Mustang Panda Campaign Overview
Vietnamese organizations and individuals have become the latest targets of Mustang Panda, a notorious Chinese cyber espionage group. According to recent findings by Cyble Research and Intelligence Labs (CRIL), Mustang Panda has been conducting a series of targeted attacks since April 2024, focusing on entities with interests in tax compliance and education.
Mustang Panda, first observed in 2017, has likely been operational since at least 2014. This threat actor group (TA) has a history of targeting a wide array of entities across the U.S., Europe, Mongolia, Myanmar, Pakistan, and Vietnam. In May 2024, Mustang Panda launched a campaign targeting Vietnamese entities with lures related to tax compliance. This campaign followed a similar attack in April 2024, which targeted entities interested in the education sector.
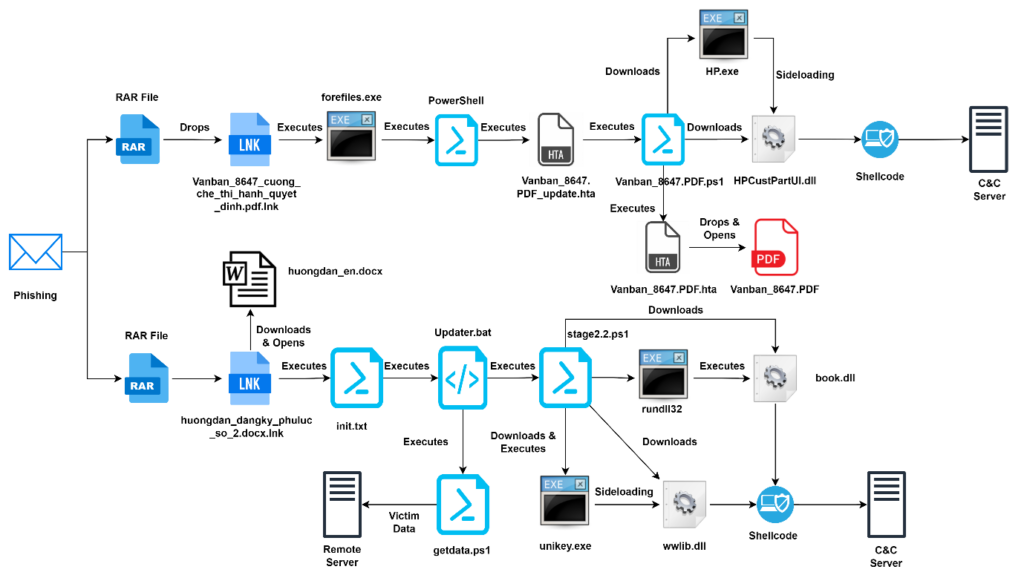
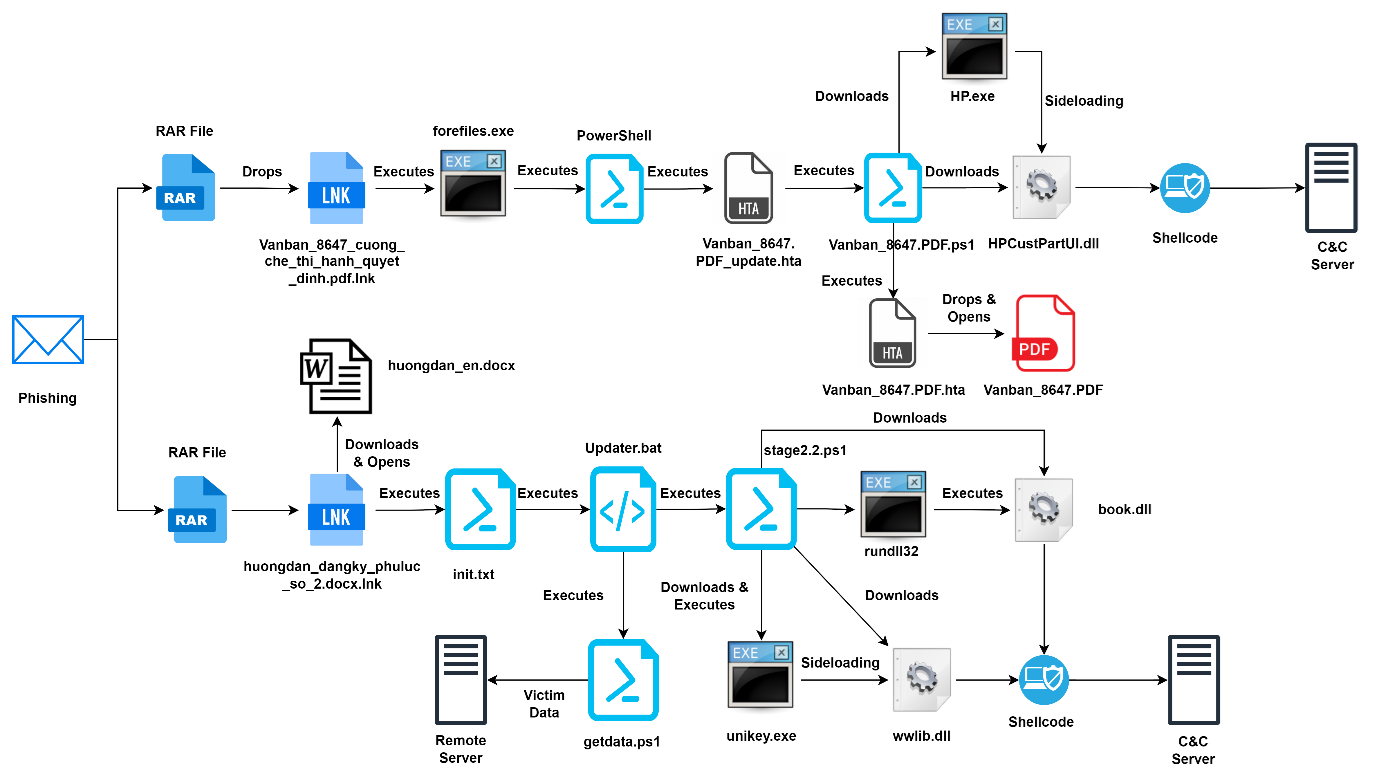
The May 2024 campaign began with spam emails containing malicious attachments, specifically Windows shortcut (LNK) files disguised as PDF documents. These LNK files, such as “Vanban_8647_cuong_che_thi_hanh_quyet_dinh.pdf.lnk,” were designed to evade detection by security software. The LNK file, once executed, abused the legitimate Windows executable “forfiles.exe” to initiate further infection stages. This involved downloading and executing a malicious HTA file hosted on a remote server.
The malicious LNK file executed the following command:
