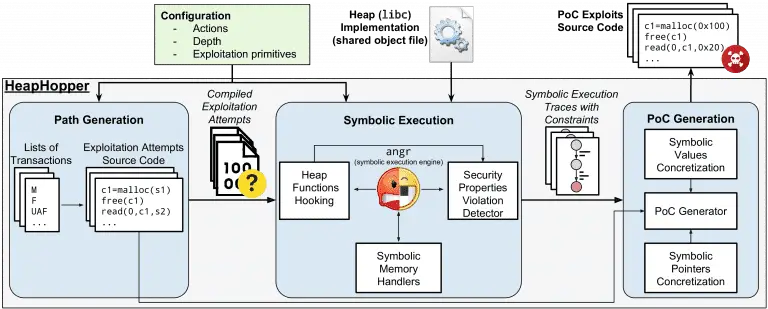
HeapHopper is a bounded model checking framework for Heap-implementations. HEAPHOPPER’s goal is to evaluate the exploitability of...
Reverse Engineering
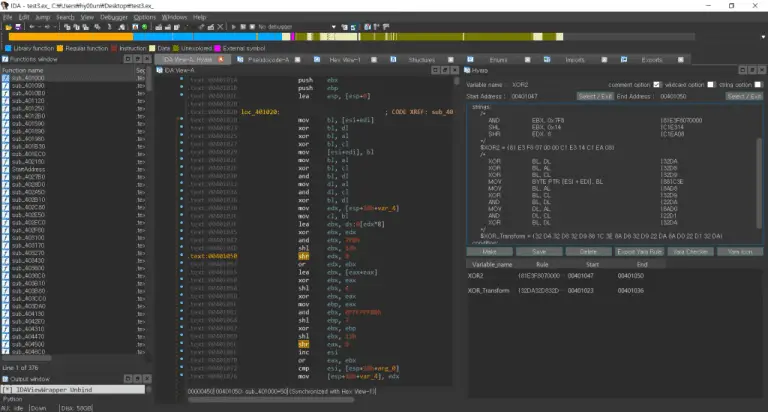
YaCo – Collaborative Reverse-Engineering for IDA YaCo is a Hex-Rays IDA plugin enabling collaborative reverse-engineering on IDA databases for multiple...
Xori – Custom disassembly framework Xori is an automation-ready disassembly and static analysis library that consumes shellcode...
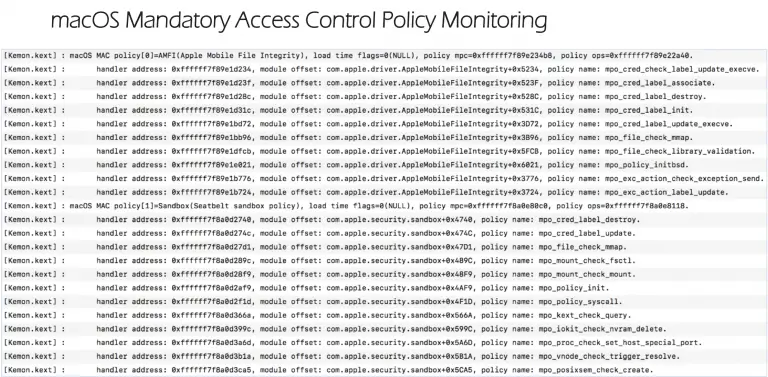
Kemon An Open-Source Pre and Post Callback-Based Framework for macOS Kernel Monitoring. With the power of it,...
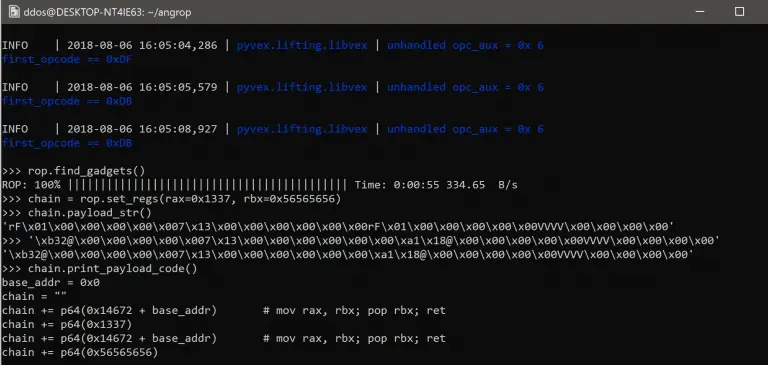
angrop angrop is a rop gadget finder and chain builder Overview angrop is a tool to automatically...
