Image: Nettitude
Organizations relying on Fortra FileCatalyst Workflow, a widely-used enterprise file transfer solution, are at severe risk due to a newly disclosed remote code execution (RCE) vulnerability (CVE-2024-25153, CVSS 9.8) and a proof-of-concept (PoC) exploit code. This flaw, responsibly reported by security researcher Tom Wedgbury of LRQA Nettitude, could give attackers full control of affected servers.
How the Attack Works
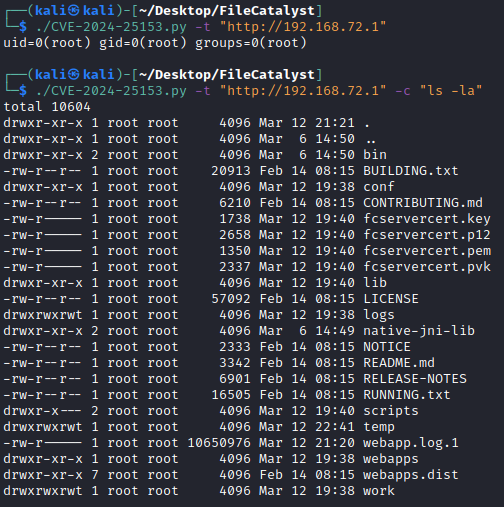
The vulnerability lies within the web portal component of FileCatalyst Workflow. Attackers can exploit a directory traversal bug to trick the server into accepting malicious file uploads outside of designated “safe” zones. If successful, this allows them to plant dangerous files like web shells directly into the server’s web root. These malicious files can then be triggered to execute arbitrary code on the system.
“A directory traversal within the ‘ftpservlet’ of the FileCatalyst Workflow Web Portal allows files to be uploaded outside of the intended ‘uploadtemp’ directory with a specially crafted POST request. In situations where a file is successfully uploaded to web portal’s DocumentRoot, specially crafted JSP files could be used to execute code, including web shells,” Fortra wrote in its security advisory.
Wide-Ranging Consequences
The implications of this vulnerability are far-reaching. Attackers could potentially:
- Exfiltrate Sensitive Data: Gain access to confidential files or steal credentials stored on the server or those in transit during file transfers.
- Establish a Foothold: Use the compromised FileCatalyst server as a pivot point to launch attacks against other internal systems.
- Cripple Operations: Disrupt essential business operations that rely on secure file transfers, potentially deploying ransomware or other destructive payloads.
Proof-of-Concept Heightens Risk

Security researcher Tom Wedgbury has released both a technical breakdown and a proof-of-concept (PoC) exploit code, demonstrating how CVE-2024-25153 can be weaponized. The release of this PoC makes it easier for less-skilled attackers to potentially exploit this vulnerability, significantly increasing the risk to unpatched systems.
Call to Action
Fortra has issued a patch for this critical flaw. Organizations using FileCatalyst Workflow 5.x, before 5.1.6 Build 114, must take the following actions immediately:
- Prioritize Patching: Apply the update as soon as possible. Any delay increases the window of opportunity for attackers.
- Enhance Monitoring: Until patched, carefully monitor system logs and the FileCatalyst server for any signs of intrusion or suspicious file uploads.
- Review Incident Response: Ensure your organization has a robust incident response plan in case of a breach.