ibombshell – Dynamic Remote Shell
ibombshell is a tool written in Powershell that allows you to have a prompt at any time with post-exploitation functionalities (and in some cases exploitation). It is a shell that is downloaded directly to memory providing access to a large number of pentesting features. These functionalities can be downloaded directly to memory, in the form of a Powershell function. This form of execution is known as everywhere.
In addition, it provides a second execution mode called Silently, so the pentester can execute an instance of ibombshell (called warrior). The compromised computer will be connected to a C2 panel through HTTP. Therefore, it will be possible to control the warrior and be able to load functions in memory that help the pentester. This is happening within the post-exploitation phase.
ibombshell C2 scheme
Install
https://github.com/ElevenPaths/ibombshell.git cd ibombshell\ c2/ pip install -r requirements.txt
Usage
ibombshell has two execution modes:
-
ibombshell everywhere
To load ibombshell simply run on PowerShell:
Now you can run the downloaded ibombshell console running: console
-
ibombshell silently mode
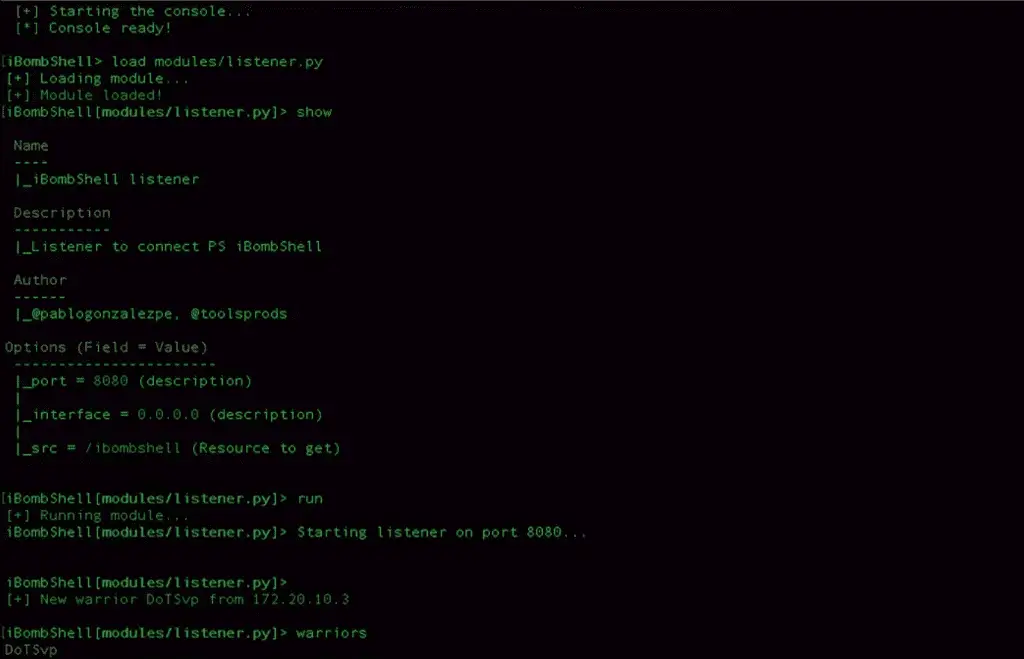
This version allows you to run the ibombshell console and remotely control it from the C2 panel created in python. To run this version, first you must launch the console process in PowerShell:
On ibombshell C2 path, prepare the C2:
And create the listener where the warriors will be connected:
The default listener port is 8080. Finally, you can launch the console in silently mode on the host to get remote control:
Example
- PoC Warrior + Bypass UAC + Pass the hash
- macOS
- Extracting Private SSH Keys on Windows 10
- PoC savefunctions
Author: ElevenPaths
Source: https://github.com/ElevenPaths/