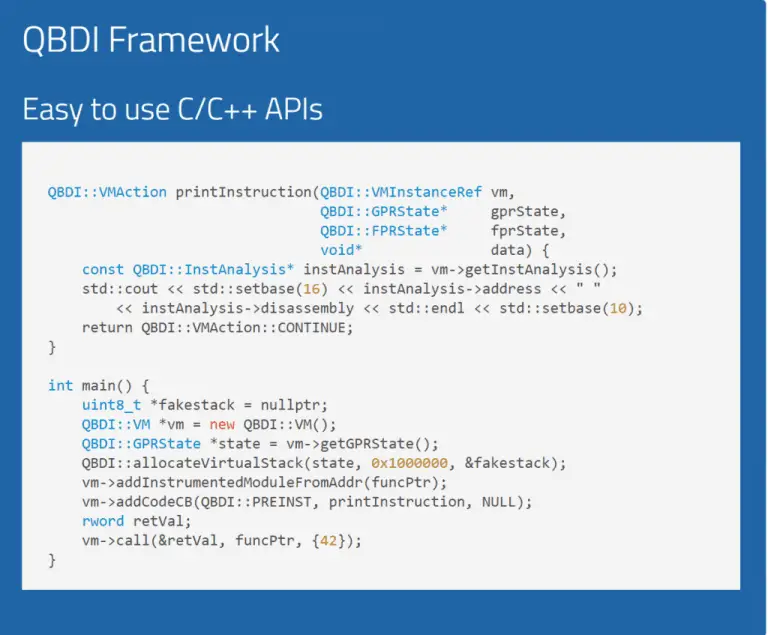
QuarkslaB Dynamic Binary Instrumentation (QBDI) is a modular, cross-platform, and cross-architecture DBI framework. It aims to support...
Hyara (IDA Plugin) Hyara is IDA Plugin that provides convenience when writing yard rules. You can designate...
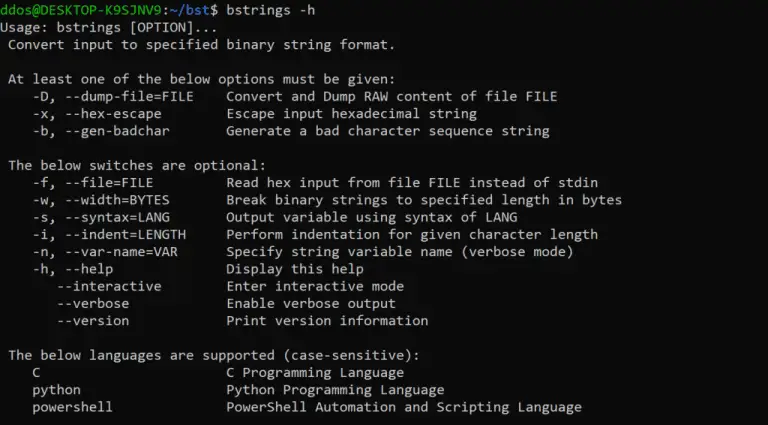
Binary String Toolkit Summary The Binary String Toolkit or BST for short is a rather simple utility...
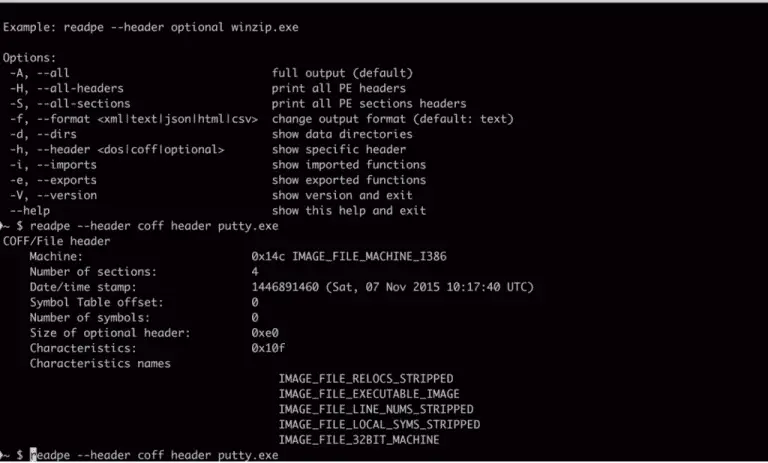
readpe readpe is a full-featured, open-source, multiplatform command-line toolkit to work with PE (Portable Executables) binaries. Use...
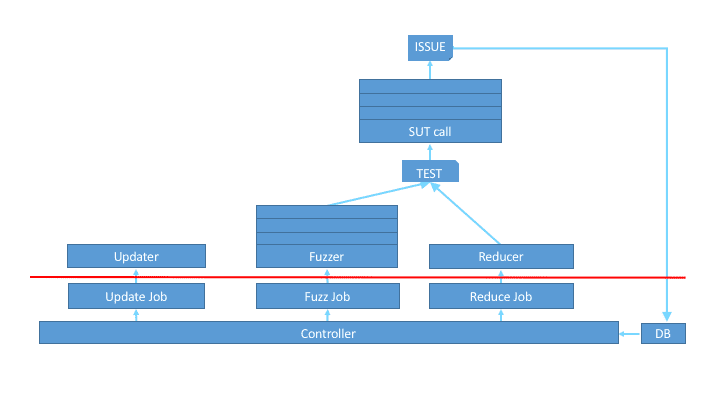
Fuzzinator Fuzzinator is a framework helping you to deal with the common fuzzing tasks, like running fuzz jobs,...
xAnalyzer is a plugin for the x86/x64 x64dbg debugger by @mrexodia. This plugin is based on the APIInfo...
SwishDbgExt is a Microsoft WinDbg debugging extension that expands the set of available commands by Microsoft WinDbg,...
angr angr is a platform-agnostic binary analysis framework developed by the Computer Security Lab at UC Santa...
arm_now is a qemu powered tool that allows instant setup of virtual machines on arm CPU, mips,...
Frick Frick is a kick-ass Frida cli for reverse engineer inspired by the epic GDB init gef...