
Proofpoint researchers have uncovered a campaign targeting transport and logistics companies across North America. These attackers are leveraging compromised email accounts from legitimate firms in the industry, using advanced social engineering tactics to deliver malware to unsuspecting recipients.
The cybercriminals hijack genuine email accounts belonging to transportation and shipping companies, injecting malicious content into ongoing conversations. Responding to existing email threads increases the likelihood that recipients will trust and interact with the malicious messages. Proofpoint reports that at least 15 compromised accounts have been used in this campaign, tracked since May 2024.
The attackers have evolved their tactics over time. Initially, they delivered malware payloads like Lumma Stealer, StealC, and NetSupport. However, by August 2024, the cybercriminals began deploying DanaBot and Arechclient2, using new infrastructure and delivery methods.
Most campaigns have utilized Google Drive URLs that direct victims to download internet shortcut files (.URL). Once executed, these files use the SMB protocol to retrieve and install the malware from a remote share. Another technique also is used, known as “ClickFix,”. This method tricks users into copying and running a Base64-encoded PowerShell script, which ultimately installs malware.
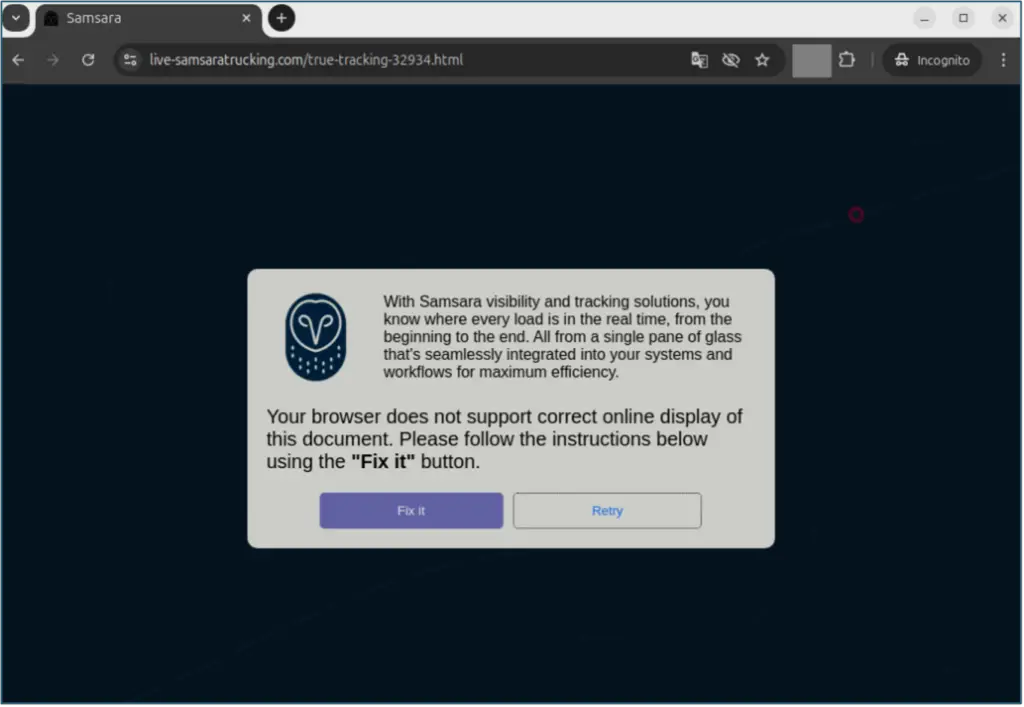
Proofpoint notes that the attackers primarily impersonate software related to transport and logistics, such as Samsara, AMB Logistic, and Astra TMS. These programs are widely used in fleet operations management, making the impersonations more believable to their targets.
Proofpoint assesses that this activity is financially motivated and aligns with broader trends in the cybercrime world. Instead of developing complex, unique malware, attackers are using commodity malware, which is widely available and easier to deploy. This shift allows cybercriminals to focus on refining their initial access and social engineering tactics
Related Posts:
- Temptation from Money: Lazarus APT extended to cryptocurrencies
- Hackers Exploit YouTube for Game Cracks, Steal Your Data
- Hacker exploits Google App script to spread malware