Hide’N Seek Botnet is Targeting Smart Home Devices
The Hide’N Seek botnet was first discovered in January this year, with initial targets for home routers and IP cameras, and a decentralised peer-to-peer architecture. As of May, this botnet has infected more than 90,000 IoT devices and is starting to target more device types and architectures.
Earlier this month, researchers at Qihoo 360 NetLab revealed that the botnet’s attack targets also covered AVTECH webcam and Cisco Linksys routers as well as OrientDB and CouchDB database servers and added a CPU mining program, but This feature was not enabled at the time.
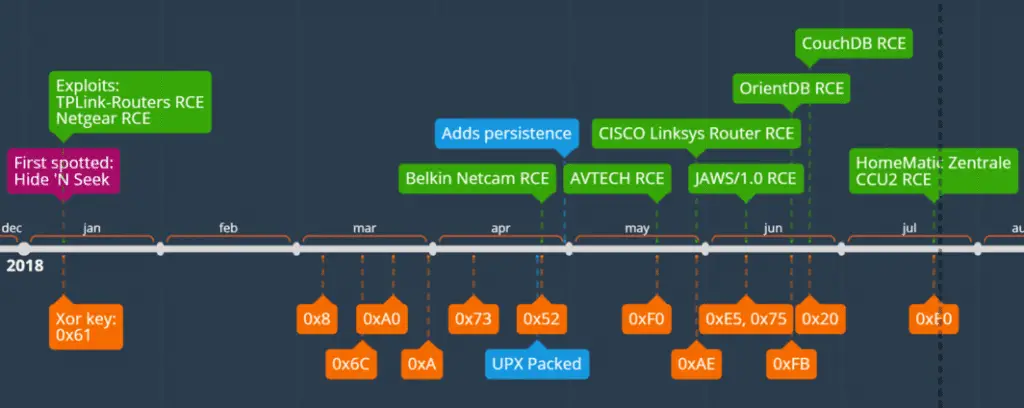
The latest report from Fortinet states that they have recently captured three new samples of HNS bots. The first sample configuration has 60 entries, including two exploits; the second sample has 81 entries and six exploits; and the third, and most recent, the sample has 110 entries and nine exploits. The vulnerabilities that have exploited so far are as follows:
| Exploit | Poc Published date |
| TP-Link Routers RCE | 2013-03-12 |
| Netgear DGN1000 RCE | 2017-10-25 |
| Belkin NetCam RCE | 2017-07-17 |
| AVTECH IP Camera/NVR/DVR RCE | 2016-10-11 |
| CISCO Linksys Router RCE | 2014-02-16 |
| JAWS/1.0 RCE | 2016-02-10 |
| OrientDB RCE | 2017-10-09 |
| Apache CouchDB RCE | 2018-06-20 |
| HomeMatic Zentrale CCU2 RCE | 2018-07-18 |
More importantly, Fortinet security researchers also revealed that HNS has now added remote code execution vulnerabilities to HomeMatic Zentrale CCU2, Apache CouchDB remote code execution vulnerabilities, and remote code execution vulnerabilities in Belkin NetCam devices. Use.
The HomeMatic German manufacturer eQ-3 is a smart home equipment supplier, while the HomeMatic Zentrale CCU2 is the heart of the HomeMatic system, offering a wide range of control, monitoring and configuration options for all HomeMatic devices. This means that if a bot compromises the HomeMatic Zentrale CCU2, the victim may lose control of the entire smart home device.
Source, Image: Fortinet