CrossC2Kit: infiltration expansion around the Unix platform
CrossC2 Kit
CrossC2Kit is an infiltration expansion around the Unix platform derived from CrossC2. Use Aggressor Script Open Source Script engine. It can be used to create automation to simulate the operation process of the Red Team and expand the CobaltStrike client.

However, it has also performed some API expansion on CrossC2 to control the UNIX platform Beacon. The main functions are to perform the dynamic library (.so / .dylib) and executable files (ELF / MachO) and executable files from memory parsing. Script (bash / python / php …). At the same time, some data set interfaces of CobaltStrike are reserved, such as portscan, screenshots, keylogger, credentials, etc., which can quickly develop Portscan and other kits. And if you are familiar with the CS native protocol, you can specify some more complicated data results for more flexible metadata collection.
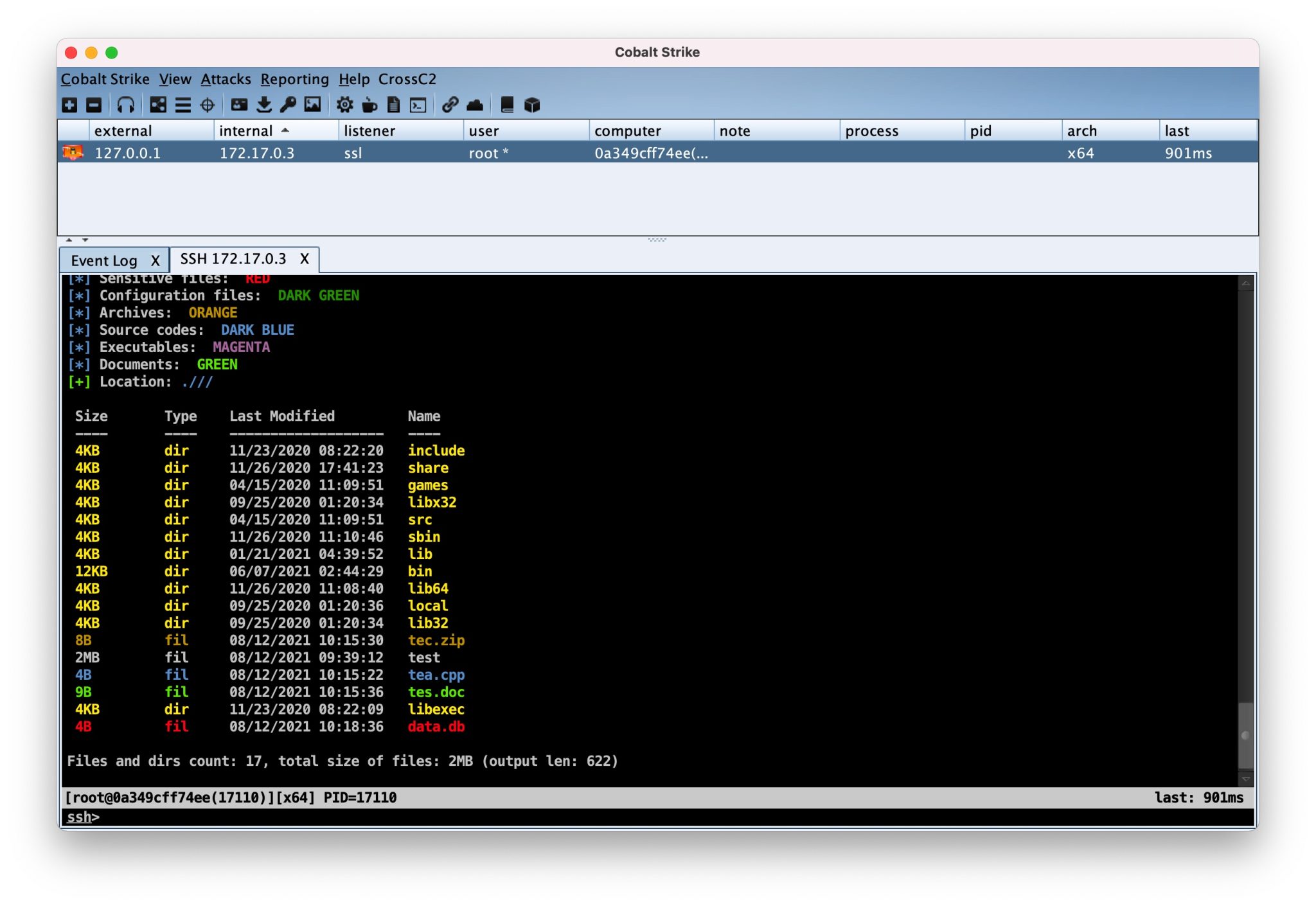
- cc2FilesColor.cna – Color Coded Files Listing for CrossC2. Based on the original FilesColor.cn by @mgeeky this script colorizes file listing outputs based on file type and extension.Use the ls command to display:

