A recent report from Cisco Talos has revealed a sophisticated cyberattack targeting a Taiwanese government-affiliated research institute. The attack, believed to have been carried out by the Chinese state-sponsored group APT41, utilized a combination of advanced tactics and known malware like ShadowPad and Cobalt Strike.
The evidence overwhelmingly points towards APT41, a notorious Chinese state-sponsored hacking group with a history of targeting high-value entities to steal intellectual property and sensitive data. This assessment is based on the use of ShadowPad, a malware exclusively linked to Chinese threat actors, along with the presence of Simplified Chinese language elements within the attack tools.
The attack was not a single strike but a meticulously planned operation that unfolded over several weeks. The attackers employed a variety of intrusion methods, showcasing their adaptability and determination to gain and maintain access to the target network. This multi-pronged approach involved the use of webshells, RDP access, and reverse shells, making detection and eradication more challenging. Further evidence of their sophistication includes attempts to exploit a known vulnerability (CVE-2018-0824) to escalate privileges.
The attackers employed multiple sophisticated methods to establish and maintain their foothold in the compromised environment:
- Webshell Installation: A webshell was installed on the webserver to facilitate further malicious activities.
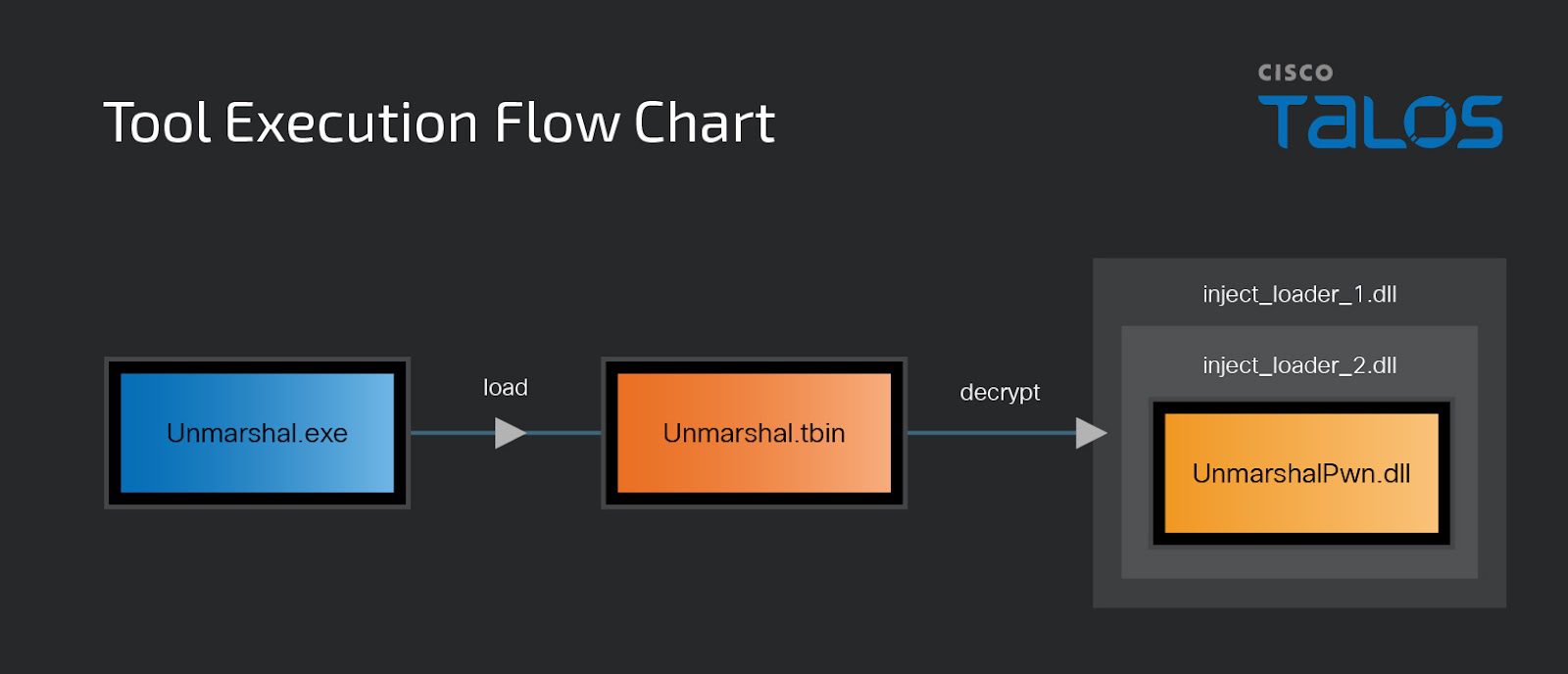
- Multiple Malware Drops: ShadowPad and Cobalt Strike were deployed using webshells, Remote Desktop Protocol (RDP) access, and reverse shells. The Cobalt Strike loader, written in GoLang, was designed to evade detection by Windows Defender.
- Stealth and Persistence: To avoid detection, the attackers executed PowerShell commands to download additional scripts and used a unique Cobalt Strike loader developed from an open-source project hosted on GitHub, written in Simplified Chinese.
Once inside the network, the attackers focused on harvesting credentials and exfiltrating data:
- Credential Harvesting: Tools like Mimikatz and WebBrowserPassView were used to obtain passwords stored in web browsers and hashes from the lsass process.
- Network Discovery: The attackers ran commands such as “net,” “whoami,” and “ipconfig” to gather information about user accounts, directory structures, and network configurations.
- Data Exfiltration: Compressed and encrypted files were exfiltrated using backdoors to communicate with the C2 server.
While the attack’s full impact is still being assessed, it’s clear that the primary objective was information theft. The attackers harvested passwords and systematically gathered sensitive data from the compromised network, potentially including valuable research findings, intellectual property, and confidential government information. The implications of this data breach could be far-reaching, affecting national security, economic competitiveness, and even international relations.
Related Posts:
- Cyber Espionage Alert: APT41 Strikes Global Industries, Steals Sensitive Data
- ThreatMon Revealed APT41’s Stealthy PowerShell Backdoor
- 160GB of confidential data leaked, PC giant Acer confirms its servers were hacked
- North Korean Hackers Exploit Old Office Flaw to Deploy Keylogger