CimSweep: perform incident response and hunting operations remotely
CimSweep
CimSweep is a suite of CIM/WMI-based tools that enable the ability to perform incident response and hunting operations remotely across all versions of Windows. CimSweep may also be used to engage in offensive reconnaissance without the need to drop any payload to disk. Windows Management Instrumentation has been installed and its respective service running by default since Windows XP and Windows 2000 and is fully supported in the latest versions of Windows including Windows 10, Nano Server, and Server 2016.
Background
Agent-based defensive tools are extremely powerful but they also require the deployment of the agent to each system. While agent-based solutions absolutely have a place in our industry, they tend to be very expensive and can be easily detected/thwarted by determined attackers. CimSweep enables the acquisition of time-sensitive data at scale all without needing to deploy an agent.
It is called CimSweep based on the fact that it utilizes the extremely powerful CIM cmdlets in PowerShell. CIM cmdlets support the WSMan protocol by default but it may also fall back to using DCOM on systems that either cannot support or do not have the Windows Remote Management (WinRM) service enabled. More information on the CIM cmdlets may be found here:
Core Functionality
At its core, CimSweep makes it easy to remotely obtain the following information from any Windows operating system:
- Registry keys, values, value types, and value content with optional recursion
- Directory and file listing with optional recursion
- Event log entries
- Services
- Processes
This core functionality was designed to facilitate the development of domain-specific functionality for incident responders, hunt operators, or anyone else needing to target information remotely over WMI.
Domain-specific Functionality
Building upon the core set of functions in CimSweep, contributors can easily write functions that enable them to obtain highly targeted information. Examples of such information would include the following:
- Attacker persistence artifacts: Run keys, start menu items, WMI persistence, etc.
- Scan for the presence of known bad artifacts: i.e. sweep for known bad files, known bad registry keys/values
- Use your imagination! CimSweep enables sweeping for a multitude of forensic artifacts. Consider tools like Sysinternals Autoruns and regripper. CimSweep enables contributors to reimplement these awesome tools all without requiring pushing any tools to a target system!
Download
git clone https://github.com/PowerShellMafia/CimSweep.git
Usage
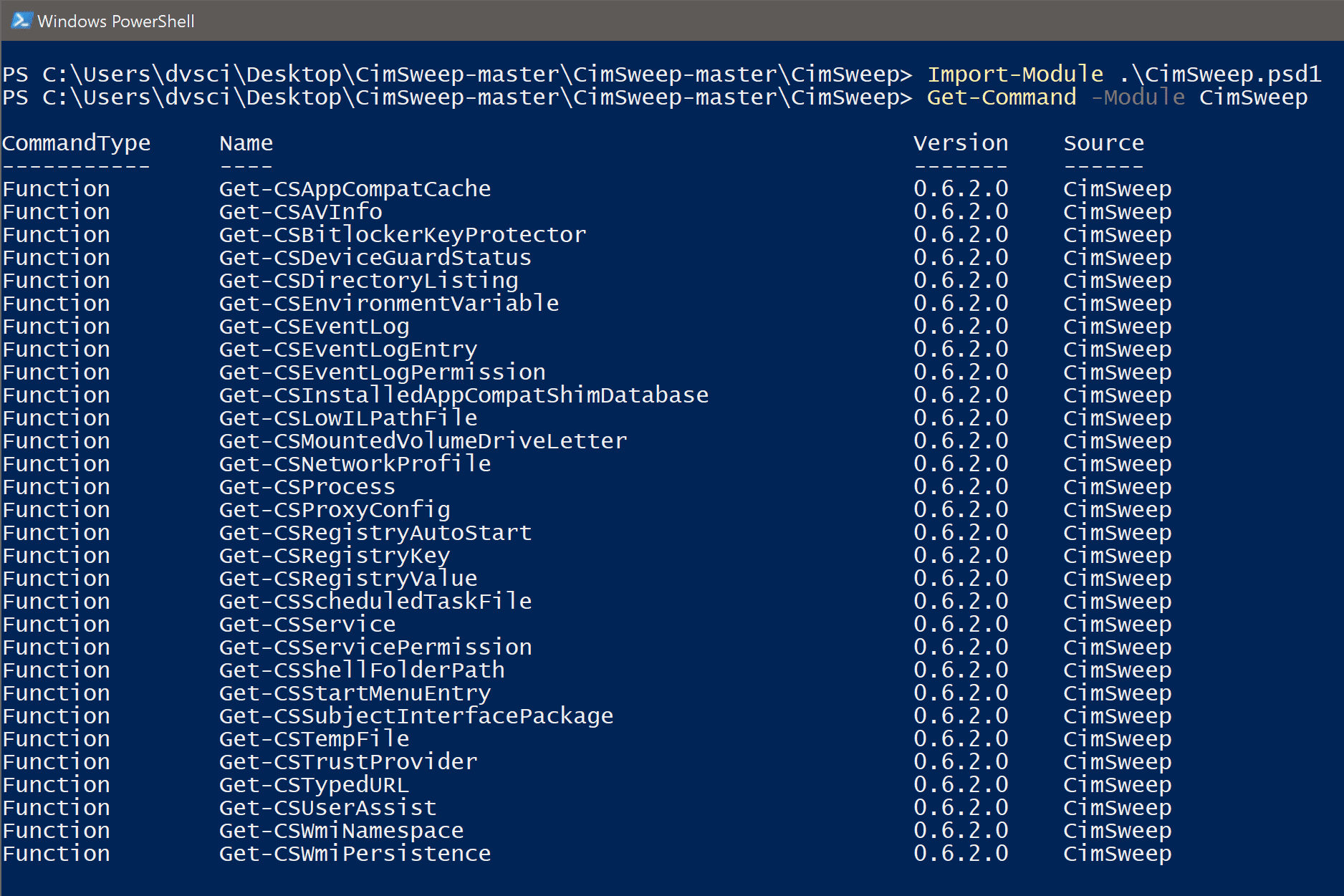
Import-Module .\CimSweep.psd1
Get-Command -Module CimSweep
Copyright (c) 2016, Matt Graeber
All rights reserved.