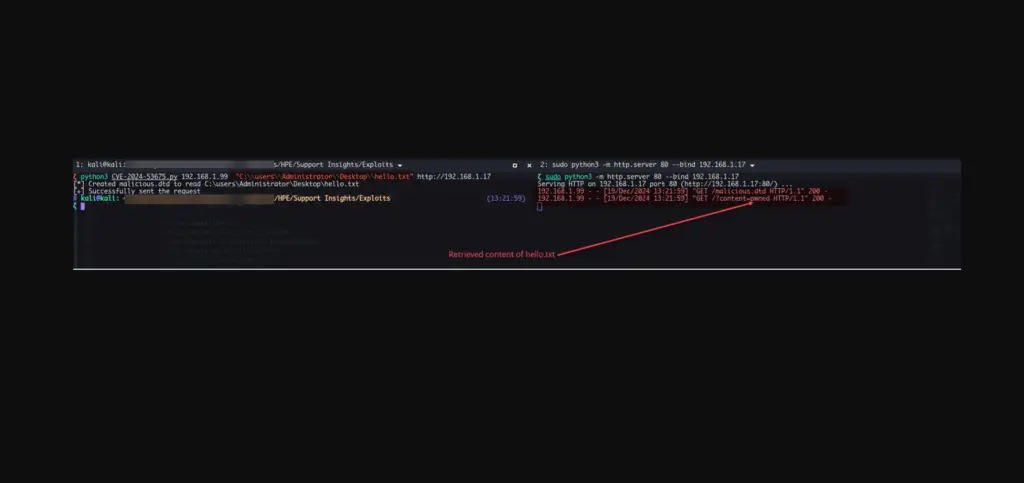
Security researcher Robin recently disclosed details and a PoC exploit code of an XML external entity injection (XXE) vulnerability, tracked as CVE-2024-53675, affecting HPE Insight Remote Support (Insight RS). This vulnerability, assigned a CVSS score of 7.3, could allow remote attackers to expose sensitive information without authentication.
HPE Insight Remote Support (Insight RS) is a widely used enterprise monitoring and support solution that enables proactive and reactive remote support for servers, storage, and networking hardware. The software helps businesses improve system availability by diagnosing hardware failures and automatically sending service notifications to HPE.
The vulnerability exists in the validateAgainstXSD method, which fails to properly restrict XML External Entity (XXE) references. According to the Zero Day Initiative (ZDI) Advisory, the flaw allows attackers to embed external entity references in crafted XML documents, leading to unauthorized access and potential data exfiltration.
The vulnerability resides in the validateAgainstXSD method, which fails to properly restrict XML External Entity (XXE) references. By crafting a malicious XML document, an attacker can trick the XML parser into accessing a specified URI and embedding its contents back into the document. This enables the attacker to potentially disclose files accessible to the SYSTEM account.
Robin’s proof-of-concept (PoC) exploit demonstrates CVE-2024-53675 by hosting a malicious DTD file and sending a crafted payload that retrieves and sends the content of a specified file to the attacker’s listener. However, the exploit is limited in its ability to exfiltrate data as the underlying library only sends the first line of the file due to issues parsing newline characters.
Despite this limitation, attackers could leverage this flaw in combination with other techniques, such as multiple sequential requests, to extract full files or gather reconnaissance information for further attacks.
HPE has acted swiftly to address this flaw by releasing Insight Remote Support v7.14.0.629. This update includes patches for all identified vulnerabilities. HPE strongly urges users to update their Insight Remote Support installations immediately to mitigate the risk of exploitation.
Related Posts:
- One-Day Exploits, Stealthy Tactics: Why Raspberry Robin Worm is a Cybersecurity Nightmare
- Raspberry Robin’s Stealth Tactics: USB Infections, Exploits, and Advanced Obfuscation Unveiled
- HPE Aruba Networking Addresses Severe Vulnerabilities in Access Points
