
A critical security vulnerability has been disclosed in Meshtastic, the open-source LoRa mesh networking platform known for enabling long-range, low-power communication without cellular or internet connectivity. Tracked as CVE-2025-24797, the flaw carries a CVSS score of 9.4 and allows for unauthenticated remote code execution (RCE) on vulnerable devices running firmware versions prior to 2.6.2.
Meshtastic is used for text messaging, GPS/location sharing, and telemetry over decentralized mesh networks. It supports platforms like ESP32, nRF52, RP2040, and Linux, and is widely adopted in outdoor adventures, emergency scenarios, and off-grid communications.
At its core, the issue lies in incorrect handling of malformed mesh packets that contain invalid Protocol Buffers (protobuf) data. The flaw occurs during decoding, where the system fails to validate memory sizes before performing memcpy operations, leading to a buffer overflow condition.
According to the official Meshtastic security advisory, “A fault in the handling of mesh packets containing invalid protobuf data can result in an attacker-controlled buffer overflow, allowing an attacker to hijack execution flow.”
This vulnerability can be exploited without authentication or user interaction, as long as the vulnerable device is actively rebroadcasting packets on the default mesh channel—a default behavior in typical Meshtastic deployments.
The attacker crafts a malicious packet that leverages the overflow to overwrite memory beyond the RadioBuffer struct, including parts of memory tied to thread management:
Security researcher Alain Siegrist (@Alainx277) is credited with the discovery and responsible disclosure of the issue, and has also released a proof-of-concept exploit showcasing the flaw in action.
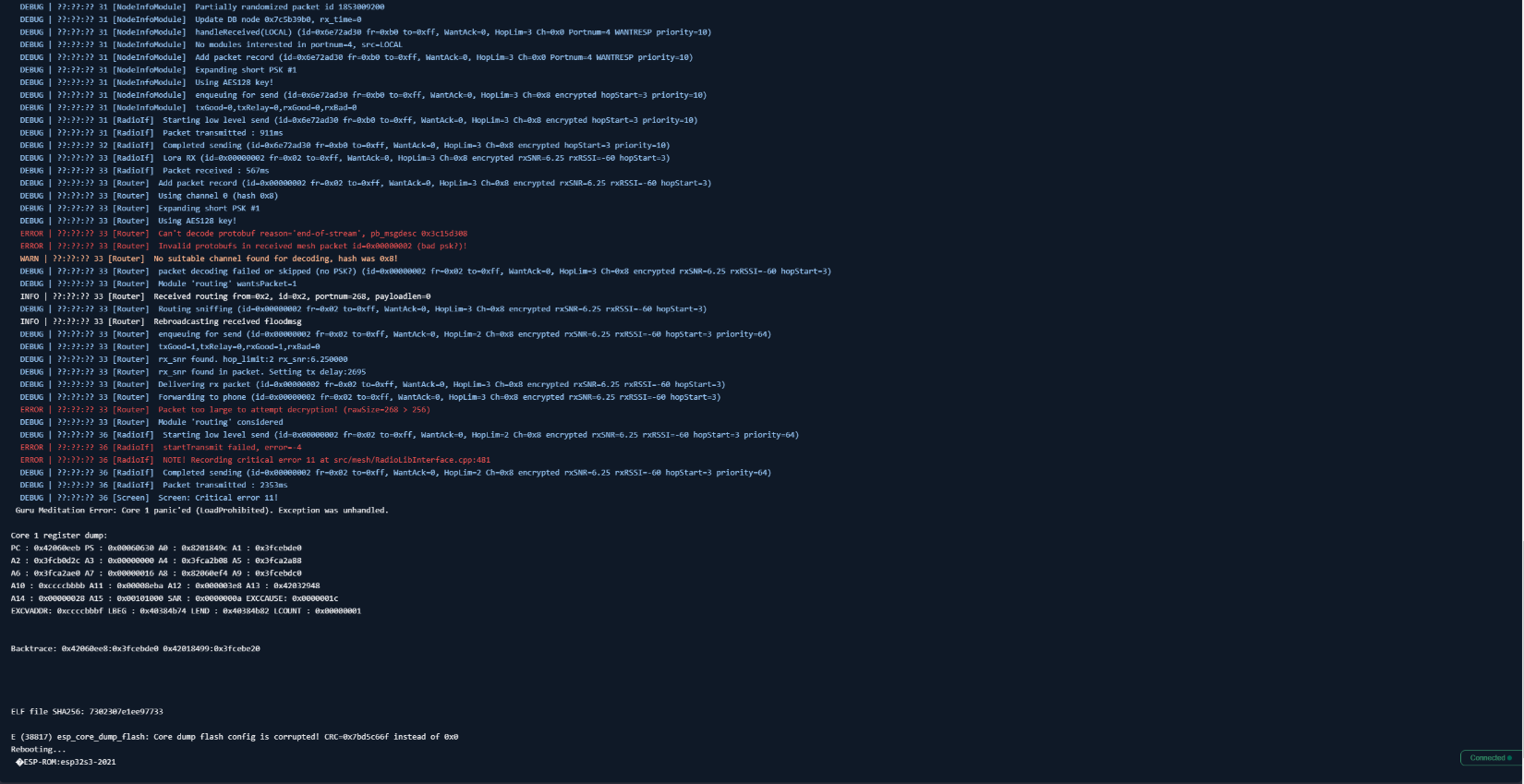
“After these fields, the virtual table pointer for concurrency::NotifiedWorkerThread follows. By overwriting this pointer, an attacker can arbitrarily redirect execution the next time the thread is run, potentially allowing remote code execution,” the researcher wrote.
The advisory notes that on embedded systems lacking ASLR or memory execution protection, developing a working exploit is “fairly simple” due to the ability to embed shellcode directly in the packet payload.
The very nature of Meshtastic’s mesh networking amplifies the risk. As the advisory points out, “This vulnerability can be abused even on nodes which are multiple hops away. Because the packet is rebroadcasted, an attacker can nest multiple stages of the malformed encrypted data, where the initial stages overwrite the size field with valid values. The data will be unpacked on every hop until the final overwrite is triggered.” This multi-hop exploitation potential significantly broadens the attack surface.
The vulnerability affects all firmware versions below 2.6 and has been patched in version 2.6.2. All users are strongly advised to upgrade immediately to prevent potential compromise.
Related Posts:
- GitHub Enterprise Server Vulnerabilities Expose Risk of Code Execution and Data Leaks
- Urgent Security Alert: CISA Warns of Actively Exploited Apple and Microsoft Vulnerabilities
- Critical Bubble.io Vulnerability Exposes Apps to Data Theft via Elasticsearch, No Patch
