enumerid
Enumerid is an impacket based Relative Identifier (RID) enumeration utility. It was initially created to solve a common problem that attackers face after getting an initial compromise- getting oriented within the network. Historically this means looking through ARP tables, VPN routes, Wireshark, etc.
With a valid set of credentials, you can now enumerate all valid network ranges.. even if you don’t currently have access to them.
How does enumerid work?
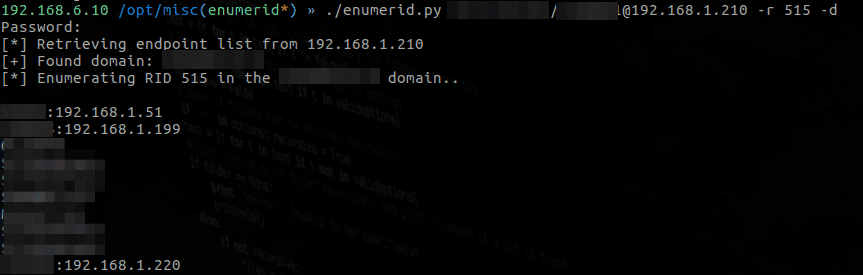
Enumerid works by querying the Domain Controller (DC) and asking for a list of RIDs for every asset in the “Domain Computers” groups. It will then ask the DC to resolve those RIDs to the corresponding clear text hostnames. With this information, you simply perform a DNS lookup on each hostname.
DNS doesn’t check if you have access to the host in question. It simply resolves the IP address for you- therefore you are able to get a list of all currently leased IP addresses. All information is output into a greppable format for easy parsing.
If the host currently has a leased IP, it will resolve. Otherwise, the hostname will appear without an IP.
You can find the associated blog for this tool here.
Install
pip2 install impacket git clone https://github.com/Gilks/enumerid.git
Use
Enumerate domain computers with DNS resolution:
./enumerid.py domain/username:password@<DC IP> -r 515 -d
Enumerate domain controllers without DNS resolution:
./enumerid.py domain/username:password@<DC IP> -r 516
Enumerate domain admins:
./enumerid.py domain/username:password@<DC IP> -r 512
Anonymous login vulnerability? Try this:
./enumerid.py domain/'':''@<DC IP> -r 515 -d
Copyright (c) 2018, Corey Gilks
All rights reserved.
Source: https://github.com/Gilks/