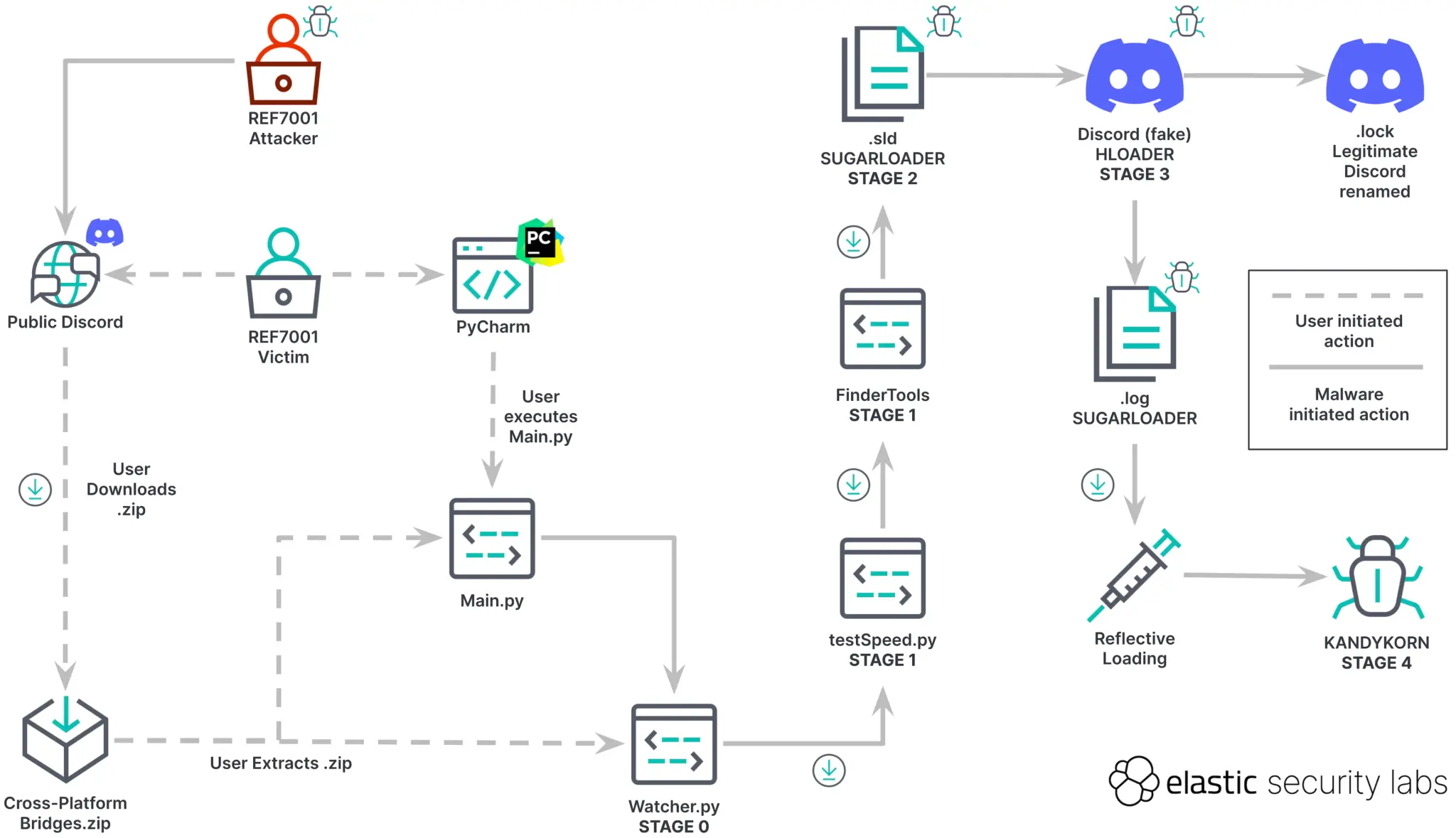
Execution Flow
In recent weeks, a surge in the activity of North Korean hackers has been sharply observed. Specialists at Elastic Security Labs have identified a new cyber threat associated with a complex piece of malware — KANDYKORN, targeting macOS users in the cryptocurrency sector, propagated via the Discord messaging platform. Posing as blockchain developers, the perpetrators offer victims tools purportedly for profiting from cryptocurrency arbitrage transactions.
Analysts link this latest campaign, initiated in April 2023, to the notorious hacker collective Lazarus, noting attack methods and network infrastructure that bear their distinct signature.

Victims are enticed to download a ZIP archive laden with malicious code, under the belief they are acquiring a cryptocurrency trading application; in reality, it serves as a conduit for hackers to gain initial system access.
“The DPRK, via units like the LAZARUS GROUP, continues to target crypto-industry businesses with the goal of stealing cryptocurrency in order to circumvent international sanctions that hinder the growth of their economy and ambitions,” explain researchers Ricardo Ungureanu, Seth Goodwin, and Andrew Pease in their report.
This year, Lazarus group hackers have already targeted macOS users with infected PDF files. Upon opening the document, the victim unwittingly triggers a concealed threat — the backdoor RustBucket, crafted in AppleScript, which stealthily downloads additional malicious components from an external server.
KANDYKORN operates directly within the RAM of macOS-based devices. This espionage software is capable not only of harvesting information from infected computers but also of initiating new malicious operations, disrupting individual applications, and executing various commands as required by the attackers.
The primary complexity of the attack lies in the use of a chain of droppers — intermediary links that facilitate the installation of the main malware. The process begins with the Python script watcher.py contained in the initial ZIP archive, acting as the first dropper. Subsequently, a second script, testSpeed.py, is downloaded from Google Drive cloud storage, paving the way for the downloading of FinderTools, another component also hosted on Google Drive.
FinderTools activates SUGARLOADER — a covert auxiliary module disguised as system files in the directories /Users/shared/.sld and .log. This component completes the system’s preparation for infection and creates favorable conditions for the implantation of the primary code, evading standard antivirus solutions.
Only then is the connection established with a remote server to download and execute KANDYKORN within the computer’s memory.
To conceal their activity, the malicious software employs HLOADER — a specially designed file written in the Swift programming language. At first glance, it is indistinguishable from a typical Discord application. Its primary function is to commandeer the execution flow, meaning HLOADER embeds itself within the startup process of ordinary, legitimate programs, remaining imperceptible to the user.
It is assumed that the principal aim of the politically motivated hackers from North Korea, including the Lazarus group, is to access cryptocurrency assets and expropriate them to circumvent economic sanctions.
