In June 2021, the cybersecurity landscape witnessed the emergence of a formidable player: Rimasuta botnet. It’s named after its unique usage of the TEA algorithm and has recently resurfaced in botnet observations. Initially discovered by 360netlab and analyzed by QAX’s XLab, this malware represents an evolution in the notorious Mirai botnet family.
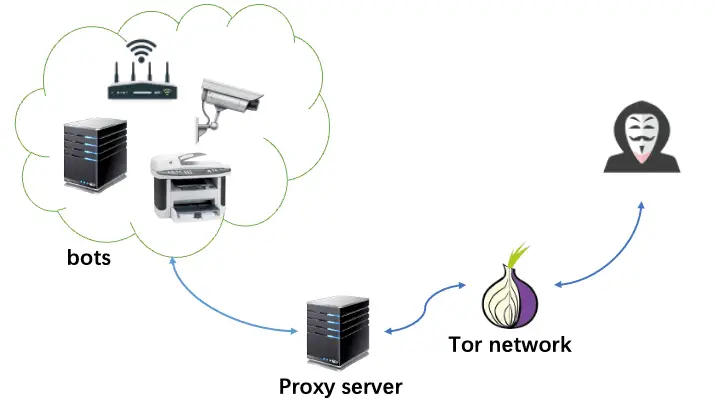
Rimasuta retains its original architecture, including Tor Proxy for communication, but has evolved in terms of encryption algorithms and protocol formats. It uses a distinct propagation method, exploiting a specific vulnerability named “NCVE_2022_03_03_RMT_saveddns.” The malware has undergone significant code structure and functionality changes, including a redesigned encryption algorithm and Command and Control (C2) communication protocol.

Rimasuta stands out due to significant alterations in its code structure and functionality. It has transitioned from the TEA algorithm to ChaCha20, enhancing its encryption capabilities. This malware cleverly navigates network defenses, exploiting vulnerabilities and adopting unique propagation methods.
At its core, the Rimasuta botnet is designed to infiltrate systems and evade detection. It employs advanced data encryption and communication techniques, making it a formidable threat to cybersecurity defenses. XLab’s analysis sheds light on the intricate workings of this malware, from its command and control protocols to its utilization of the STUN protocol for information collection.
Rimasuta’s resurgence signifies a continuous threat in the cybersecurity realm. Its ability to adapt and evolve makes it particularly dangerous. However, users can detect potential infections by monitoring network traffic and analyzing data for specific indicators linked to Rimasuta’s activities.
Rimasuta is not just malware; it’s a wake-up call for the cybersecurity community. Its evolution and sophistication highlight the need for advanced defensive strategies and continuous vigilance in cybersecurity.