Image Credit: Germán Fernández
A sophisticated cyberattack targeting the government sector has been uncovered, utilizing a quartet of malicious software – XWorm, AsyncRAT, VenomRAT, and PureLogs Stealer – and exploiting Cloudflare’s TryCloudflare service.
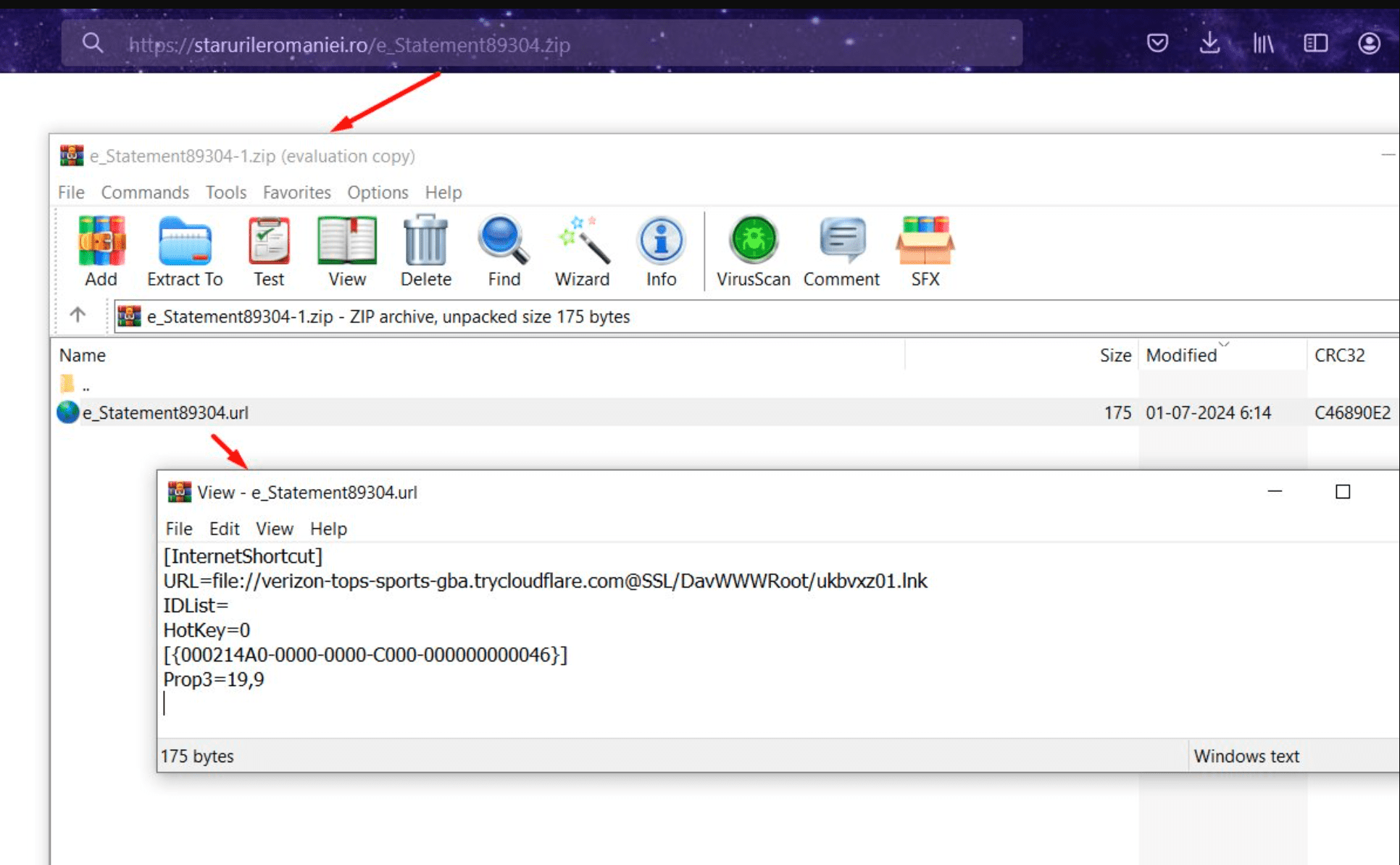
eSentire’s Threat Response Unit (TRU) detected the attack in July 2024, which began with a phishing email containing a malicious URL shortcut leading to a WebDAV server hosted on TryCloudflare. This server was used to distribute encrypted payloads, including obfuscated batch files and Python scripts, to the victim’s machine.
