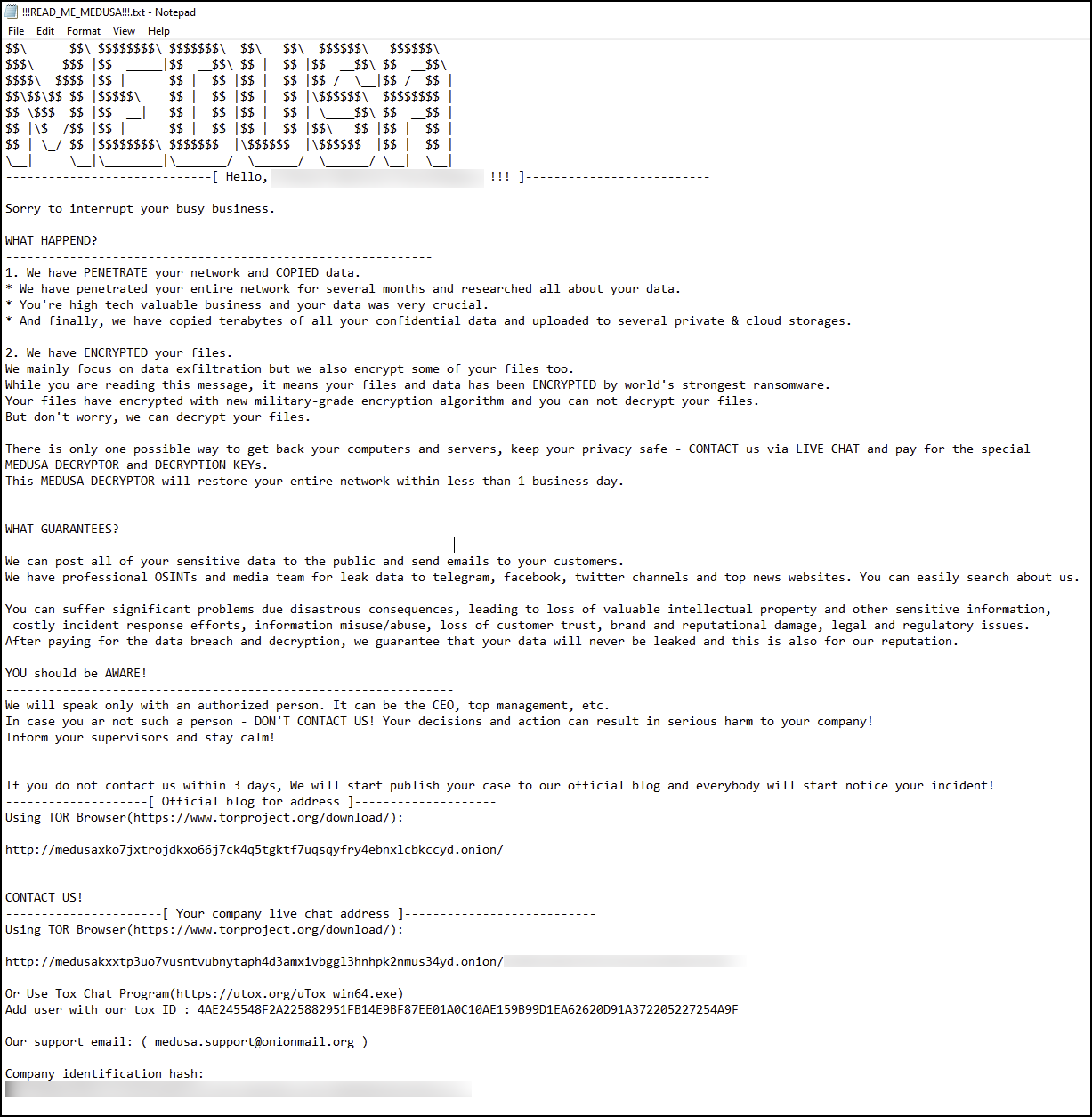
Medusa ransomware ransom note | Image: Unit 42
In a concerning new development, cybersecurity researchers at Darktrace have unveiled a report detailing the exploitation of Fortinet’s FortiClient Endpoint Management Server (EMS) by cybercriminals. The report highlights critical vulnerabilities, particularly CVE-2023-48788, and outlines a sophisticated attack chain and post-exploitation tactics observed across various environments.
FortiClient EMS, widely used for centralized management of endpoint security, was compromised through an SQL injection vulnerability (CVE-2023-48788) that scored a critical 9.8 on the CVSS scale. The vulnerability, disclosed in March 2024, allowed attackers to gain unauthorized access without authentication by exploiting improper SQL command neutralization. This flaw opened a path for Remote Code Execution (RCE), posing a serious threat to organizations that had yet to patch their systems.
Darktrace observed multiple instances of EMS devices communicating with suspicious external IPs, suggesting early signs of exploitation. These connections were likely used to validate the vulnerability and establish an initial foothold.
Once access was achieved, attackers deployed Remote Monitoring and Management (RMM) tools, including Atera and ScreenConnect, to maintain persistent access to the compromised systems. The use of legitimate RMM tools helped the attackers blend into normal network traffic, avoiding detection by conventional security tools. Notably, some devices initiated HTTP POST requests to IPs linked to the notorious Sliver C2 framework, commonly used by advanced persistent threat (APT) groups like APT28 and APT29.
The malicious actors also downloaded files, including “SETUP.MSI” and “run.zip,” which likely contained additional malicious payloads. These downloads further solidified their control over the compromised devices.
Following the initial breach, the attackers engaged in internal reconnaissance, leveraging tools like Nmap to scan the network and gather critical intelligence. In one environment, an unusual spike in internal connections was detected, indicating widespread network scanning activity.
Sometimes, the attackers used brute-force attacks to escalate privileges, successfully authenticating with admin credentials. Once administrative access was obtained, lateral movement followed swiftly, using tools like PsExec and exploiting the DCE-RPC protocol to traverse the network undetected.
While Darktrace did not observe the end goal in most cases, one instance stood out where a large volume of data was uploaded to an external cloud storage service. This suggests that data exfiltration may have been the attackers’ primary objective. In another instance, a Medusa ransomware attack was traced back to a FortiClient EMS compromise, where the system was breached weeks before the ransomware deployment.
The exploitation of FortiClient EMS underscores the critical need for organizations to patch vulnerabilities in internet-facing systems promptly. The rapid exploitation of CVE-2023-48788, even after the public disclosure of a fix, reveals how quickly threat actors can capitalize on unpatched systems. Darktrace’s findings also highlight the growing sophistication of post-exploitation tactics, as attackers increasingly rely on legitimate tools like RMM software to remain undetected.
Related Posts:
- Critical Fortinet Vulnerability Exploited: Hackers Deploy Remote Control Tools and Backdoors
- PoC Exploit Released for Critical Fortinet FortiClient EMS CVE-2023-48788 Flaw
- “Connect:fun” Campaign Targets Media Organizations, Exploits Critical Fortinet Vulnerability
- Medusa Exploits Fortinet Flaw (CVE-2023-48788) for Stealthy Ransomware Attacks
- Fortinet Patches Multiple Critical Vulnerabilities Affecting FortiClient, FortiSandbox, FortiOS, and FortiProxy