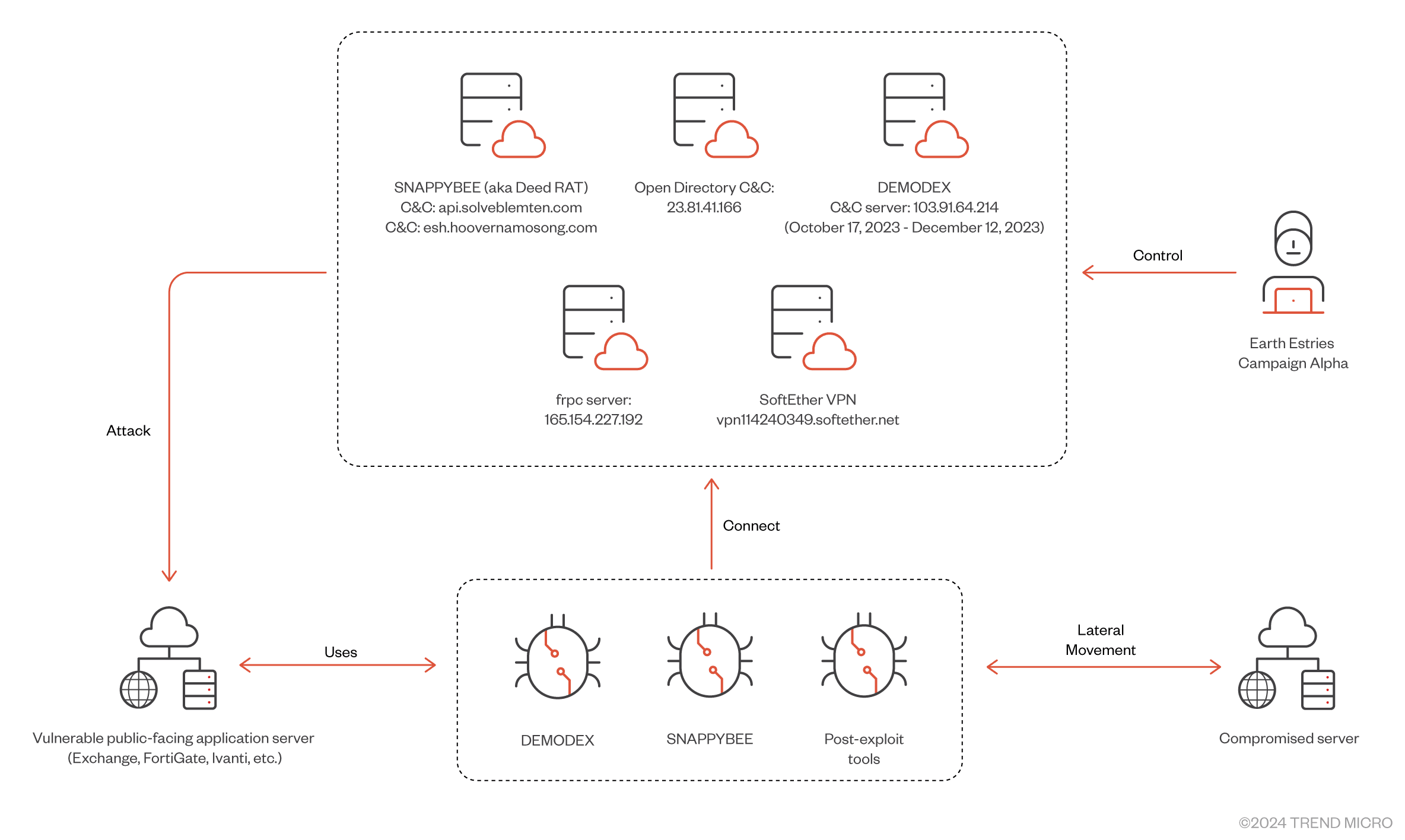
Campaign Alpha overview | Image: Trend Micro
In a detailed report from Trend Micro, the Chinese advanced persistent threat (APT) group Earth Estries, also known by aliases like Salt Typhoon and GhostEmperor, has emerged as a significant cyber espionage actor since 2023. Targeting critical sectors such as telecommunications, government entities, and NGOs, the group has left its mark across the US, Asia-Pacific, Middle East, and Africa. Their operations have also extended to industries including technology, consulting, and transportation, compromising over 20 organizations worldwide.
Earth Estries employs a mix of sophisticated tools and strategies, including three proprietary backdoors: GHOSTSPIDER, SNAPPYBEE, and MASOL RAT. These tools are often deployed after exploiting public-facing server vulnerabilities, such as those in Ivanti Connect Secure VPN (CVE-2023-46805, CVE-2024-21887), Fortinet FortiClient EMS (CVE-2023-48788), and Microsoft Exchange servers through the notorious ProxyLogon exploit chain. These backdoors enable the group to establish long-term footholds in targeted networks.
One of their most notable tools, GHOSTSPIDER, is a modular backdoor designed for stealth and adaptability. It utilizes a multi-layered architecture, loading different modules based on specific tasks. The report states, “This backdoor communicates with its C&C server using a custom protocol protected by Transport Layer Security (TLS), ensuring secure communication.”
The group’s primary focus has been on Southeast Asia, where they have targeted governments and telecommunications companies. A particularly concerning discovery was their use of the DEMODEX rootkit, which was implanted on vendor machines associated with major telecommunications providers. This strategy allowed them to infiltrate larger networks and gather sensitive intelligence more effectively.
The overlap between Earth Estries’ tactics and those of other Chinese APT groups, such as FamousSparrow and GhostEmperor, suggests the possible use of shared tools sourced from malware-as-a-service (MaaS) providers. For example, SNAPPYBEE, a modular backdoor widely associated with Chinese APTs, has been a recurring tool in Earth Estries’ arsenal.
The report emphasizes the difficulty in detecting Earth Estries’ activities, as they rely heavily on living-off-the-land binaries (LOLBINs) like WMIC.exe and PsExec for lateral movement within networks. Their use of encrypted communication and modular malware complicates traditional detection methods.
As Trend Micro aptly concludes: “Earth Estries conducts stealthy attacks that start from edge devices and extend to cloud environments, making detection challenging. They employ various methods to establish operational networks that effectively conceal their cyber espionage activities, demonstrating a high level of sophistication in their approach to infiltrating and monitoring sensitive targets.” For businesses and governments alike, understanding the intricacies of such groups is key to building resilient defenses against cyber-espionage.
For the full technical analysis and indicators of compromise, visit Trend Micro’s official blog.
Related Posts:
- Earth Estries’ Evolving Toolkit: A Deep Dive into Their Advanced Techniques
- Earth Lusca: China-Linked Espionage Group Targets Taiwan, Exploits Geopolitical Tensions
- Earth Baku APT Group Expands Global Reach with Advanced Techniques
- Earth Preta’s Cyber Arsenal Expands: New Malware and Strategies Target APAC Governments
- Earth Simnavaz Exploits Windows Kernel Flaw CVE-2024-30088 in Attacks on Critical Infrastructure