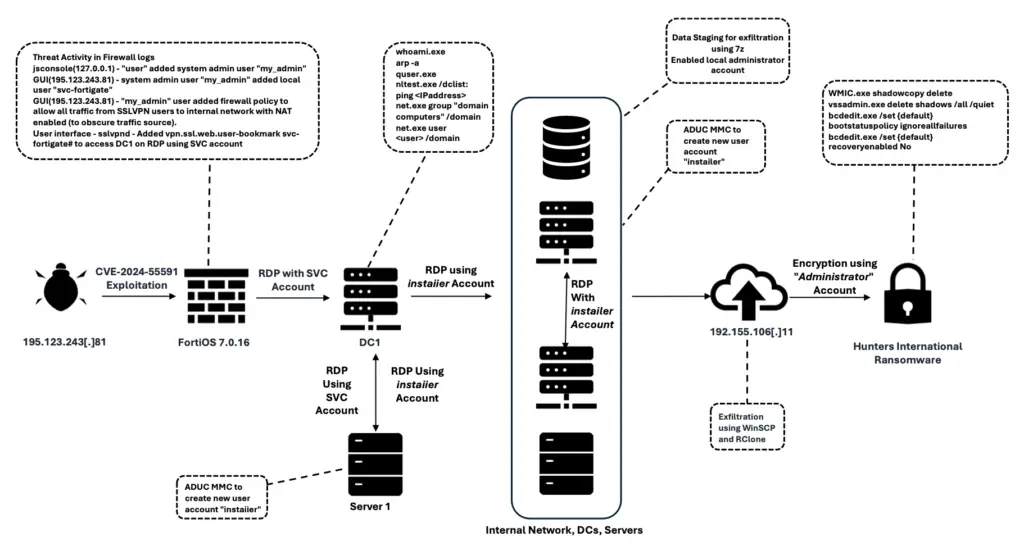
Attack Flow Diagram | Image: TRU
In the dynamic realm of cybercrime, ransomware groups continuously evolve their tactics, techniques, and procedures (TTPs) to maximize impact and financial gain.
In February 2025, the eSentire Threat Response Unit (TRU) documented a sophisticated ransomware campaign launched by Hunters International ransomware group against a retail organization, highlighting how quickly a breach can escalate when the right vulnerabilities meet the wrong hands.
The Hunters International group — suspected to be a spinoff of the now-defunct Hive ransomware — gained access by abusing CVE-2024-55591, an authentication bypass vulnerability in FortiOS and FortiProxy.
“Initial access to the environment was achieved via exploitation of CVE-2024-55591 against a vulnerable Fortinet device.”
Once inside, the attackers created a super admin account named my_admin and began laying the groundwork for lateral movement.
The attack infrastructure included VPN access via VPN Jantit, which allowed remote connectivity using the newly created admin account. This account was used to create svc-fortigate, a user granted broad network access via custom firewall rules.
These changes were consistent with tactics seen in Fortinet’s own threat advisories, confirming how attackers mirrored known Fortinet misconfigurations to expand their reach.
The attackers ran several commands to map the environment:
- nltest /dclist: – Find domain controllers
- net group “domain admins” – List privileged accounts
- whoami, ipconfig, arp -a – Fingerprint the system
They also created deceptive user accounts named InstaIIer and Instailer (note the use of uppercase “I” to mimic lowercase “l”), and re-enabled the built-in Administrator account to ensure persistent access.
With a path mapped, the attackers exfiltrated sensitive data using Rclone and later WinSCP. The command lines show efficiency and precision:
“Looking to exfiltrate files and deploy ransomware as soon as possible, specific arguments were passed to RClone… setting the max bandwidth to 200 MiB/s.”
When Rclone failed, they downloaded WinSCP from the official site and leveraged custom PowerShell scripts to automate data transfers — scripts that eSentire suspects may have been generated using AI tooling due to their structure and logic.
Once data was in their hands, Hunters International deployed their Rust-based ransomware payload, initially using encrypter_windows_x64.exe. But when this binary was quarantined by endpoint detection systems, they pivoted to a stealthier DLL version: encrypter_windows_x64.dll.
“Unlike previous variants, this variant does not leave ransom notes, nor does it append a file extension to encrypted files.”
The ransomware was launched using rundll32.exe with arguments that impersonated domain administrators and killed specific processes before encrypting files. The ransomware used AES-256 CTR mode for encryption, with each file receiving a uniquely generated key and counter via BCryptRandom.
The attackers made sure that recovery was near impossible. They issued commands to:
- Delete Volume Shadow Copies using vssadmin.exe and wmic.exe
- Remove system state backups via wbadmin.exe
- Disable recovery mode with bcdedit.exe
This ensured that traditional system recovery options were rendered useless — a hallmark of today’s most aggressive ransomware strains.
Hunters International operates a dark web extortion site where exfiltrated data is posted if victims refuse to pay. As of the time of the report:
“263 organizations have been affected so far.”
This double-extortion model not only encrypts critical data but also threatens to expose it — amplifying pressure on victims.