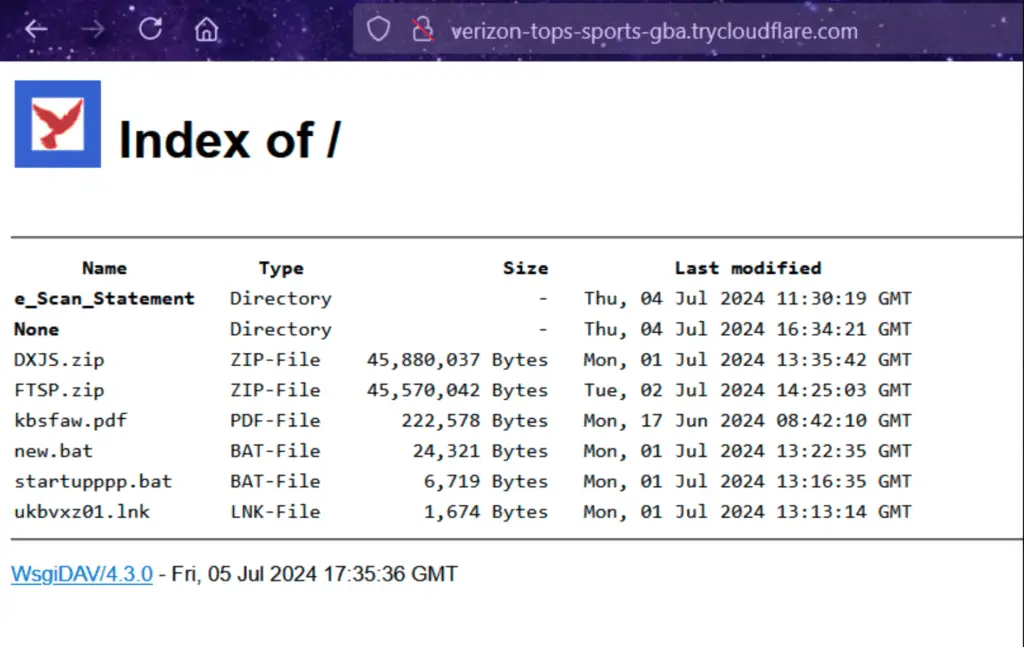
The attackers utilized the Web Distributed Authoring and Versioning (WebDAV) protocol, an ideal method for managing files on remote servers, thus facilitating the hosting and distribution of malicious files. They exploited TryCloudflare, a free service from Cloudflare intended for web development and testing, which proxies local machines through Cloudflare’s infrastructure, generating random subdomains under trycloudflare.com for internet accessibility.
The initial infection vector was a phishing email, a common yet highly effective method for breaching security. The targeted user received a ZIP archive containing a URL shortcut, leading to a .lnk shortcut file hosted on a TryCloudflare-proxied WebDAV server. This file initiated the execution of obfuscated batch files, which subsequently retrieved and executed additional Python payloads.
Upon execution, the shortcut file triggered the new.bat batch file, obfuscated with a substitution cipher and UTF-16LE encoding to evade detection. This batch file performed several actions:
- Launching a decoy PDF file hosted on the WebDAV server.
- Downloading ZIP archives from the WebDAV server using PowerShell and extracting them to the “Downloads” folder.
- Hiding the extracted Python and Print folders.
- Downloading and moving the startuppppp.bat file to the Startup Folder.
- Executing multiple malicious Python files, including moment.py, update.py, upload.py, time.py, and kamp.py.
The batch files and Python scripts were highly obfuscated, employing base64 encoding and RC4 encryption. The decrypted shellcode executed in memory, utilizing the Donut loader and Chaskey cipher for further payload decryption. The shellcode used direct syscalls to evade Endpoint Detection and Response (EDR) systems, injecting the final payload into the notepad.exe process via Early Bird APC Queue Code Injection.
The attack culminated in the deployment of XWorm, VenomRAT, AsyncRAT, and PureLogs Stealer. These malware strains enabled the attackers to:
- Log keystrokes and steal sensitive information.
- Capture screenshots and record the screen.
- Execute remote commands and control the infected devices.
- Exfiltrate data stealthily to avoid detection.
The threat actors employed sophisticated evasion techniques, including direct syscalls and obfuscation, to bypass security measures. They also implemented mechanisms to maintain persistence on infected devices, such as altering file attributes and using accessibility features to prevent users from accessing settings or antivirus applications.
The combination of XWorm, AsyncRAT, VenomRAT, and PureLogs Stealer, coupled with advanced obfuscation and evasion tactics, highlights the need for robust cybersecurity measures and vigilant monitoring to protect against such sophisticated threats. As the cyber threat landscape continues to evolve, organizations must remain proactive in identifying and mitigating emerging threats to safeguard their digital assets and sensitive information.