Check Point Research has identified the misuse of the Godot game engine—a popular, open-source tool for game development—as a platform for distributing malware. Dubbed GodLoader, this novel technique highlights how cybercriminals exploit legitimate software to evade detection and spread malicious payloads across multiple platforms.
Godot Engine, known for its versatility and widespread use in game development, provides a platform-agnostic environment that supports exports to Windows, macOS, Linux, Android, iOS, and more. Unfortunately, these same features have made it an attractive target for attackers. “Threat actors take advantage of Godot engine and GDScript, which use this new technique to execute malicious code, download malware, and deploy it while remaining undetected,” Check Point noted in its report.
GodLoader leverages Godot’s .pck files—used to bundle game assets like scripts, textures, and sounds—to introduce malicious GDScript code. The technique capitalizes on Godot’s ability to load these files dynamically, which can include updates or downloadable content. Attackers craft these files to include malicious scripts that trigger harmful actions upon execution.
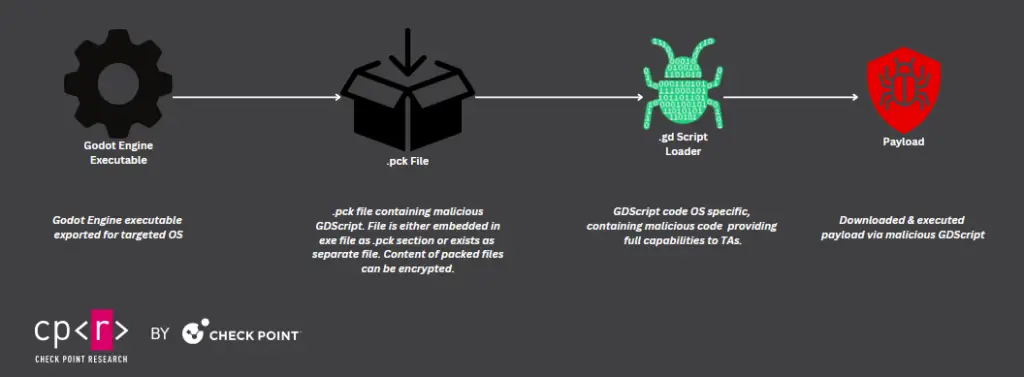
The report explains, “The Pack file could be transported separately or in sections inside the executable. While the main evolution of malicious code happens within the .pck file, in later stages, the actor also attempted to improve the evasion level and encrypt the .pck file”
GodLoader is distributed through the Stargazers Ghost Network, a GitHub-based malware-as-a-service operation. Over 200 repositories have been identified as part of the campaign, which began in June 2024. These repositories are designed to look legitimate, bolstered by “stargazers” and GitHub bots that enhance their visibility. This deceptive strategy has infected over 17,000 systems.
One of the most concerning aspects of GodLoader is its cross-platform reach. While initially targeting Windows, Check Point researchers demonstrated proof-of-concept attacks on macOS and Linux. They noted that “This new technique allows threat actors to target and infect devices across multiple platforms, such as Windows, macOS, Linux, Android, and iOS. “
Examples include scripts that evade sandboxes and deploy payloads:
- Linux Payloads: Download and execute scripts using the system’s
wgetandchmodtools. - macOS Payloads: Similar methods using system commands to deploy and run payloads, such as opening the Calculator app in demos.
Looking ahead, attackers might extend their focus to legitimate Godot-developed games. By replacing .pck files or injecting malicious scripts into legitimate games, attackers could exploit the trust built around the Godot engine. “Potentially, an ‘infector’ could replace the .pck section contents with the malicious file,” warned the researchers.
Related Posts:
- Beware of Search Results: Hackers Using Fake Websites to Spread Malware
- Hackers Exploit YouTube for Game Cracks, Steal Your Data
- Attackers Leveraging Public Cobalt Strike Profiles to Evade Detection