The HTA file contained obfuscated VBScript, which, upon deobfuscation, executed a PowerShell command to download and run a remote script. This script further downloaded additional payloads, including a DLL loader and other malicious files, which facilitated data exfiltration and further compromised the system.
One of the notable techniques used in this campaign was DLL sideloading. The downloaded PowerShell script dropped three files: “HP.exe” (a legitimate executable), “HPCustPartUI.dll” (a malicious DLL), and “Vanban_8647.PDF.hta.” The script then used the legitimate “HP.exe” to load the malicious DLL, which in turn executed additional malicious activities, including downloading an encrypted file from a remote server.
In addition to the May 2024 campaign, CRIL identified a related campaign from April 2024. This earlier campaign used similar tactics but targeted individuals interested in the education sector. The malicious LNK files in this campaign also employed double extensions to masquerade as legitimate documents. The infection chain involved downloading and executing PowerShell scripts that further compromised the system.
Mustang Panda’s primary objective appears to be the exfiltration of sensitive information, as the malware collects extensive system data and transmits it to a command-and-control (C&C) server. CRIL researchers suspect that the group may be deploying the PlugX Remote Access Trojan (RAT), granting them complete control over infected machines.
This campaign underscores the ongoing threat posed by state-sponsored cyber espionage groups like Mustang Panda, and the need for heightened vigilance and robust security measures to protect against these sophisticated attacks.