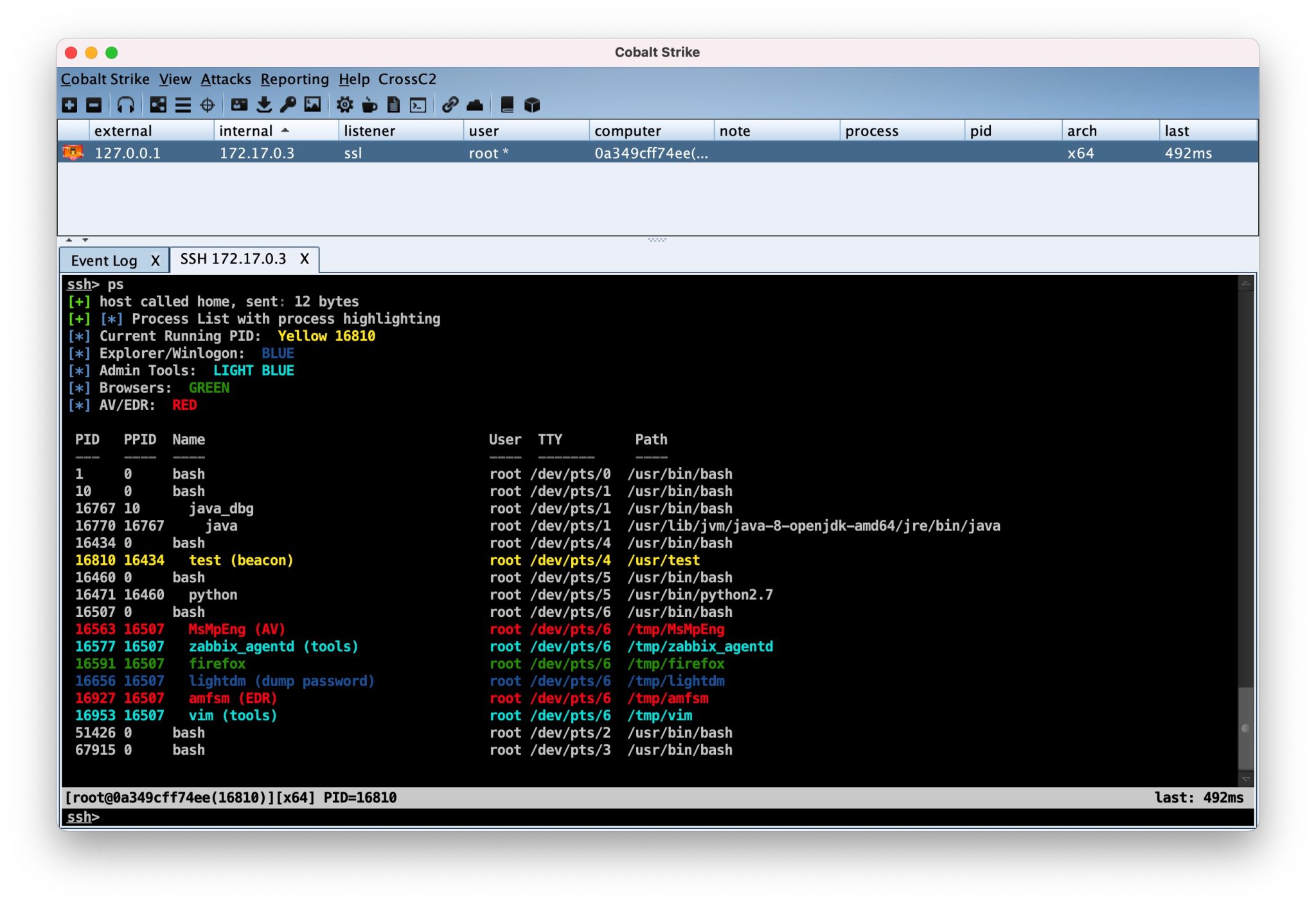
- cc2ProcessColor.cna – Color Coded Process Listing for CrossC2. Based on the original ProcessColor.cna by @r3dQu1nn.Takes the ps output in CS and color codes all AV processes, explorer process, browsers processes, and current process running. If the process can dump the password, it will display (dump password) to prompt.Use the ps command to display:

Basic function
- Interpreter related plug-ins – Support calling script interpreters such as bash / python / ruby / perl / php in the host, Execute the incoming script. The plug-in will redirect the interpreter I/O, input and output directly from the memory, and no files will be executed on the ground. It also integrates python-import which is similar to the powershell-import operation
- python c:\getsysteminfo.py arg1 arg2 arg3
- python import base64;print base64.b64encode(‘whoami’); print ‘a’*40
- python-import c:\test.py
- Password dump module – cc2_mimipenguin uses the open-source project MimiPenguin2.0
- Authentication backdoor modules – cc2_auth, cc2_ssh sudo / su / passed, and other authentication backdoors, ssh is connected and the credentials to connect to other hosts will be recorded.
