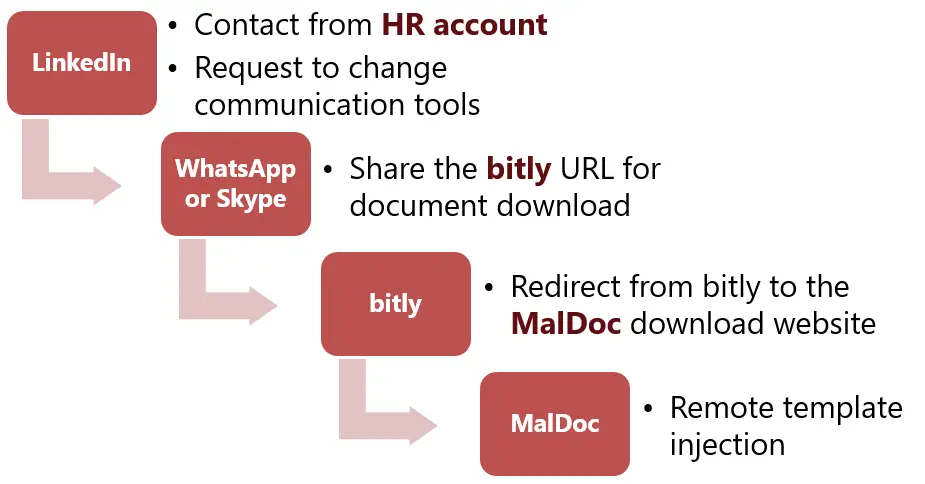
Flow of attack (Operation Dream Job) | Source: JPCERT/CC
Cybersecurity researcher Shusei Tomonaga from JPCERT/CC has issued a warning about LinkedIn being exploited as an initial infection vector by cybercriminals, particularly the Lazarus Group. Recent reports from Japan reveal unauthorized access incidents linked to fraudulent LinkedIn interactions. These attacks, ongoing since 2019, target various industries, including defense contractors and cryptocurrency exchangers, emphasizing the need for robust organizational defenses.
Tomonaga’s report highlights three key attack operations orchestrated by Lazarus Group:
- Operation Dream Job
In this campaign, attackers hijack legitimate LinkedIn accounts belonging to HR representatives of defense contractors. They approach employees under the guise of recruiters and, after transitioning the conversation to other platforms like Skype or WhatsApp, persuade their targets to download malicious Word documents. These documents, when executed, install malware on the victim’s devices.
“LinkedIn accounts exploited for the attack may not be the attackers’ but legitimate ones hijacked, and thus it is sometimes difficult to identify anything suspicious,” Tomonaga explains. - Operation Dangerous Password
Targeting cryptocurrency exchanges, this operation involves sending LinkedIn messages containing ZIP files with malicious LNK files, often disguised as Password.txt.lnk. The malware has evolved over time, now affecting not just Windows but also macOS and Linux systems. One incident involved a hijacked LinkedIn account contacting financial institutions and developers globally. - Operation AppleJeus
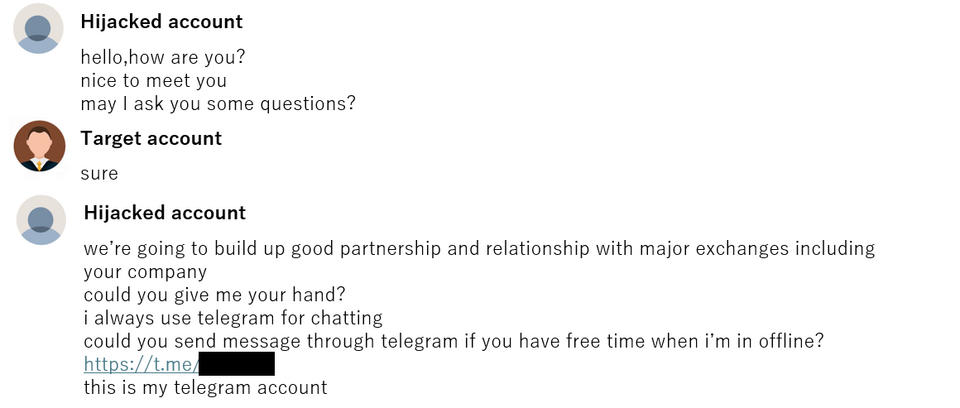
This campaign targets cryptocurrency users, redirecting LinkedIn conversations to Telegram, where victims are tricked into downloading MSI files masquerading as cryptocurrency exchange tools. Once executed, these files install malware to compromise the user’s system.
Tomonaga outlines distinct characteristics of LinkedIn-based attacks:
- Requests to switch communication platforms from LinkedIn to Skype, WhatsApp, or Telegram.
- Persistent follow-ups about downloading and executing files.
- Use of hijacked LinkedIn accounts that appear legitimate at first glance.
- Communication often in English, with occasional Japanese-language messages for local targets.
These attacks underline the dangers of using social media platforms like LinkedIn for business on corporate devices. “Past incident cases suggest that using LinkedIn on a host for business is highly dangerous and should be avoided unless there is any special reason,” the report warns. Organizations are urged to restrict SNS use on work devices, prohibit unauthorized applications, and establish clear policies to protect employees.
Related Posts:
- Iranian “Dream Job” Campaign Targets Aerospace Industry with SnailResin Malware
- Hacker Leaks LinkedIn Database Containing 35 Million User Records
- Beware of LinkedIn: Ducktail Malware’s Sneaky ZIP Attack Revealed