Golden GMSA
GoldenGMSA is a C# tool for abusing Group Managed Service Accounts (gMSA) in Active Directory.

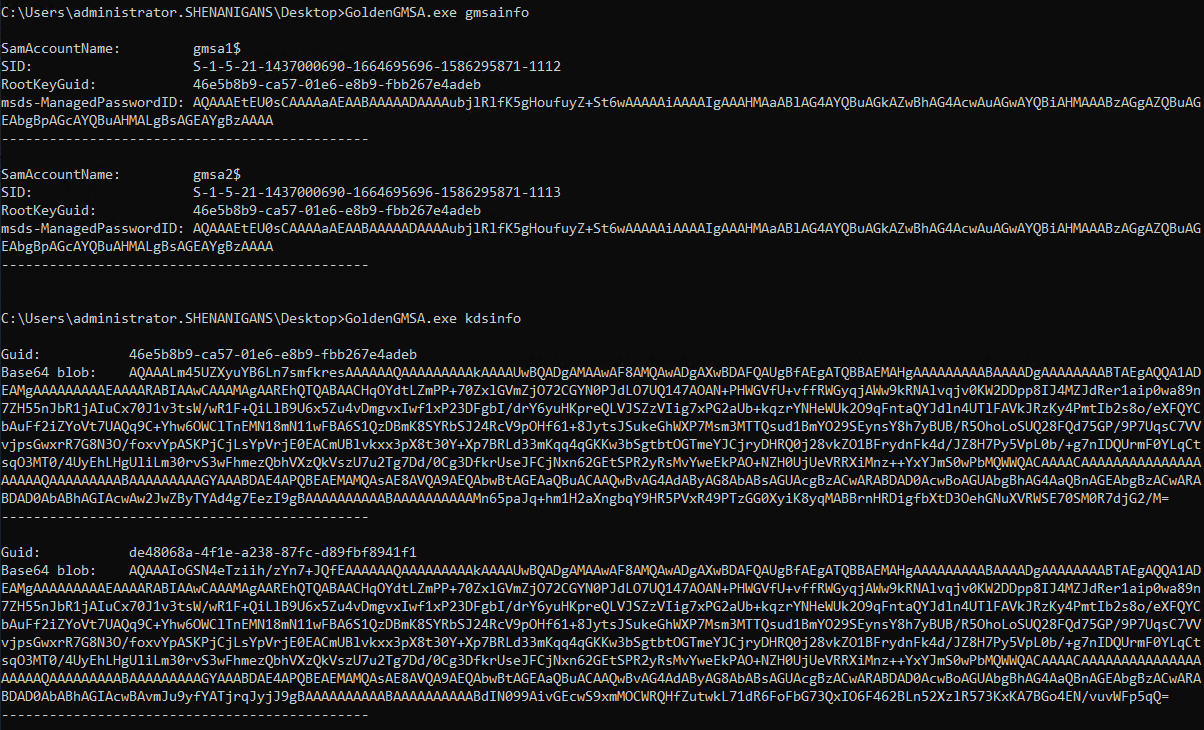
The Golden GMSA attack occurs when an attacker dumps a KDS root key’s relevant attributes and then uses them to generate the password for associated gMSA accounts offline. The Golden GMSA attack is somewhat similar to the Golden Ticket attack, which allows attackers who compromise the krbtgt account to forge Ticket Granting Tickets (TGTs) as long as the krbtgt password remains unchanged.
One notable difference between a Golden Ticket attack and the Golden GMSA attack is that we are not aware of a way of rotating the KDS root key secret. Therefore, if a KDS root key is compromised, there is no way to protect the gMSAs associated with it. The only mitigation in such a scenario is to create new gMSAs with a new KDS root key.
The GoldenGMSA Attack tool can retrieve the necessary attributes from a specified KDS root key object or use values provided by the user to generate a GKE. The tool can also retrieve the msDS-ManagedPasswordID based on a gMSA SID and, of course, generate the gMSA’s password offline.
An attacker can potentially use the password to compromise services that use the gMSA by forging a Silver Ticket or obtaining a Kerberos service ticket for privileged accounts through S4U2Self. If the gMSA has high privileges, the attacker might use it to compromise other resources and, in some cases, compromise the entire forest.
More details are available at the post Introducing the Golden GMSA Attack.
Download & Use
Copyright (c) 2022 Semperis, Inc