Host Scanner: Active/passive network scanner and autonomous vulnerability assessment application
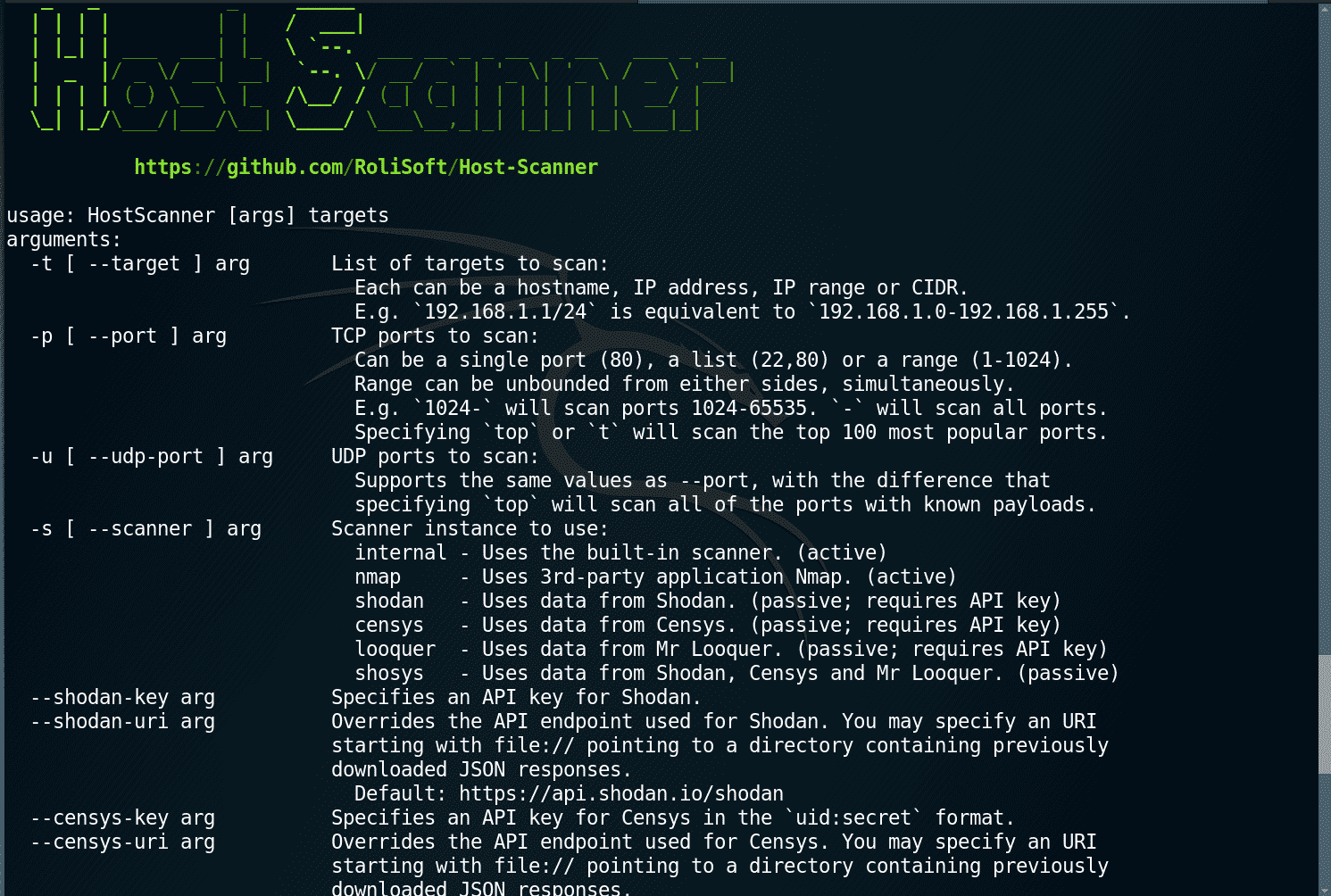
Host Scanner
The purpose of this project is to implement a network scanner with both active and passive data acquisition components, which can then autonomously identify services using the latest CPE dictionary from NIST and discover the vulnerabilities of those by querying the CVE database.

Features
- TCP Scanner
- High-performance TCP scanner which initiates the three-way handshake (also called “TCP connect scan”) by multiplexing non-blocking sockets and grabbing their service banners.
- UDP Scanner
- Makes use of a database of specifically crafted payloads mapped to port numbers in order to try and get an answer from the UDP services, if there are any listening.
- ICMP Pinger
- Support for the use of ICMP Echo Request packets (also known as “standard ping”) in order to determine if a host is alive.