- Information collection modules – cc2_safari_dump, cc2_chrome_dump, cc2_iMessage_dump, cc2_keychain_dump access records of common browsers, as well as iMessage chat content and authentication credentials saved in the keychain will be obtained
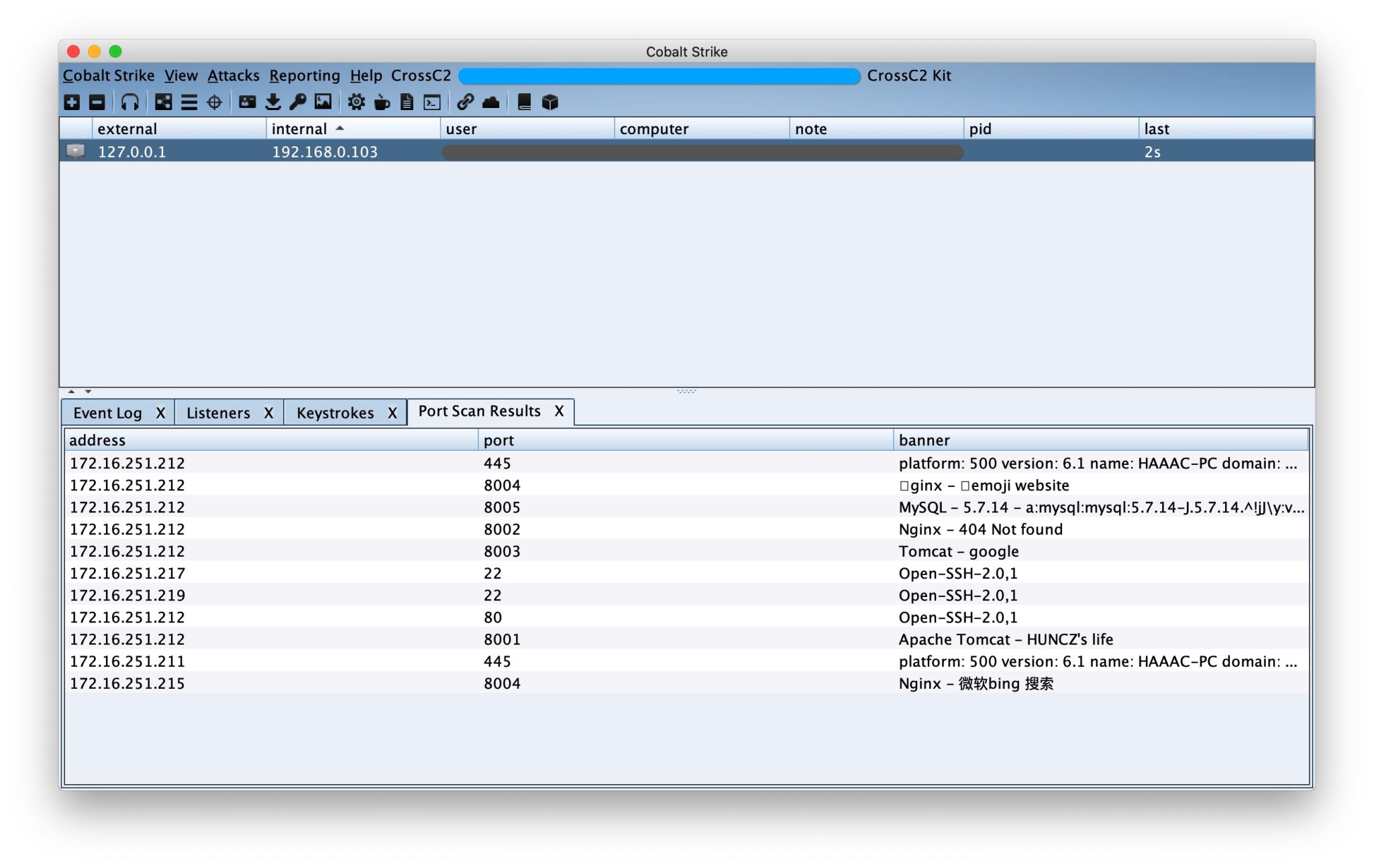
- Traffic proxy module – cc2_frp supports fast TCP/KCP (UDP) reverse socks5 encrypted traffic proxy (server can deploy Github native FRP)
- Keylogger module – cc2_keylogger records the keyboard input of MacOS users
- Privilege promotion module – cc2_prompt_spoof induces deception to obtain a MacOS user account password
- Task management module – cc2_job manages the modules running in memory.
Download
Copyright (C) 2022 gloxec