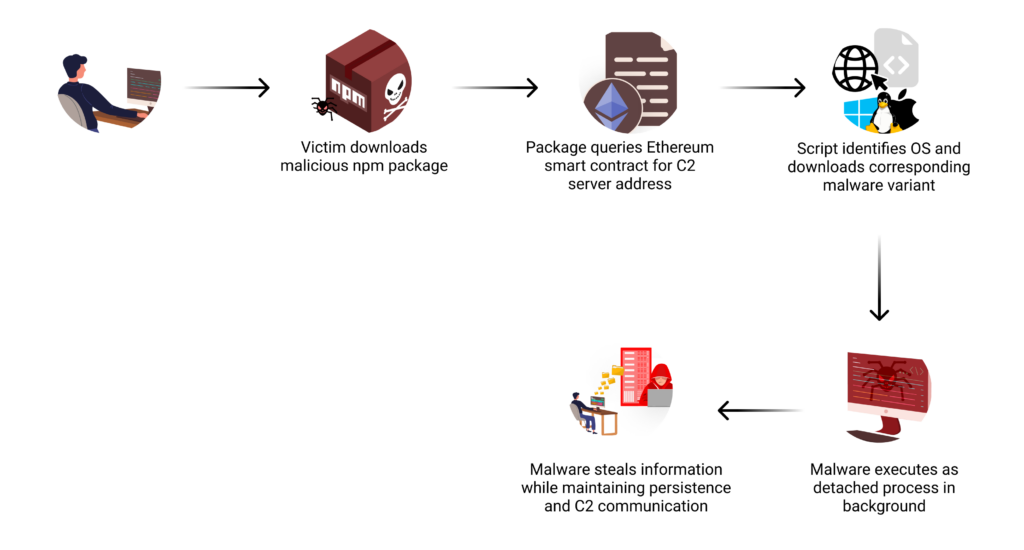
Attack Flow | Image: Checkmarx
A recent report from the Checkmarx Security Research Team reveals a sophisticated supply chain attack targeting the NPM ecosystem. The attack involves a malicious package, jest-fet-mock, which uses Ethereum smart contracts to manage its command-and-control (C2) infrastructure. This malware targets Windows, Linux, and macOS, marking a new level of complexity in supply chain attacks, especially in developer environments.
One of the most notable aspects of this campaign is its use of Ethereum smart contracts for C2 operations. Traditionally, malware relies on hardcoded servers or domain names for C2 communication, making it easier for defenders to take down the infrastructure. However, by integrating blockchain technology, the attackers gain a virtually untouchable C2 setup.
“The most distinctive aspect of this attack is how it leverages the Ethereum blockchain for its command-and-control infrastructure,” states the Checkmarx report. “When executed, the malware interacts with a smart contract… to retrieve its C2 server address.”
This approach provides the attackers with a flexible and resilient infrastructure. By simply updating the C2 address in the smart contract, they can redirect all infected systems to a new server without modifying the malware itself, allowing for continuous control and adaptability.
The attackers used jest-fet-mock, a typosquatted package, which mimics two popular testing utilities, fetch-mock-jest and jest-fetch-mock, used by JavaScript developers to mock HTTP requests. The report notes that “jest-fet-mock was the first package identified in a larger ongoing campaign targeting the NPM ecosystem“. By masquerading as familiar tools, the attackers increased the likelihood that developers would inadvertently install the malware.
The malicious package utilizes a preinstall script, executed during installation, to determine the host OS and download the appropriate payload for each platform. Notably, the attackers developed distinct malware variants for each OS, as highlighted in the report: “Cross-platform malware targeting Windows, Linux, and macOS development environments.”
Each variant includes capabilities tailored to its environment, such as system reconnaissance, credential theft, and persistence mechanisms. This cross-platform strategy underscores the attackers’ focus on compromising diverse development environments, including CI/CD pipelines.
By targeting tools within the NPM ecosystem, the attackers gained potential access to critical development infrastructures. Not only are individual developer systems at risk, but compromised CI/CD pipelines could lead to a cascade of infections across an organization’s software products and updates.
The discovery of jest-fet-mock is just the beginning. This campaign is ongoing, with additional packages linked to it. As the report concludes, “this case serves as an important reminder for development teams to implement strict security controls around package management and carefully verify the authenticity of testing utilities.”
Related Posts:
- ETH Devs Launch First Shadow Fork to test POS
- Typosquat Campaign Targets Puppeteer Users: Researcher Warns of Malware in npm Packages