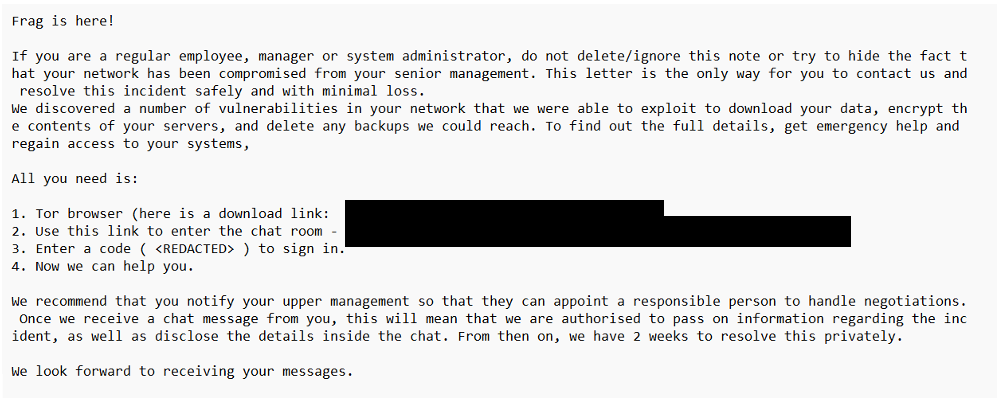
The Frag ransom note | Image: Sophos
Sophos X-Ops recently uncovered Frag ransomware in a series of cyberattacks exploiting a vulnerability in Veeam backup servers, designated CVE-2024-40711. This newly observed ransomware, deployed by a threat group Sophos tracks as STAC 5881, follows a familiar playbook but introduces some novel tactics. In previous incidents, this threat group had used other ransomware strains, such as Akira and Fog, but Frag marks a unique addition to their arsenal.
Frag ransomware is command-line-driven, with attackers specifying parameters to control the percentage of each file to be encrypted. This flexibility allows selective encryption, possibly to evade detection or prolong the victim’s attempt to recover files. A Sophos X-Ops researcher notes that “Frag is executed on the command line with a number of parameters, with one required: percentage of file encryption.”
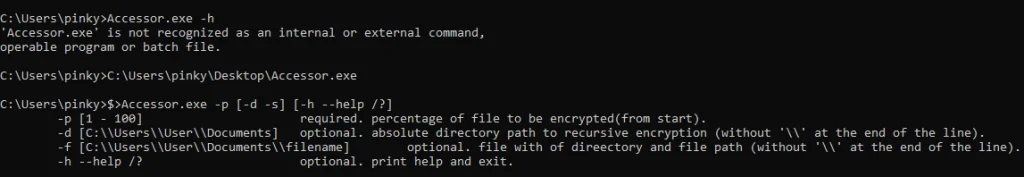
After encryption, files are renamed with a .frag extension. This ransomware, like Akira, also exploits compromised VPN appliances to gain access and leverages Veeam vulnerabilities to create administrator accounts on target systems, such as “point” and, in recent cases, an additional “point2” account.
Sophos reports that Frag’s tactics mirror those seen in Akira ransomware, suggesting a possible link between the groups or shared techniques. Agger Labs has also noted these similarities, indicating that Frag might signal the rise of a new, sophisticated ransomware player. Sophos has responded by updating their CryptoGuard feature to detect and block Frag ransomware attacks proactively. “A detection for the ransomware binary has since been added,” the report confirms.
Related Posts:
- PoC Exploit Releases for Unauthenticated RCE CVE-2024-40711 in Veeam Backup & Replication
- Fog & Akira Ransomware Exploit Critical Veeam RCE Flaw CVE-2024-40711 After PoC Release
- Unpatched Vulnerabilities: Ransomware’s Favorite Entry Point
- Leaked LockBit Tools: Novice Hackers Target Vulnerabilities
- Veeam Backup & Replication Faces RCE Flaw– CVE-2024-40711 (CVSS 9.8) Allows Full System Takeover
