
Trend Micro has uncovered details about a sophisticated cyberespionage campaign from Earth Estries, also known as Salt Typhoon. Active since 2020, Earth Estries primarily targets governments and technology firms through intricate multi-step attack chains. The group’s evolving toolkit and techniques highlight their dedication to remaining undetected and maintaining prolonged access to compromised environments.
Trend Micro’s analysis of Earth Estries’ activities reveals two distinct infection chains, each with its own arsenal of tools and tactics. “The first chain employs PsExec and WMI command-line (WMIC) for lateral movement, using tools such as Cobalt Strike, Trillclient, Hemigate, and Crowdoor,” the report states. These tools are introduced via CAB file packages, a method that allows for seamless distribution and execution within target networks. This chain is notable for its use of Trillclient to extract user credentials from browser caches, extending Earth Estries’ reach across systems.
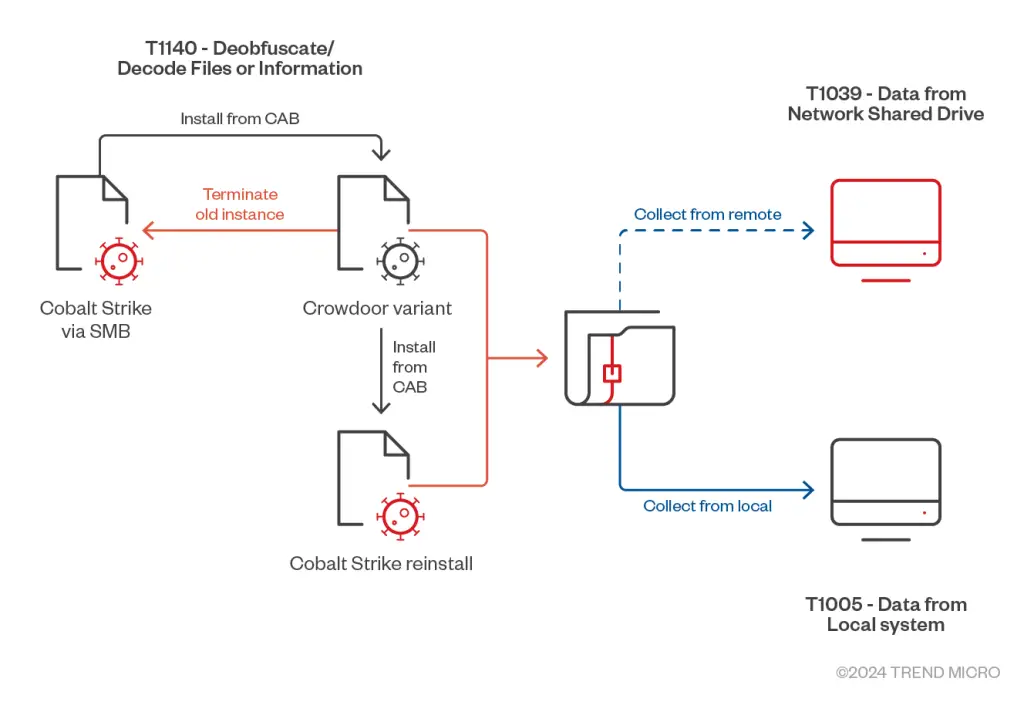
The second chain focuses on exploiting vulnerabilities in Microsoft Exchange servers, leveraging the ChinaChopper web shell to implant Cobalt Strike and other backdoors like Zingdoor and SnappyBee. As Trend Micro explains, “Delivery of these additional backdoors and tools is done either via a C&C server or by using cURL to download them from attacker-controlled servers”. This method enables Earth Estries to refresh and replace their malware components regularly, making them harder to detect.
