Finding and exploiting Cross-site request forgery (CSRF)
Introduce
Cross-site request forgery [CSRF], also known as a one-click attack or session riding or Sea-Surf and abbreviated as CSRF or XSRF, is a type of malicious attack exploit of a website (“Web Application”); where unauthorized commands are transmitted from a user that the website trusts. The impact of a successful CSRF attack is limited to the capabilities exposed by the vulnerable application and based on the privileges of each victim. When targeting a normal user, a successful CSRF attack can compromise end-user data and their associated functions with the web app. More info, please visit here.
Damn Vulnerable Web App (DVWA) is a PHP/MySQL web application that is damn vulnerable. Its main goals are to be an aid for security professionals to test their skills and tools in a legal environment, help web developers better understand the processes of securing web applications and aid teachers/students to teach/learn web application security in a classroom environment.
Tutorial
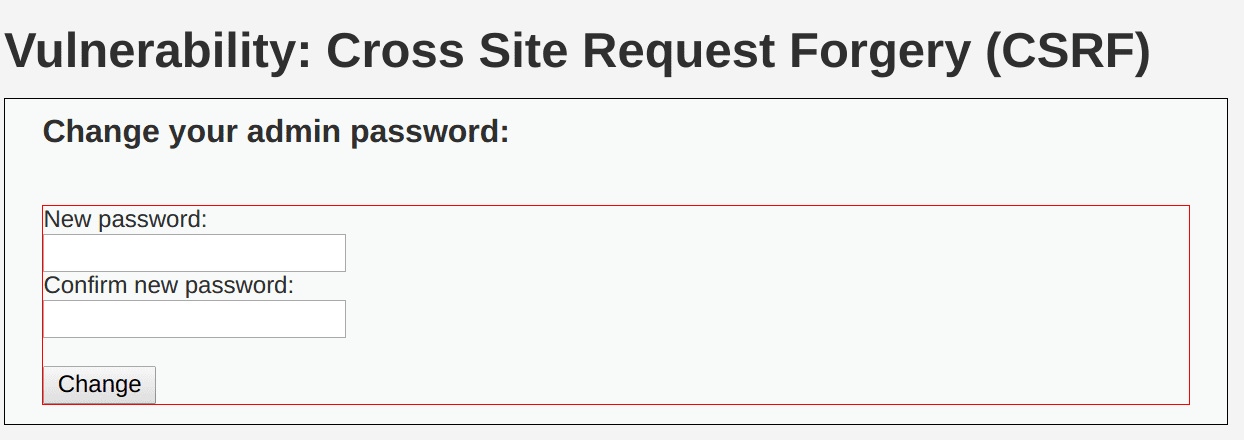
Low-Security Level
Code audit
From the code can be seen, PHP directly passed in two parameters passed password_new and password_conf, and then update the database dvwaCurrentUser () password, this is a very dangerous practice. An attacker could construct a link http://192.168.1.16/dvwa/vulnerabilities/csrf/?password_new=password&password_conf=password&Change=Change. As a result, any parameter can be constructed to implement a CSRF attack.
Medium Security Level
Code audit
The code is the same low-security level but added the following judgment:
This security level determines the source site, so the CSRF need to cooperate with other attacks, such as XSS. Determine whether the source of the link legitimate: If the HTTP header in the Host and SERVER_NAME agreed to the next step. With this judgment, CSRF can only be achieved through the XSS way. To insert link into the DVWA site to make the CSRF take effect, you can configure the following Payload in Relected-XSS or Stored-XSS for the CSRF attack to take effect:
High Security Level
Code audit
It is the same low security level but add the abnormal Anti-CSRF token, this method is widely used for Web applications to modify the password or posting function:
With Anti-CSRF token, basically, and XSS together with the use. And should be the existence of this token, XSS insert the script to be more complex, but experienced hacker still have the opportunity to CSRF success.
My approach is to be used together with the XSS. Using XSS to get the user’s token and then post to the destination address to go.





