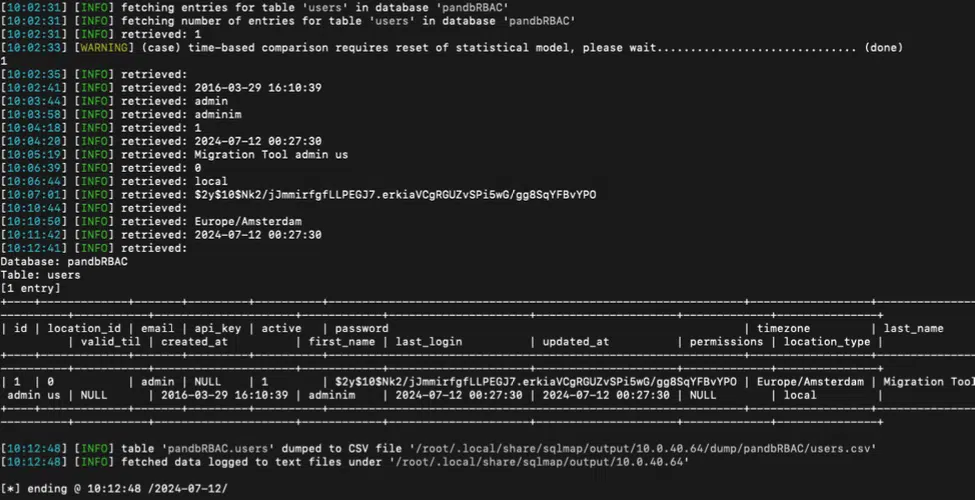
Dumping entire table of choice via BLIND time-based SQL payloads | Image: Horizon3.ai
A critical vulnerability, CVE-2024-9465, has been discovered in Palo Alto Networks’ Expedition tool by security researcher Zach Hanley of Horizon3.ai. This SQL injection flaw, with a CVSS score of 9.2, allows unauthenticated attackers to access sensitive information stored in Expedition’s database. This includes password hashes, usernames, device configurations, and API keys, potentially leading to system compromise.
Hanley’s analysis of the vulnerability reveals that attackers can exploit the flaw by sending malicious SQL queries through unprotected endpoints. An unauthenticated curl request can create a table within the Expedition system’s database, opening the door for further exploitation. By crafting specific requests, an attacker can create tables, inject queries, and dump sensitive data, all without requiring valid credentials.
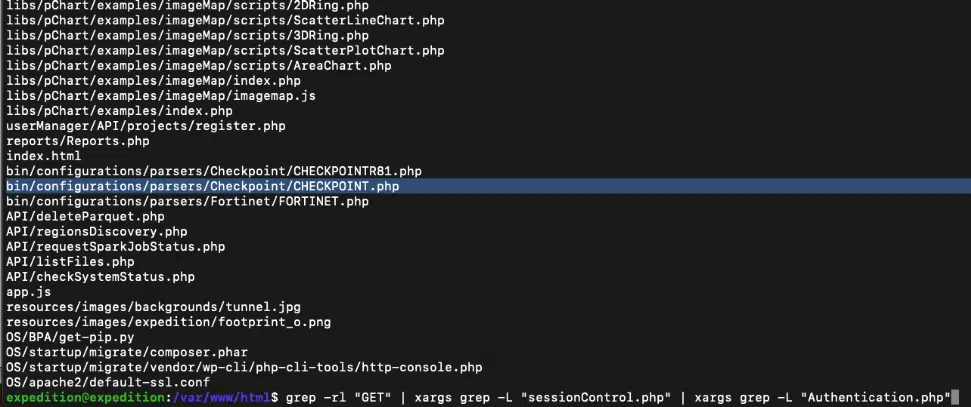
The flaw was found in a PHP file within the Expedition web root, where certain HTTP request parameters are parsed and used in SQL queries without proper sanitization. “We happen upon the file /var/www/html/bin/configurations/parsers/Checkpoint/CHECKPOINT.php. This file is reachable unauthenticated, takes HTTP request parameters as inputs, and then constructs SQL queries with that input,” Hanley noted. Using tools such as SQLMAP, Hanley successfully demonstrated how attackers could dump sensitive data from Expedition’s database, including the full contents of the “users” table.
The researcher published a proof of concept to exploit CVE-2024-9465 on vulnerable devices.
The impact of this vulnerability is significant. Attackers can not only leak sensitive data but also create and read arbitrary files on the Expedition system, escalating their control over compromised networks. In response to this vulnerability, Palo Alto Networks has released fixes in Expedition version 1.2.96 and later versions.
To mitigate the risk, Palo Alto Networks advises restricting network access to the Expedition tool, ensuring it is only accessible to authorized users, hosts, or networks. As a temporary workaround, organizations are encouraged to shut down the Expedition tool if it is not actively in use.
Related Posts:
- Palo Alto Networks Issues Fix for Critical Vulnerabilities, Including CVE-2024-9463 (CVSS 9.9)
- CVE-2024-9466 Flaw in Palo Alto Networks’ Expedition Exposes Sensitive Credentials to Attackers, PoC Published
- CVE-2024-5910: Critical Vulnerability Threatens Palo Alto Networks’ Expedition
- PoC Exploit Releases for Exploited Vulnerability CVE-2024-8190 in Ivanti Cloud Services Appliance
- Critical SolarWinds Flaw Exposes 827 Instances: PoC Exploit Unveiled for CVE-2024-28987