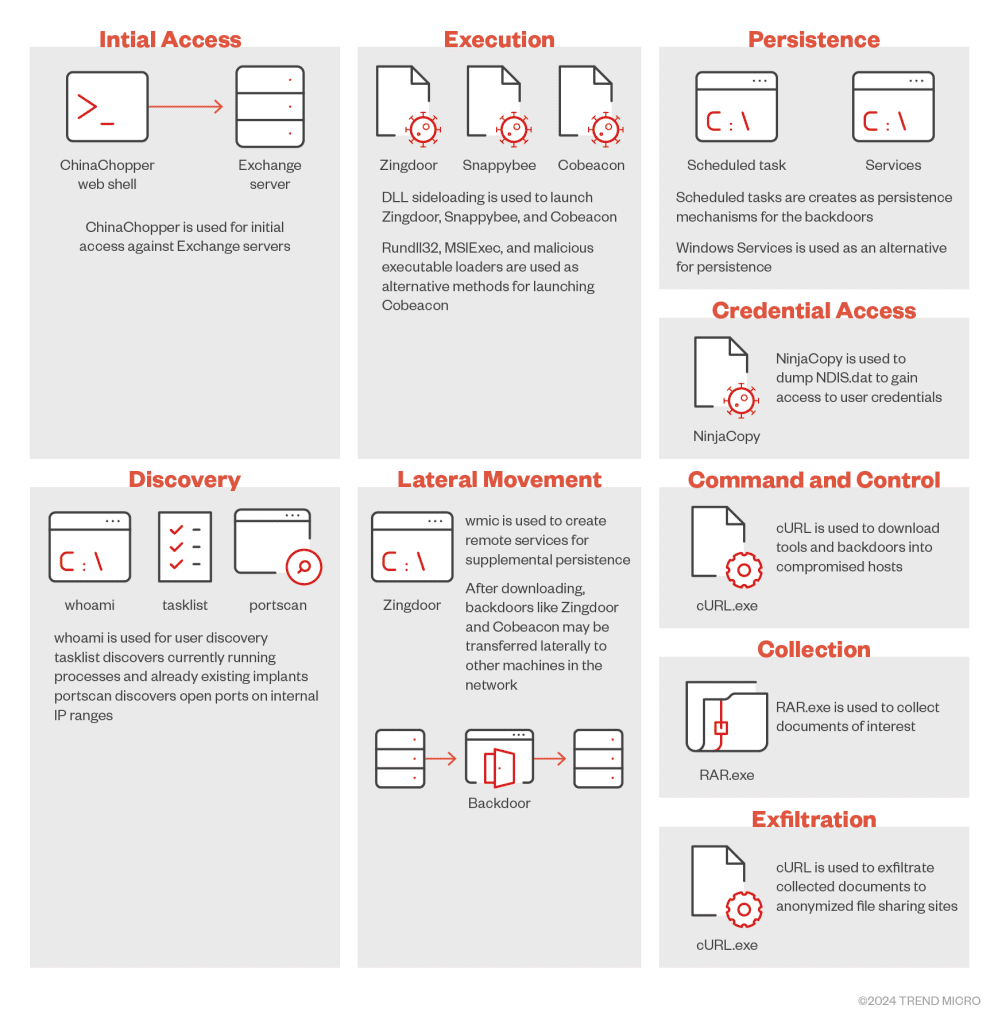
Earth Estries has introduced new backdoors to its toolkit, including Crowdoor, an update from previous backdoor Hemigate. Crowdoor operates in sync with Cobalt Strike, leveraging an advanced command structure to ensure effective persistence and concealment. “Crowdoor will perform different actions based on the corresponding argument,” the report notes, with unique commands for actions such as persistence, file manipulation, and remote shell operations.
The group’s persistence strategies are equally complex. They utilize scheduled tasks, DLL sideloading, and remote service creation to maintain access, often employing tools like Zingdoor through DLL sideloading on Windows Defender’s MsSecEs.exe. Moreover, Earth Estries extensively relies on the cURL utility to pull sensitive data and upload it to anonymous file-sharing sites, ensuring a discreet exfiltration process. According to Trend Micro, “Exfiltration is done using cURL, which sends the stolen documents to anonymized file sharing services.”
Earth Estries’ campaigns exemplify the strategic depth of modern cyberespionage. Through continuous adaptation and custom tool development, the group has refined its approach to bypass security defenses and exploit overlooked vulnerabilities. Trend Micro’s report warns that Earth Estries “has displayed a keen understanding of their target environments,” a quality that enables them to navigate complex networks with precision and resilience.
With its multi-pronged attack strategies and layered persistence mechanisms, Earth Estries represents a formidable threat that underscores the necessity for robust, proactive defense measures across government and tech infrastructures.
Related Posts:
- Earth Preta’s Cyber Arsenal Expands: New Malware and Strategies Target APAC Governments
- Earth Lusca: China-Linked Espionage Group Targets Taiwan, Exploits Geopolitical Tensions
- Earth Baku APT Group Expands Global Reach with Advanced Techniques
- Earth Simnavaz Exploits Windows Kernel Flaw CVE-2024-30088 in Attacks on Critical Infrastructure
- New KTLVdoor Backdoor Discovered in Multiplatform Intrusion Campaign Linked to Earth Lusca