- ARP Pinger
- Support for the use of ARP Who-Has Request packets in order to map online hosts on a local network. Useful when ICMP packets are filtered on a network.
- External Scanners
- Ability to use external tools for all the active or passive scanning needs, instead of the built-in scanners:
- Launch new scans with or process earlier XML outputs from Nmap.
- Ability to use external tools for all the active or passive scanning needs, instead of the built-in scanners:
- Online Sources
- Support for passive reconnaissance by fetching data already available from relevant services intended for security researchers:
- Shodan
- Censys
- Mr Looquer
- Support for passive reconnaissance by fetching data already available from relevant services intended for security researchers:
- Service Identification
- Autonomous Identification:
- Latest CPE dictionary from NIST is used to map service banners to their CPE names.
- Pattern-based Identification:
- Database of regular expressions can be used as a redundancy to map service banners to their CPE names.
- Autonomous Identification:
- Vulnerability Assessment
- Based on the CVE database, the resolved CPE names (which also include version numbers) are matched against the affected software list of each CVE entry to discover service vulnerabilities.
- Package Lookup
- Resolve CPE names to actual operating system packages and get a simple command to update only the vulnerable versions for:
- Debian (oldstable to unstable), Ubuntu (all current and lts versions)
- Red Hat (5-7), CentOS (5-7), Fedora (all current and rawhide)
- Resolve CPE names to actual operating system packages and get a simple command to update only the vulnerable versions for:
- Vulnerability Validation
- Use the package manager, security or bug tracker of the identified distribution to check whether a package is vulnerable, whether a vendor patch is available, and whether it is installed or not.
- Estimate System Upgrade Date
- Using the changelog of the discovered packages with version numbers and security patch information, estimate the date range of the last system upgrade of the host.
- Reporting
- Generate a LATEX report of the scanned network, which includes open ports, identified services, discovered vulnerabilities and mitigation recommendations.
- Unit Tests
- All features are covered by unit tests which are run on three platforms in order to ensure utmost stability and portability.
- Portability
- Features are implemented (when a standardized API is not available) using raw sockets on Linux, WinPcap on Windows, and Berkeley Packet Filter on BSD / OS X.
Building
To compile and run the application, you must first install the dependencies, which can be done with:
- Debian/Ubuntu/Kali:
apt install build-essential cmake libcurl4-openssl-dev libsqlite3-dev libboost-all-dev libz-dev - RHEL/CentOS/Fedora:
yum install gcc-c++ make cmake libcurl-devel sqlite-devel boost-devel-static zlib-devel - FreeBSD:
pkg install cmake curl sqlite3 boost-libs - Mac OS X: (with Homebrew)
xcode-select --install && brew install cmake curl sqlite boost - Windows or any of the above platforms if problems arise with the vendor packages: (with Conan)
conan install --build=missingWhen executed in the project root, downloads and/or builds all required dependencies for the project and generates a
conanbuildinfo.cmakefile, which when exists, will be used byCMakeLists.txtto configure include directories and link targets.
After the dependencies have been installed, you can check out the repository and compile it with the following commands:
git clone https://github.com/RoliSoft/Host-Scanner.git cd Host-Scanner/build cmake .. make
If the compilation was successful, you can run it with the ./HostScanner command. Tests are also available, you may run them through make test or directly, by executing ./TestScanner.
Usage
Examples
Scan a network for vulnerabilities on the top 100 TCP ports and known UDP ports using the internal scanners:
./HostScanner -p t -u t 192.168.1.0/24
Scan an IP address or netblock for vulnerabilities passively, with data from Shodan, Censys and Mr Looquer:
./HostScanner -x 178.62.192.0/18
Perform service identification and vulnerability analysis on an earlier XML output of nmap through nmap -oX report.xml …:
./HostScanner -s nmap -f report.xml
Get list of vulnerable packages and command to upgrade it on the host:
./HostScanner -r 192.168.1.66 192.168.1.71
The above will scan the TCP ports of the specified addresses, perform operating system and service detection followed by vulnerability analysis, and lookup the packages needed to be updated for the discovered CVEs to be mitigated:
[*] 192.168.1.66 is running cpe:/o:debian:debian_linux:8
[*] 192.168.1.71 is running cpe:/o:redhat:enterprise_linux:7
...
[*] 192.168.1.66 -> sudo apt-get install --only-upgrade apache2 php5 python2.7
[*] 192.168.1.71 -> sudo yum update httpd php python27-python
Copyright (c) 2016 RoliSoft <root@rolisoft.net>
Source: https://github.com/RoliSoft/





