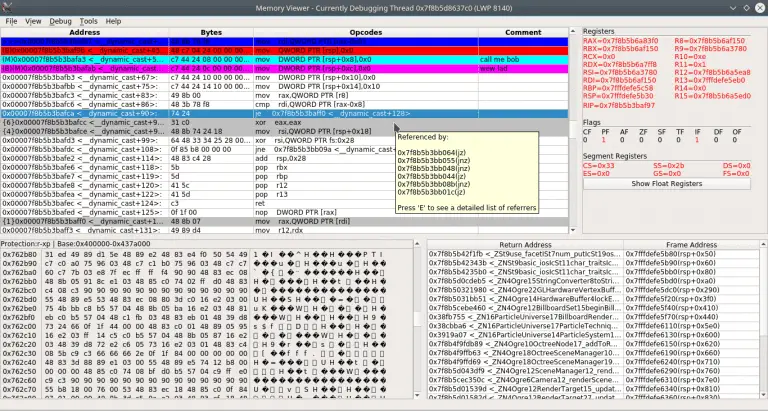
PINCE PINCE is a front-end/reverse engineering tool for the GNU Project Debugger (GDB), focused on games. However,...
Lighthouse – Code Coverage Explorer for IDA Pro Overview Lighthouse is a code coverage plugin for IDA Pro....
Adhrit is an open source Android APK reversing and analysis tool that can help security researchers and...
HITCON-Training For Linux binary Exploitation Outline Basic Knowledge Introduction Reverse Engineering Static Analysis Dynamic Analysis Exploitation Useful...
IDArling is a collaborative reverse engineering plugin for IDA Pro and Hex-Rays. It allows synchronizing in real-time the changes made...
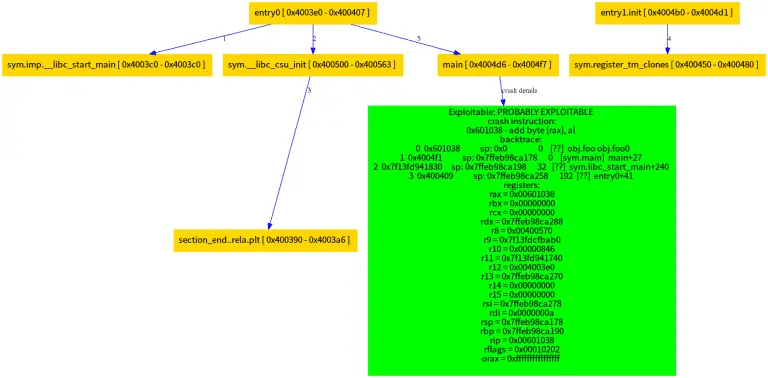
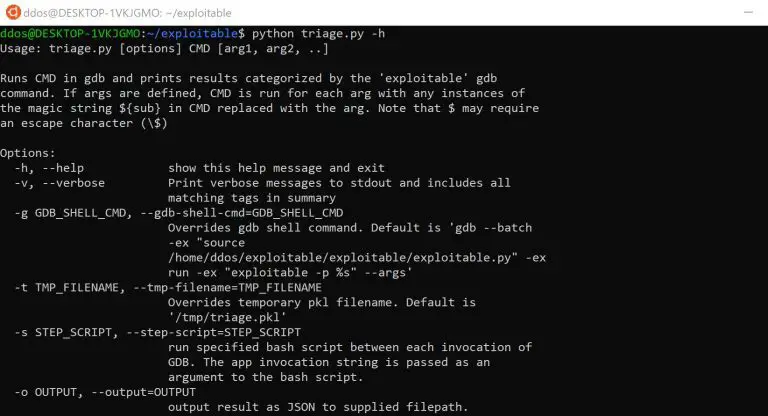
GDB ‘exploitable’ plugin The ‘exploitable’ plugin (exploitable/exploitable.py) ‘exploitable’ is a GDB extension that classifies Linux application bugs...
Exploit-Challenges Here are a collection of vulnerable ARM binaries designed for beginner vulnerability researchers & exploit developers...
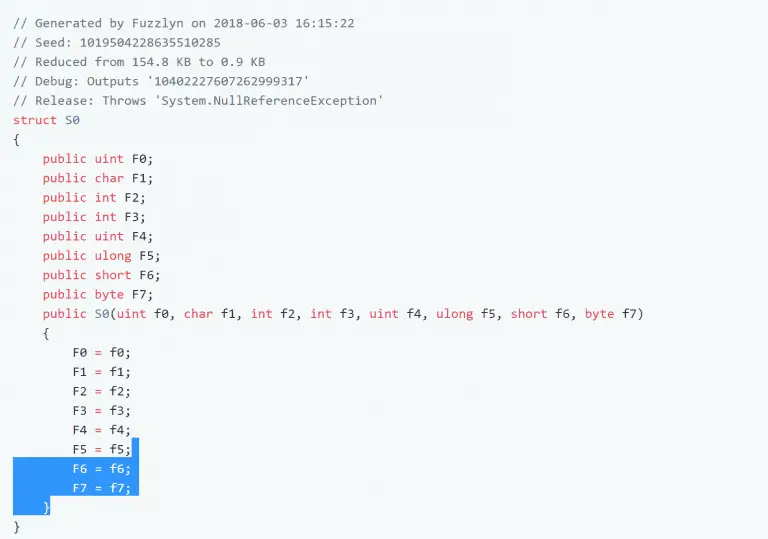
Fuzzlyn Fuzzlyn is a fuzzer which utilizes Roslyn to generate random C# programs. It runs these programs...
Triton is a dynamic binary analysis (DBA) framework. It provides internal components like a Dynamic Symbolic Execution (DSE)...