CIRCO
Cisco Implant Raspberry Controlled Operations
Designed under Raspberry Pi and aimed for Red Team Ops, we take advantage of “Sec/Net/Dev/Ops” enterprise tools to capture network credentials in a stealth mode.
Using low profile hardware & electronics camouflaged as simple network outlet box to be sitting under/over a desk.
CIRCO include different techniques for network data exfiltration to avoid detection.
This tool gathers information and uses a combination of honeypots to trick Automation Systems to give us their network credentials!

Hardware
The specific hardware will depend on the size and features you want, as an example, you can run CIRCO on a Raspberry Pi Zero without a Wireless Extraction feature or you could be using a Raspberry Pi 3B with a wireless dongle.
The main constraint is physical space to fit CIRCO.
You will also need some Cat 5 twisted cable, pliers, RJ45, soldering/desoldering tools, wires, glue-gun, zip-ties, etc
Software
There are 3 main elements that make CIRCO:
- The implant main program called
circo.pywhich also runsshd-fake.pyandtelnetd-fake.pydaemons (honeypots)
To emulate a Cisco Switch SNMP Agent, we are using forked version of snmposter - To receive extracted credentials via different techniques, we use
carpa.pyon an Internet Server, as long is has a public IP and no firewalls in front preventing traffic to reach it. We also need a domain pointing NS records to our public IP - Specific for wireless exfiltration we have
jaula.py, been tested on a Raspberry Pi Zero with a wireless dongle but should run different hardware without issues
Most of the packet manipulation and crafting is been done with Scapy as it has enough flexibility with some exceptions
Demo
CIRCO Demo from Emilio on Vimeo.
Changelog v1.6
- Python 3
- Modular Code
- New exfiltration method (FM)
- Support net-creds
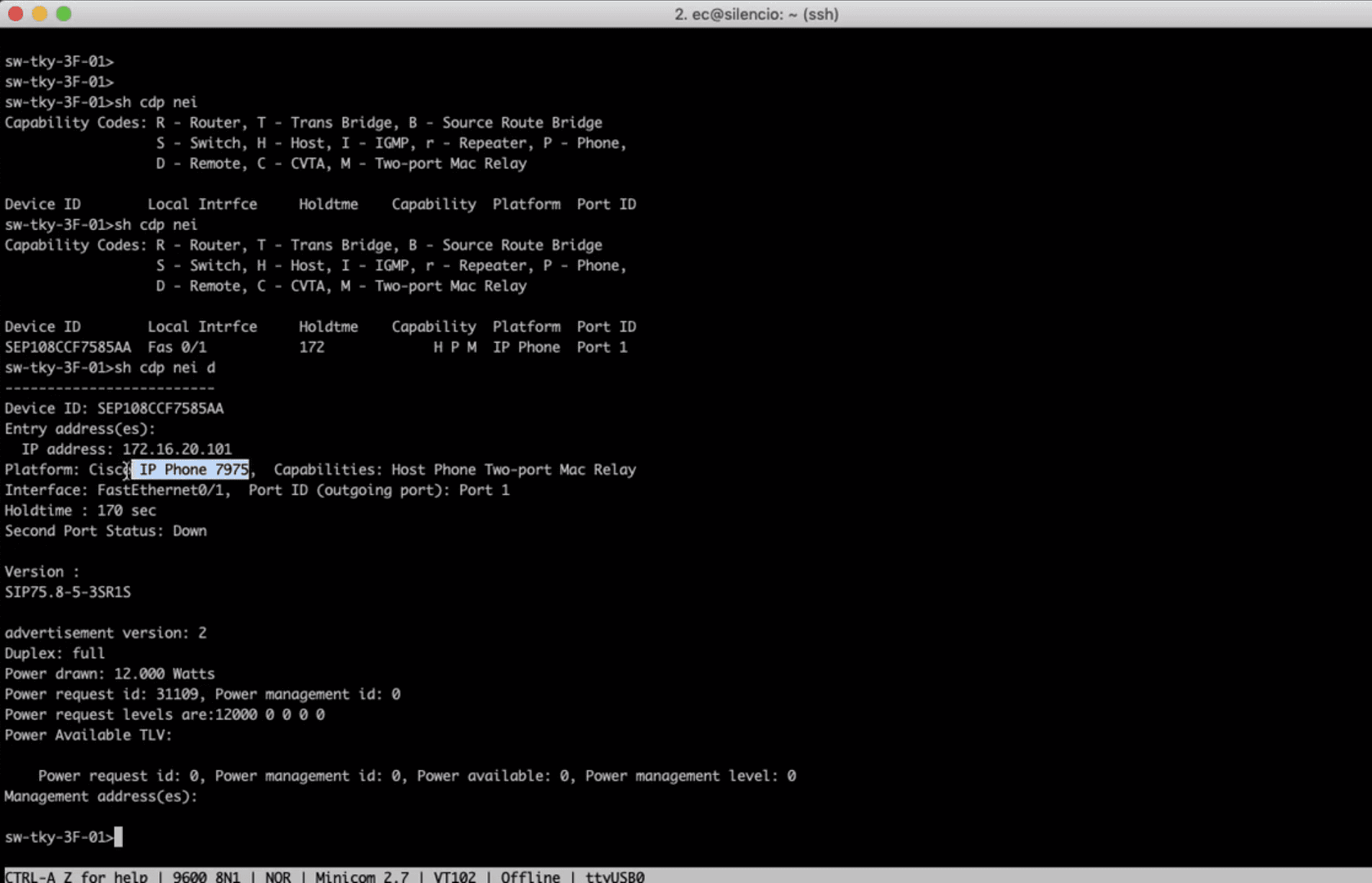
- Capture VoIP RTP traffic (tapping phone calls)
- Capture SIP hash
- Spoof MAC/IP for exfiltration
- Support any TCP port for exfiltration
Install && Usage
Copyright (c) 2018 ekio