From SideCopy to Transparent Tribe: Pakistan APTs Hit Indian Government With RATs
A new report by Seqrite Labs reveals an alarming escalation in cyberattacks against Indian government entities by Pakistani Advanced Persistent Threats (APTs). The report highlights a coordinated campaign waged by the notorious SideCopy and Transparent Tribe (APT36) groups, demonstrating a deepening of ties between these state-backed hackers.
Seqrite Labs identified three separate campaigns over the past few weeks involving the deployment of the AllaKore RAT by the SideCopy group. Transparent Tribe concurrently used the Crimson RAT, employing both encoded and packed versions to elude detection. These revelations not only underscore the intensifying cyber espionage activities but also demonstrate the advanced technical capabilities of these threat actors.
Technical Breakdown of the Attacks

Attack Chain of SideCopy
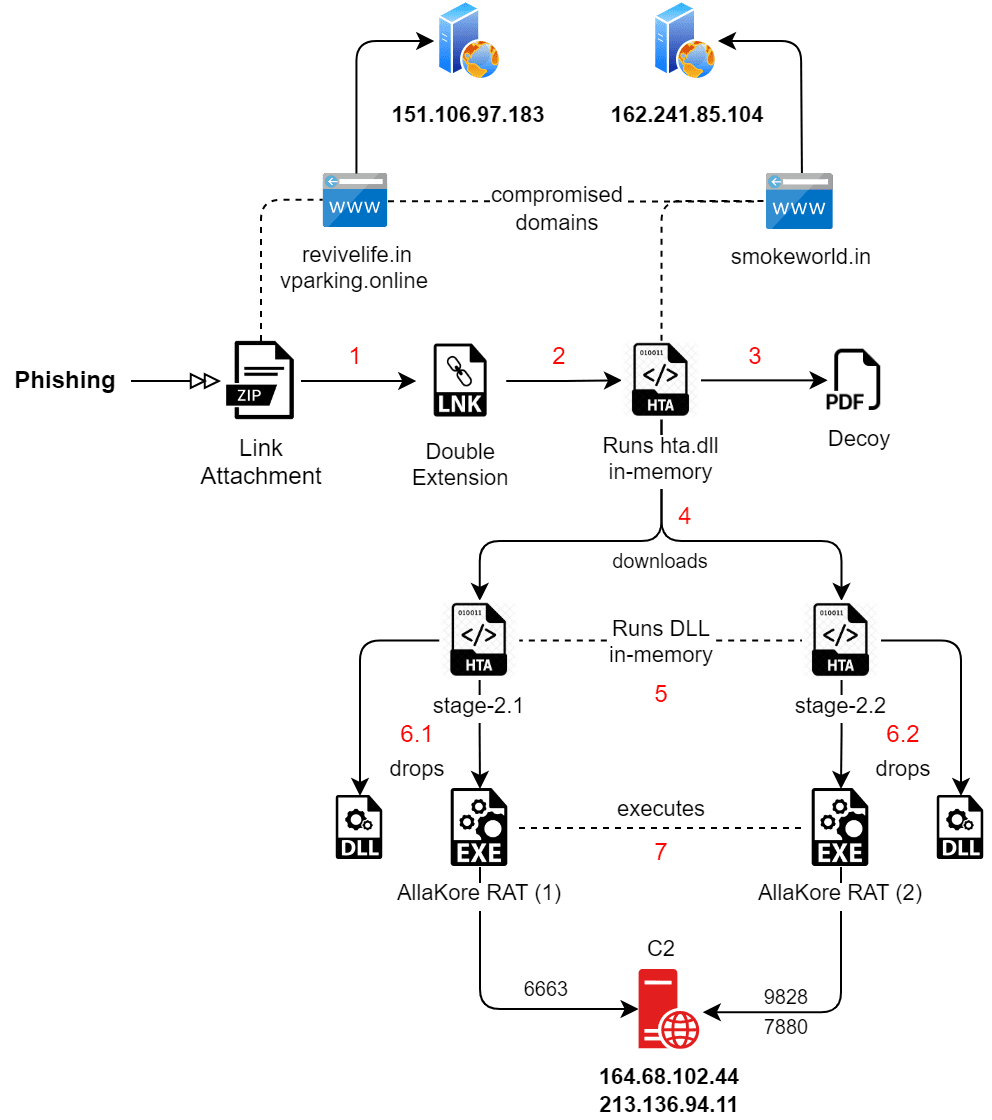
Infection Process
The campaigns typically initiated with spear-phishing emails containing a malicious LNK file, which upon execution, would contact a compromised domain to download further malicious payloads. This multi-stage infection process included the use of in-memory execution of DLLs, evasion techniques like base64 encoding, and the deployment of two RATs simultaneously, enhancing their capabilities to spy, exfiltrate data, and maintain persistence on the infected systems.
AllaKore RAT Deployment
Seqrite Labs noted that each of the AllaKore RAT deployments involved two variants operating simultaneously, communicating with C2 servers via different ports but with the same IP address. This coordination suggests a well-orchestrated approach to maximize the impact of the attack, allowing for comprehensive control and surveillance capabilities.
Attribution and Connections
Through meticulous analysis of the C2 infrastructure and previous attack patterns, Seqrite Labs has reinforced the connection between SideCopy and Transparent Tribe, confirming the subdivisional relationship between these groups. This detailed attribution helps in understanding the evolving tactics and shared methodologies among these groups, reflecting a deep-rooted cyber espionage agenda against Indian targets.
Broader Implications
The findings by Seqrite Labs reveal not only the sophistication and persistence of these threat actors but also highlight the broader implications for national security. With India being one of the most targeted nations in the cyber threat landscape, the activities of groups like SideCopy and Transparent Tribe pose significant challenges to the cybersecurity defenses of the country.
Cyberwarfare: The New Frontier of India-Pakistan Rivalry
The surge in cyberattacks against India underscores the deepening rivalry between India and Pakistan. Traditional battlefields are becoming too risky, prompting state actors to seek an edge in cyberspace. Attacks like those uncovered by Seqrite serve multiple purposes:
- Intelligence Gathering: Stealing sensitive government data can provide strategic advantages and inform military planning.
- Disruption and Sabotage: APTs can cripple critical infrastructure, sow confusion, and undermine India’s economic growth.
- Psychological Warfare: High-profile breaches and data leaks erode public trust in the government’s ability to protect its citizens.
Conclusion
The continuous advancements in the cyber capabilities of Pakistani APT groups targeting India are alarming. As Seqrite Labs continues to monitor these activities, the need for heightened cybersecurity awareness and robust defensive strategies becomes increasingly critical. The report serves as a stark reminder of the persistent threats and the need for continuous vigilance and improvement in cybersecurity postures by government and defense entities in India.





